In today's digital landscape, web applications have become an integral part of our lives. From e-commerce platforms to social media networks, these applications provide convenience and interconnectedness.
However, they also open up avenues for potential security risks. While automated security tools play a vital role in detecting vulnerabilities, there are specific types of web application vulnerabilities where human expertise shines.
In this article, we will explore these vulnerabilities and shed light on the unique advantages that humans bring to the table in the realm of web application security.
User-Interaction-Based Vulnerabilities
One area where humans excel in identifying vulnerabilities is user-interaction-based flaws. These vulnerabilities arise when an application's design or functionality allows users to perform unintended actions or access unauthorized information. Through their familiarity with user behavior and intuitive understanding of user interfaces, humans can uncover these flaws that automated tools might miss. Examples include input validation issues, insecure direct object references, and business logic flaws.
Contextual Awareness
Humans possess a remarkable ability to understand the context surrounding an application and its intended use. This contextual awareness empowers them to identify vulnerabilities that arise due to subtle nuances or ambiguities in the application's behavior. Whether it's identifying privilege escalation opportunities or recognizing subtle differences in URL structures, humans can leverage their experience and critical thinking to spot vulnerabilities that automated tools might overlook.
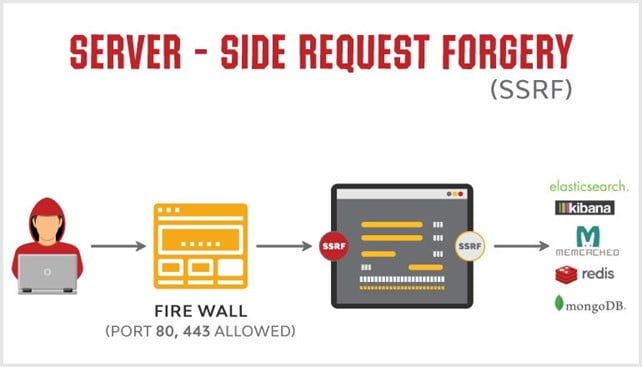
Complex Vulnerabilities
Web application vulnerabilities can be intricate and multifaceted, often requiring a deep understanding of the underlying technologies and intricate business logic. Humans, with their cognitive abilities and experience, can detect complex vulnerabilities that demand contextual understanding, advanced reconnaissance, and targeted attacks. Examples include security misconfigurations, server-side request forgery, and XML external entity (XXE) attacks.
Behavioral Analysis
Humans possess a unique advantage in analyzing human behavior and identifying anomalies or suspicious patterns that automated tools might struggle to detect. By leveraging their understanding of human psychology, social engineering techniques, and fraud detection skills, humans can uncover vulnerabilities that arise due to phishing attacks, session hijacking, or unauthorized access attempts. Their ability to think like potential attackers aids in identifying vulnerabilities that rely on manipulating user behavior.
Conclusion
While automated security tools are indispensable in ensuring the safety of web applications, humans bring a complementary set of skills and knowledge to the table.
Through user-interaction-based vulnerability discovery, contextual awareness, expertise in complex vulnerabilities, and behavioral analysis, humans play a crucial role in identifying web application vulnerabilities that are often missed by automated tools.
By harnessing the power of human intuition, expertise, and critical thinking, organizations can bolster their web application security and safeguard against ever-evolving threats in the digital landscape.