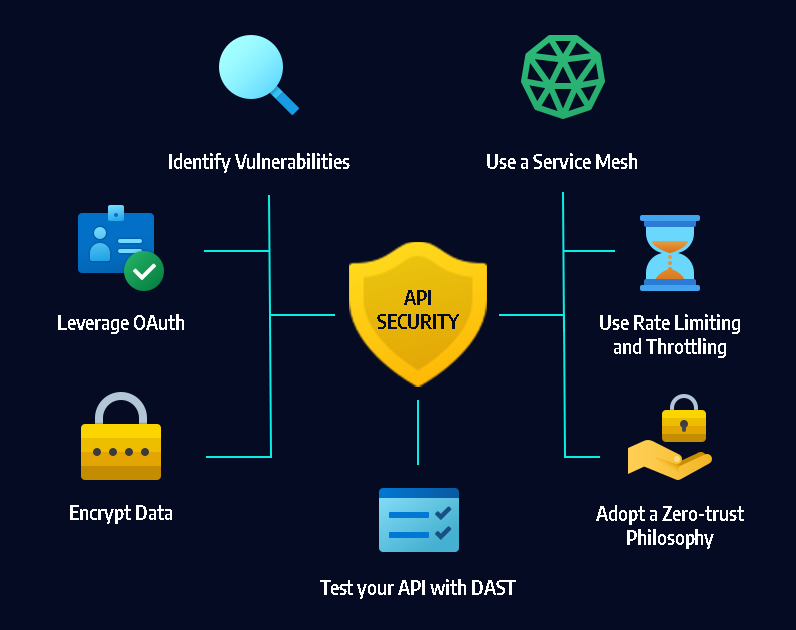
In an era of increasing cyber threats and evolving attack techniques, organizations worldwide are adopting proactive measures to secure their digital assets. Penetration testing, commonly known as ethical hacking, has emerged as a popular strategy for identifying vulnerabilities and strengthening the overall security posture.
This article aims to provide a comprehensive overview of the advantages and disadvantages associated with penetration testing. By examining both sides of the coin, readers will gain insights into the benefits of this practice as well as its limitations, enabling them to make informed decisions about integrating it into their cybersecurity strategies.
Advantages of Penetration Testing
Identifying Vulnerabilities:
One of the primary benefits of penetration testing is its ability to uncover vulnerabilities that may exist within an organization's network, applications, or systems. By simulating real-world attack scenarios, ethical hackers can identify security weaknesses that could be exploited by malicious actors. This knowledge empowers organizations to address these vulnerabilities proactively, significantly reducing the likelihood of successful cyberattacks.
Enhanced Security Awareness:
Penetration testing not only identifies technical vulnerabilities but also raises security awareness among employees. By demonstrating how attackers exploit weaknesses, organizations can educate their workforce about potential threats and promote a culture of cybersecurity. This increased awareness encourages employees to adopt best practices, such as creating strong passwords, being cautious with email attachments, and reporting suspicious activities promptly.
Cost-Effective Risk Mitigation:
While penetration testing requires an investment, it is often more cost-effective than the consequences of a successful cyberattack. By proactively identifying and fixing vulnerabilities, organizations can mitigate the risk of potential data breaches, financial losses, reputational damage, and legal implications. This approach saves substantial resources that would otherwise be required for incident response, recovery, and regulatory compliance in the aftermath of an attack.
Compliance and Regulatory Requirements:
Many industries are subject to strict compliance standards and regulatory requirements concerning the protection of sensitive data. Penetration testing helps organizations meet these obligations by identifying vulnerabilities and ensuring appropriate security measures are in place. Regular penetration testing demonstrates due diligence in maintaining a secure environment and can help organizations avoid penalties, legal consequences, and reputational harm associated with non-compliance.
Enhanced Incident Response:
By proactively identifying vulnerabilities, organizations can strengthen their incident response capabilities. Penetration testing provides valuable insights into potential attack vectors and how they can be mitigated. With this knowledge, organizations can develop robust incident response plans, ensuring a rapid and effective response in the event of a breach. This proactive approach reduces downtime, minimizes the impact on business operations, and facilitates a quicker return to normalcy.
Disadvantages of Penetration Testing
Limitations in Scope:
While penetration testing is a valuable tool, it has limitations in terms of scope. The effectiveness of testing largely depends on the skills and experience of the ethical hacker conducting the assessment. If an ethical hacker fails to identify a vulnerability or explores a limited range of attack vectors, the assessment may provide a false sense of security. To address this limitation, organizations should engage reputable penetration testing providers with extensive experience and expertise.
Disruption of Business Operations:
Penetration testing involves simulated attacks on an organization's systems, which can disrupt normal business operations. Testing activities, such as network scans, vulnerability assessments, and exploitation attempts, may cause temporary service disruptions or impact system performance. Organizations need to plan and schedule penetration testing carefully to minimize any potential disruptions and ensure they align with critical business processes.
False Positives and Negatives:
Penetration testing may generate false positives or false negatives, impacting the accuracy of vulnerability identification. False positives occur when the assessment incorrectly identifies a vulnerability that does not exist, leading to unnecessary remediation efforts and resource wastage. False negatives, on the other hand, occur when a genuine vulnerability is missed, leaving organizations exposed to potential attacks. Regular communication and collaboration between penetration testers and organizations can help minimize false findings.
Limited Point-in-Time Assessment:
Penetration testing provides a snapshot of an organization's security posture at a specific point in time. As the threat landscape evolves rapidly, new vulnerabilities may emerge shortly after the testing is conducted. Therefore, organizations should view penetration testing as part of an ongoing cybersecurity strategy rather than a one-time solution. Continuous monitoring, regular testing, and the implementation of security patches and updates are essential to maintain a robust security posture.
Ethical and Legal Considerations
Penetration testing involves ethical hacking, which requires strict adherence to legal and ethical guidelines. Without proper authorization, conducting penetration testing can be illegal and result in severe consequences. Organizations must ensure they have written consent and agreements in place with ethical hackers to avoid legal ramifications. Additionally, it is crucial to establish clear rules of engagement and communication channels to prevent misunderstandings and potential damage during the testing process.
Conclusion
Penetration testing offers numerous advantages, including vulnerability identification, enhanced security awareness, cost-effective risk mitigation, compliance adherence, and improved incident response capabilities. However, it is essential to consider the limitations of penetration testing, such as scope restrictions, potential disruption to business operations, false positives/negatives, limited point-in-time assessment, and ethical and legal considerations. By understanding these advantages and disadvantages, organizations can make informed decisions about incorporating penetration testing into their comprehensive cybersecurity strategies, effectively safeguarding their digital assets from evolving threats.