Web Penetration Testing - Cyber Attacks

Protecting Your Wireless Network Against Cyber Attacks
May 12, 2023
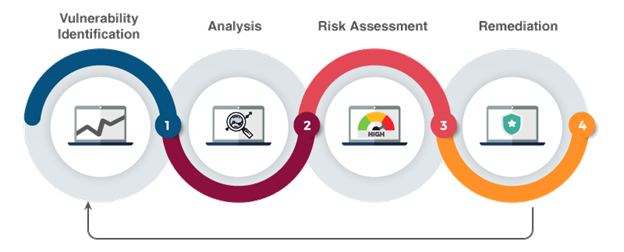
Assessing the Security of Cloud Environments
May 13, 2023

Collecting Volatile Data and Identifying Attack Patterns through Forensic Analysis
May 15, 2023
Understanding the Psychology of Cybercriminals
May 5, 2023

Understanding the Importance of Cyber Insurance in Today's Business
May 6, 2023

Role of AI in Cybersecurity: Opportunities & Challenges
May 5, 2023