In an increasingly connected world, the need for secure communication has become paramount. From sensitive financial transactions to confidential government communications, the protection of information is of utmost importance. Traditional encryption methods have long been the bedrock of secure communication, but with the advent of quantum computing, they face new vulnerabilities.
Enter quantum cryptography, a field that harnesses the principles of quantum mechanics to create unbreakable encryption. In this article, we will explore the fascinating world of quantum cryptography, its advantages over traditional encryption, and its potential to revolutionize secure communication.
Understanding Quantum Mechanics
Before delving into quantum cryptography, let's briefly understand the basics of quantum mechanics. Quantum mechanics is the branch of physics that deals with the behavior of matter and energy on the smallest scales, such as atoms and subatomic particles. It introduces fundamental concepts such as superposition and entanglement, which form the basis of quantum cryptography.
Quantum Key Distribution (QKD)
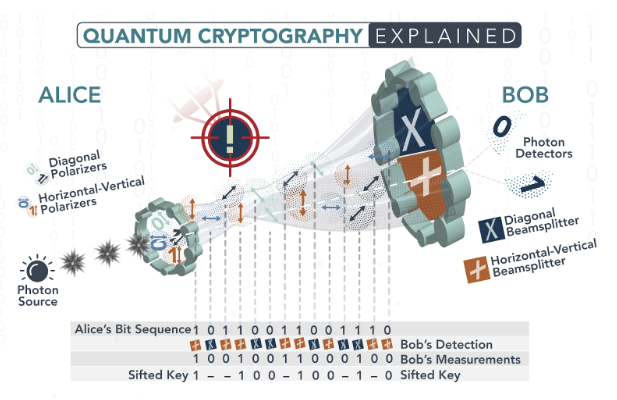
At the heart of quantum cryptography lies Quantum Key Distribution (QKD). QKD is a method of securely sharing encryption keys between two parties, known as Alice and Bob. Unlike traditional encryption, which relies on the computational complexity of factoring large numbers, QKD utilizes the principles of quantum mechanics to ensure the security of the shared keys.
The process begins with Alice generating a string of random bits and encoding them onto individual quantum particles, typically photons. She then sends the photons to Bob, who measures them using a specific set of measurements. The nature of quantum mechanics ensures that any attempt to intercept or measure the photons by an eavesdropper, known as Eve, will disrupt the quantum state of the particles. This disruption can be detected by Alice and Bob, allowing them to discard the compromised bits and establish a secure encryption key.
Advantages of Quantum Cryptography
Quantum cryptography offers several advantages over traditional encryption methods:
Unbreakable Encryption: Due to the principles of quantum mechanics, any attempt to intercept the quantum signals will disturb the particles, alerting the communicating parties. This inherent property makes quantum cryptography immune to eavesdropping, providing unbreakable encryption.
Information-Theoretic Security: Traditional encryption methods rely on computational assumptions, which could be vulnerable to advancements in computing power. In contrast, quantum cryptography offers information-theoretic security, meaning the security of the system is based on fundamental physical principles rather than computational complexity.
Key Distribution Efficiency: QKD allows for the efficient distribution of encryption keys over long distances. With advancements in quantum technology, secure communication channels can be established between parties located far apart, enabling global secure communication networks.
Applications of Quantum Cryptography
The potential applications of quantum cryptography are vast and can revolutionize secure communication in various fields:
Financial Sector: Quantum cryptography can enhance the security of financial transactions, protecting sensitive information such as credit card details and banking transactions from potential hackers. It can also prevent unauthorized access to financial databases.
Government and Defense: Governments and defense organizations deal with highly classified information that requires the utmost security. Quantum cryptography can provide unbreakable encryption for secure communication channels between government officials and military personnel, safeguarding national security interests.
Healthcare and Medical Research: In the healthcare industry, patient data privacy is crucial. Quantum cryptography can ensure secure communication between healthcare providers, protecting medical records and research data from unauthorized access or tampering.
Internet of Things (IoT): With the proliferation of IoT devices, ensuring secure communication and data privacy is essential. Quantum cryptography can establish secure connections between IoT devices, safeguarding sensitive information transmitted through these devices.
Challenges and Future Directions
While quantum cryptography holds great promise, there are still challenges to overcome before it becomes widely adopted:
Technological Advancements: Quantum cryptography requires highly specialized and expensive equipment. Advancements in quantum technology and the development of more practical and cost-effective solutions are necessary to make quantum cryptography accessible to a broader audience.
Infrastructure Requirements: Building a quantum communication infrastructure capable of supporting secure communication over long distances is a significant undertaking. Developing a network of quantum repeaters and quantum satellite systems is crucial for the widespread adoption of quantum cryptography.
Standardization: Establishing international standards for quantum cryptography protocols and systems is essential to ensure interoperability and trust among different implementations.
Conclusion
Quantum cryptography represents a promising future for unbreakable encryption. By harnessing the principles of quantum mechanics, it offers unprecedented levels of security and opens up new possibilities for secure communication in various sectors. As technological advancements continue and infrastructure develops, quantum cryptography has the potential to revolutionize the way we protect sensitive information and communicate securely in an increasingly interconnected world.