Web Penetration Testing - Prevention
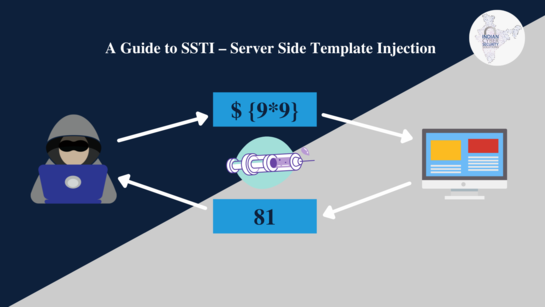
Server-Side Template Injection (SSTI): Exploitation Techniques
July 15, 2023
Remote File Inclusion (RFI) and Local File Inclusion (LFI) Attacks
July 11, 2023

XML External Entity (XXE) Attacks
July 11, 2023

Exploiting File Upload Vulnerabilities in Web Applications
July 10, 2023

Collecting Volatile Data and Identifying Attack Patterns through Forensic Analysis
May 15, 2023

Best ways to learn web penetration testing, ethical hacking, and IT security
July 4, 2023

The Impact of Social Engineering on Cybersecurity
July 3, 2023

Rising Threat of Ransomware and its Prevention By AI and Machine Learning
May 11, 2023

The Future of Ransomware
May 11, 2023

Ransomware and the Supply Chain
May 10, 2023

LastPass Hack: Understanding the Risks and Protecting Your Passwords
May 10, 2023

Understanding The Dark Web And Its Role In Cybercrime
May 9, 2023

Top Cybersecurity threats facing businesses in 2023
May 9, 2023

JBS Foods Ransomware Attack: Everything You Need To Know
May 8, 2023
The NotPetya Ransomware Attack: A Case Study in Destructive Malware
May 8, 2023

Major Data Breach in India Exposes COVID-19 Vaccination Data
June 14, 2023

Uber Data Breach Exposes Driver and Passenger Data
June 5, 2023

Emerging Technologies And Their Implications On Data Breach Prevention
June 8, 2023
Cyberbullying: A Growing Problem
June 28, 2023

STYX: The Newest Dark Web Market
June 8, 2023

North Korean Hackers Breach Hospital in Seoul, Threatening Data Security
June 13, 2023