
Automating Metasploit with Pymetasploit3 in Continuous Integration
May 8, 2023

Role of AI in Cybersecurity: Opportunities & Challenges
May 5, 2023
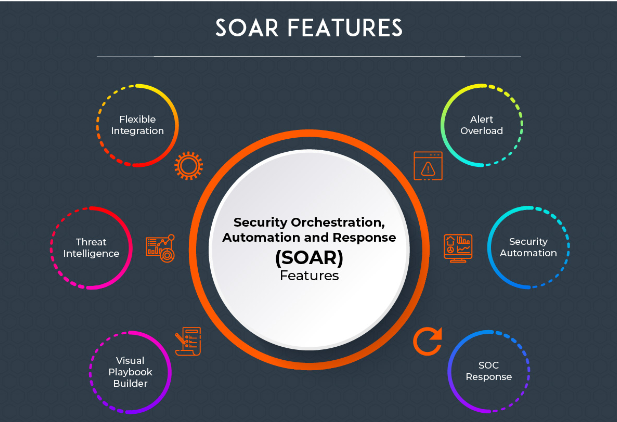
The Role of Security Orchestration, Automation, and Response in Cyber Defense
June 21, 2023

The Future of Tech: What to Expect in the Next Decade
June 26, 2023

How Can We Automate Penetration Testing In Order To Improve Network Security
June 2, 2023

What Priority Is Looking For Security Vulnerabilities In The Packages And Libraries?
June 3, 2023