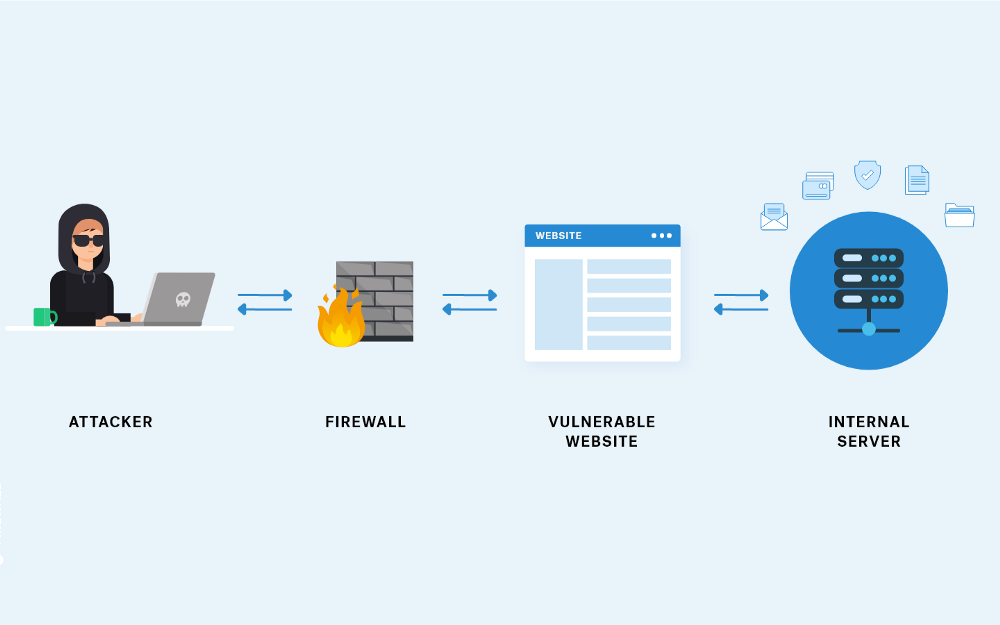
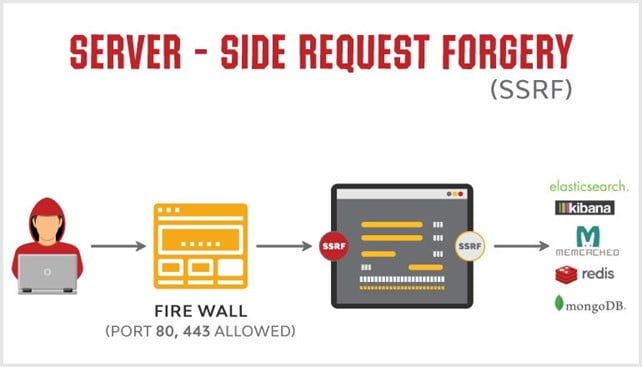
In today's rapidly evolving digital landscape, ensuring the security of our networks and systems has become paramount. Penetration testing, a critical component of any robust security strategy, allows organizations to proactively identify vulnerabilities and strengthen their defenses.
However, traditional manual penetration testing methods can be time-consuming, expensive, and prone to human error. To overcome these limitations, the automation of penetration testing has emerged as a transformative solution.
This article explores the benefits, challenges, and best practices associated with automating penetration testing, shedding light on how this approach can significantly improve network security.
Understanding Penetration Testing
Before diving into the specifics of automation, it is crucial to understand the fundamentals of penetration testing. This section provides an overview of the purpose, methodologies, and key objectives of penetration testing. By comprehending the underlying principles of this practice, readers will gain a solid foundation for understanding how automation can enhance its effectiveness.
The Power of Automation
Automation brings a multitude of advantages to the realm of penetration testing. This section delves into the benefits of automated approaches, including increased efficiency, scalability, and accuracy. By automating repetitive tasks, organizations can allocate resources more effectively, identify vulnerabilities at a faster pace, and respond swiftly to emerging threats. Furthermore, automation enables penetration testers to focus on critical thinking and analysis, leveraging their expertise to craft more robust security strategies.
Overcoming Challenges
While automation presents numerous advantages, it is not without its challenges. This section explores the potential obstacles that organizations may face when implementing automated penetration testing. From technical complexities to the need for skilled personnel and the importance of maintaining a balance between automation and human intervention, readers will gain valuable insights into the key considerations that accompany this transformative approach.
Best Practices for Automated Penetration Testing
To ensure successful implementation, organizations must adhere to best practices when automating penetration testing. This section provides a comprehensive guide, covering crucial aspects such as selecting the right tools, establishing clear goals and objectives, designing realistic test scenarios, and integrating automation seamlessly into existing security workflows. By following these best practices, organizations can maximize the effectiveness of automated penetration testing and achieve significant improvements in network security.
The Human Touch: Balancing Automation and Expertise
While automation plays a pivotal role in enhancing penetration testing, it is important to strike a balance between automated processes and human expertise. This section emphasizes the role of human intervention in interpreting results, conducting advanced analysis, and making strategic decisions based on the findings. By leveraging the strengths of automation while recognizing its limitations, organizations can optimize their network security efforts.
Conclusion
As cyber threats continue to evolve, automation is revolutionizing the field of penetration testing, offering a more efficient, scalable, and accurate approach to enhancing network security. By understanding the benefits, overcoming challenges, and implementing best practices, organizations can unlock the full potential of automated penetration testing. Striking the right balance between automation and human expertise will empower organizations to build robust defenses against emerging threats, safeguarding their networks and systems in an increasingly interconnected world.