In today's technology-driven world, cybersecurity is of paramount importance for organizations of all sizes and sectors. The increasing frequency and sophistication of cyber threats necessitate the adoption of robust security measures. To help organizations navigate the complex landscape of cybersecurity, the National Institute of Standards and Technology (NIST) has developed a comprehensive Cybersecurity Framework. In this article, we will delve into the NIST Cybersecurity Framework, its components, and how it can enhance organizational security.
Understanding the NIST Cybersecurity Framework
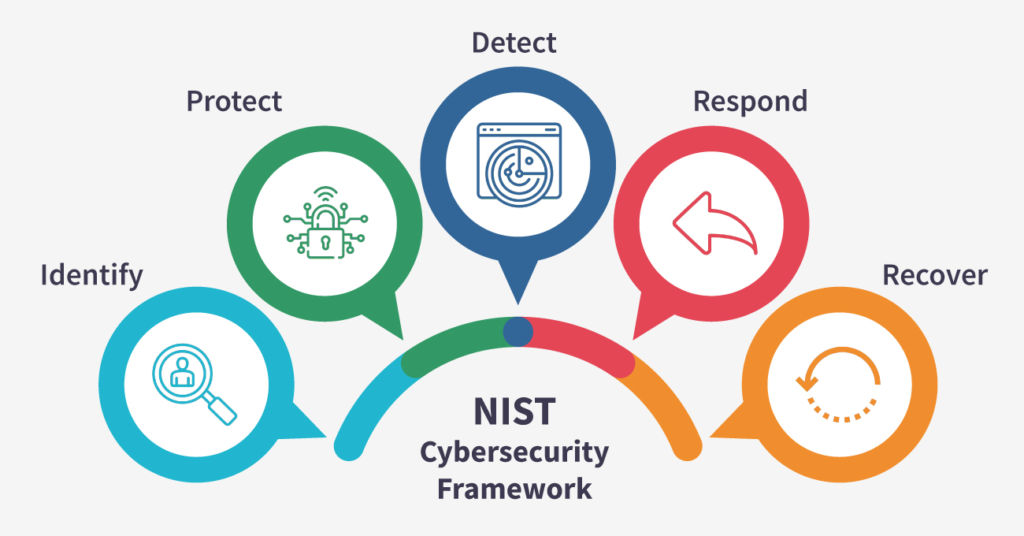
The NIST Cybersecurity Framework was first introduced in 2014 as a voluntary guideline for organizations to manage and mitigate cybersecurity risks. Since then, it has become widely recognized as a leading cybersecurity standard globally. Its primary objective is to help organizations identify, protect, detect, respond to, and recover from cyber incidents effectively.
Core Components of the NIST Cybersecurity Framework
a. Identify: The "Identify" phase involves developing a comprehensive understanding of an organization's cybersecurity risks, vulnerabilities, and potential impacts. Organizations must prioritize and protect critical assets, whether physical or digital. The framework emphasizes the importance of knowing the threat landscape and establishing risk management processes.
b. Protect: In the "Protect" phase, the NIST framework focuses on implementing safeguards to limit or contain the impact of cybersecurity incidents. This includes the implementation of access controls, training employees on cybersecurity best practices, and deploying encryption techniques to secure sensitive data.
c. Detect: The "Detect" phase revolves around establishing continuous monitoring capabilities to identify cybersecurity threats promptly. Organizations are encouraged to deploy intrusion detection systems, log monitoring tools, and other technologies to swiftly identify any suspicious activities.
d. Respond: In the event of a cybersecurity incident, the "Respond" phase guides organizations on how to respond effectively. This includes developing an incident response plan, containing the incident, conducting forensic analysis, and communicating with relevant stakeholders.
e. Recover: The "Recover" phase emphasizes the importance of restoring normal operations following a cybersecurity incident. Organizations are advised to conduct a lessons-learned analysis to improve future incident responses and recovery efforts.
Benefits of Adopting the NIST Cybersecurity Framework
a. Tailored Approach: One of the key advantages of the NIST Cybersecurity Framework is its flexibility. Organizations can adapt and scale the framework to meet their specific needs, taking into account their size, industry, and risk tolerance.
b. Risk Management: By promoting a risk-based approach, the NIST Cybersecurity Framework allows organizations to allocate resources efficiently. This ensures that the most critical assets receive the highest levels of protection.
c. Industry-wide Recognition: The NIST Cybersecurity Framework is widely recognized and adopted by both the private and public sectors. Embracing this framework enhances an organization's reputation and fosters trust among customers, partners, and regulators.
d. Continuous Improvement: The framework encourages a continuous improvement cycle, enabling organizations to evolve their cybersecurity practices as threats and technologies change.
Implementing the NIST Cybersecurity Framework
While adopting the NIST Cybersecurity Framework can significantly enhance organizational security, its successful implementation requires commitment and cooperation from all levels within an organization. Key steps include:
a. Leadership Support: Senior management must endorse and champion the framework's implementation, providing the necessary resources and support.
b. Risk Assessment: Organizations must conduct a thorough risk assessment to identify their vulnerabilities and potential impacts.
c. Aligning with Best Practices: Organizations should align their existing cybersecurity practices with the framework's guidelines to ensure comprehensive coverage.
d. Training and Awareness: Properly training employees about cybersecurity risks and best practices is crucial to the success of the framework.
e. Regular Assessments: Regularly assess and review the effectiveness of the implemented cybersecurity measures and make necessary improvements.
Conclusion
In conclusion, the NIST Cybersecurity Framework offers organizations a powerful tool to enhance their security posture in the face of ever-evolving cyber threats. By following the framework's core components and guidelines, organizations can effectively identify, protect, detect, respond to, and recover from cyber incidents. As the digital landscape continues to expand, embracing the NIST Cybersecurity Framework will prove to be a wise and proactive approach to safeguarding sensitive information and ensuring business continuity.(Note: The keyword "NIST Cybersecurity Framework" has been used multiple times throughout the article to maintain keyword density.)




