
Cyber Insurance: Lessons Learned and Best Practices for Coverage.
May 16, 2023

Best Practices For Securing Your Remote Workforce
May 9, 2023

JBS Foods Ransomware Attack: Everything You Need To Know
May 8, 2023

How to Develop a Cybersecurity Incident Response Plan for Your Business
May 6, 2023
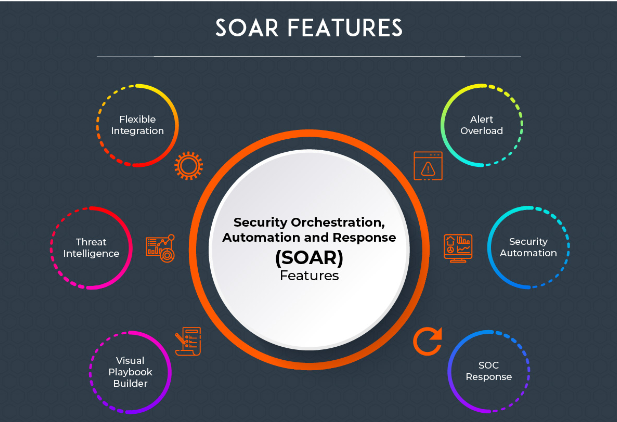
The Role of Security Orchestration, Automation, and Response in Cyber Defense
June 21, 2023

Nelnet Servicing Breach Exposes Data of 2.5 Million Student Loan Accounts
June 10, 2023

Securing Cloud-Native Applications: Considerations and Best Practices
June 13, 2023