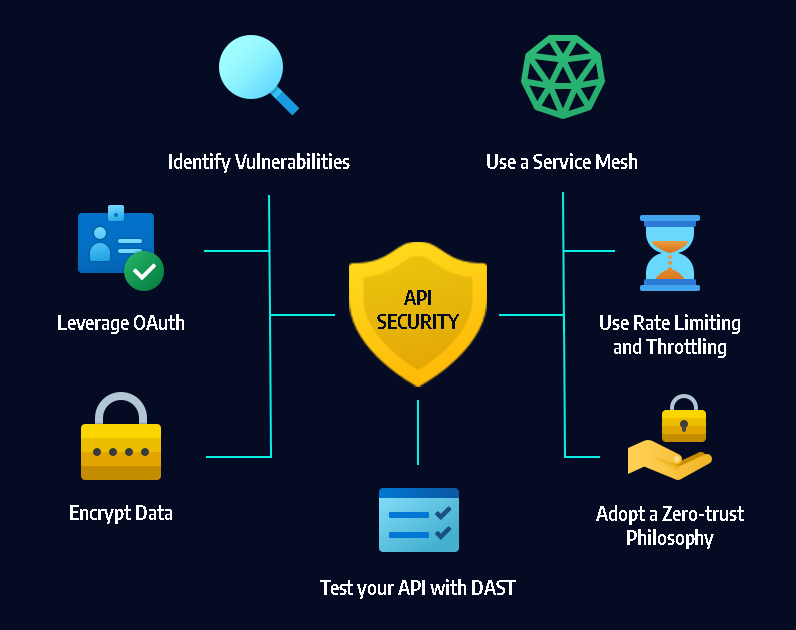
API tokens are widely used in modern web applications and services as a means of authentication and authorization. These tokens provide a secure way for applications to interact with APIs, but they also come with their own set of risks. In this article, we will explore the risks associated with API token security and provide recommendations to mitigate these risks effectively.
Risks of API Token Security:
a. Exposure of Sensitive Information: API tokens, especially if transmitted in URLs or as query parameters, can be easily exposed in server logs, browser histories, or network traffic, leading to unauthorized access if intercepted.
b. Token Leakage: Developers may inadvertently leak API tokens by including them in publicly accessible code repositories or configuration files, making them vulnerable to exploitation.
c. Lack of Token Expiry: If API tokens do not have a limited validity period or do not expire upon logout, they may be susceptible to unauthorized access, even after a user session has ended.
d. Man-in-the-Middle Attacks: Attackers can intercept API tokens during transmission if proper encryption and secure communication channels are not employed, leading to potential token theft.
e. Insufficient Entropy: Weak token generation mechanisms may lead to predictable token values, making it easier for attackers to guess or brute-force tokens.
Recommendations for API Token Security:
a. Use HTTPS for Token Transmission: Always transmit API tokens over HTTPS to ensure secure communication between the client and server, preventing interception by unauthorized parties.
b. Implement Token Expiry and Rotation: Set a reasonable expiry time for API tokens and regularly rotate them to reduce the window of opportunity for attackers to misuse stolen tokens.
c. Store Tokens Securely: Avoid storing API tokens in client-side storage mechanisms like cookies or local storage, as they are more vulnerable to theft. Instead, use HttpOnly cookies or other secure storage mechanisms on the server side.
d. Avoid Transmitting Tokens in URLs or Query Parameters: Transmitting tokens in URLs or query parameters can lead to token exposure. Use HTTP headers (e.g., Authorization header) for token transmission instead.
e. Use Strong Token Generation: Ensure that API tokens are generated using a strong cryptographic random number generator to maximize unpredictability and avoid easily guessable values.
f. Monitor Token Activity: Implement token activity monitoring and logging to detect suspicious behavior or unauthorized token usage promptly.
g. Regular Security Audits: Conduct regular security audits and penetration testing to identify vulnerabilities and weaknesses in the API token implementation.
h. Employ Token Scopes and Permissions: Implement token scopes and permissions to limit the actions a token can perform. This principle of least privilege ensures that each token has the minimum required access rights.
i. Enable Multi-Factor Authentication (MFA): Consider using MFA alongside API tokens to add an extra layer of security, making it harder for attackers to compromise the token.
Conclusion:
API tokens play a vital role in securing interactions between applications and APIs. However, their improper implementation can lead to serious security risks, including unauthorized access and data breaches. By following the best practices mentioned above, developers and organizations can significantly enhance the security of their API token systems. Regular security audits, monitoring token activity, and employing strong token generation mechanisms are essential steps to safeguard against token-related risks. With a proactive approach to API token security, businesses can confidently utilize these tokens to enable secure and seamless communication between their applications and APIs.




