In today's interconnected world, where vast amounts of data are generated, processed, and stored, data breaches pose a significant threat to individuals and organizations alike. Cybercriminals constantly devise new methods to exploit vulnerabilities and gain unauthorized access to sensitive information, making data breach prevention an increasingly critical priority.
Thankfully, the rapid advancements in technology have not only given rise to sophisticated cyber threats but also provided innovative tools and solutions to combat them. In this article, we explore the emerging technologies that play a pivotal role in data breach prevention. We will delve into their implications, advantages, and limitations, shedding light on how organizations can leverage these solutions to fortify their cybersecurity defenses.
1. Artificial Intelligence and Machine Learning
Artificial Intelligence (AI) and Machine Learning (ML) have revolutionized the cybersecurity landscape by empowering organizations to detect and respond to data breaches proactively. AI algorithms can analyze vast volumes of data, identify patterns, and recognize anomalies that indicate potential security threats. By continuously learning from new data, AI-based systems can adapt to evolving attack vectors, enhancing their accuracy over time.
ML algorithms are particularly effective in anomaly detection, where they establish baseline behavior and raise alerts when deviations occur. This helps organizations identify suspicious activities, detect insider threats, and prevent data breaches in real-time. Additionally, AI-powered threat intelligence platforms leverage natural language processing and sentiment analysis to scour the web for indicators of impending attacks, enabling proactive mitigation.
However, it's important to acknowledge the limitations of AI and ML in data breach prevention. Adversarial attacks can exploit vulnerabilities in AI models, making them susceptible to manipulation. Continual human oversight and model retraining are necessary to mitigate such risks and ensure the effectiveness of AI-based security systems

2. Blockchain Technology
Blockchain technology, widely known as the foundation of cryptocurrencies, offers promising potential for enhancing data breach prevention. By design, blockchain creates an immutable and decentralized ledger that records and verifies transactions across multiple nodes. This distributed nature makes it incredibly challenging for attackers to tamper with or compromise the data stored within the blockchain.
In the context of data breach prevention, blockchain can be used to secure sensitive information, such as personal identities or medical records. With blockchain-based identity management systems, users can maintain control over their data, granting permission for access only when necessary. Blockchain's cryptographic algorithms ensure the integrity of stored data and provide a transparent audit trail, simplifying breach investigations.
However, implementing blockchain for data breach prevention comes with certain considerations. Scalability and performance limitations, high energy consumption, and regulatory challenges must be addressed to fully harness the potential of this technology. Furthermore, while blockchain enhances data security, it does not eliminate the risks associated with vulnerabilities at the endpoints or weak access controls.

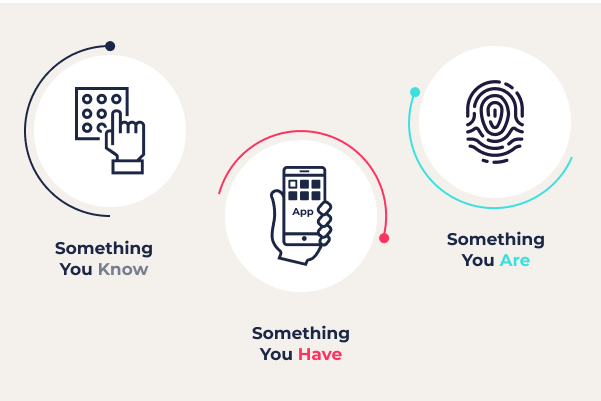
3. Biometric Authentication
Traditional authentication methods, such as passwords or PINs, can be easily compromised, leading to data breaches. Biometric authentication offers a more secure alternative by utilizing unique physical or behavioral characteristics, such as fingerprints, facial recognition, or voice patterns, for identity verification.
Biometric authentication significantly reduces the risk of unauthorized access to sensitive information. Even if credentials are stolen, an attacker would still require the specific biometric data of the authorized user to gain access. Biometric systems also provide a seamless user experience by eliminating the need for memorizing and managing multiple passwords.
However, the implementation of biometric authentication must address privacy concerns and ensure robust protection of biometric data. Biometric information must be securely stored, encrypted, and compliant with privacy regulations. Organizations should also consider the possibility of biometric data breaches, such as synthetic fingerprint attacks, and implement robust anti-spoofing measures.
Conclusion
Data breach prevention requires a comprehensive approach that combines technology, processes, and a vigilant cybersecurity culture. Emerging technologies, such as Artificial Intelligence and Machine Learning, blockchain, and biometric authentication, offer powerful tools to enhance data security and prevent breaches. These technologies enable organizations to detect anomalies, secure data through decentralization, and provide more robust identity verification.
However, it is crucial to recognize that no single technology can guarantee complete protection against data breaches. A multi-layered security strategy, regular risk assessments, employee training, and proactive monitoring are essential components of a robust data breach prevention framework.
By harnessing the potential of emerging technologies and adopting a holistic approach to cybersecurity, organizations can significantly reduce the risk of data breaches, safeguard sensitive information, and build trust with their stakeholders in an increasingly digital world.