Web Penetration Testing - Security Vulnerabilities
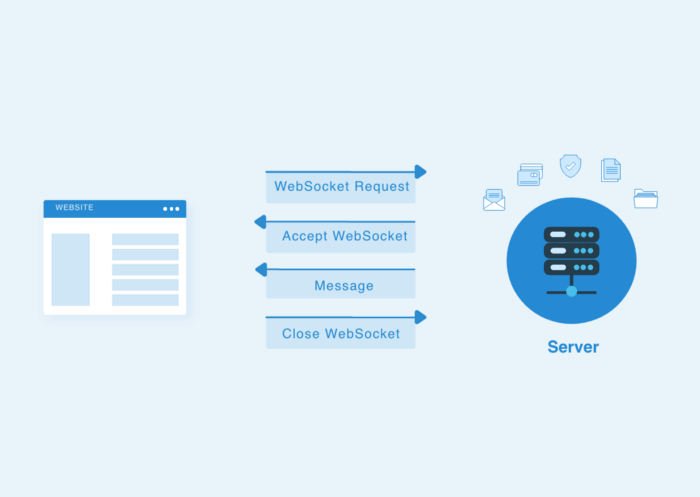
WebSocket Hijacking: Techniques and Countermeasures
July 31, 2023

GraphQL Security: Common Vulnerabilities and Best Practices
July 25, 2023

Business Logic Flaws in Web Applications: Detection and Exploitation
July 24, 2023
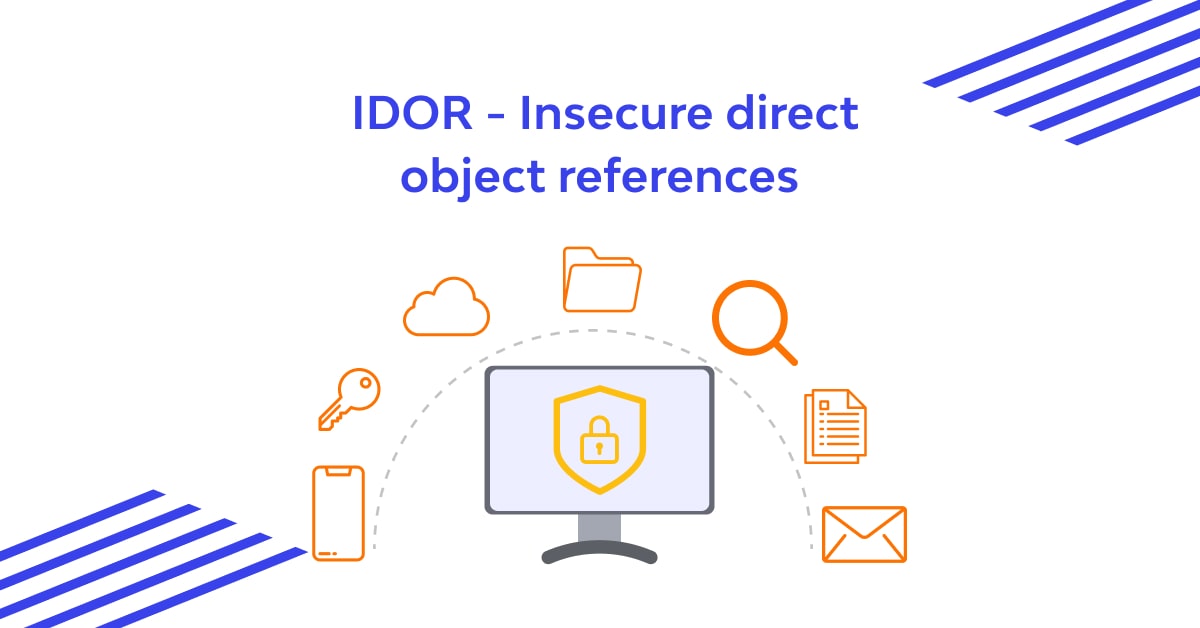
Insecure Direct Object References (IDOR): Exploitation and Prevention
July 17, 2023
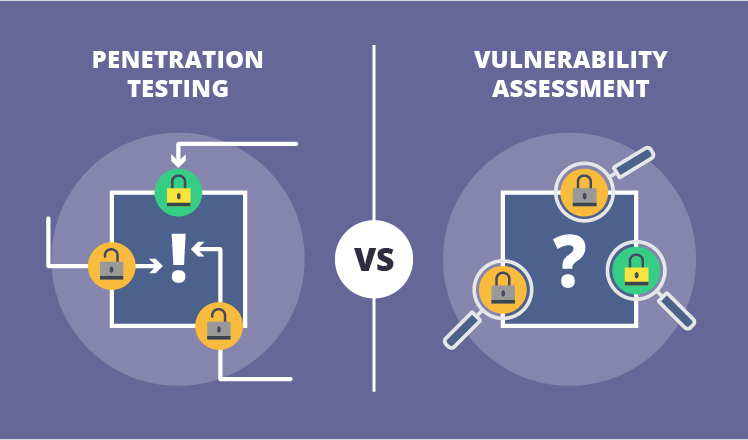
Vulnerability Assessment vs. Penetration Testing: What's the Difference?
July 13, 2023

Web Application Security Scanning Tools: A Comparative Analysis
July 12, 2023
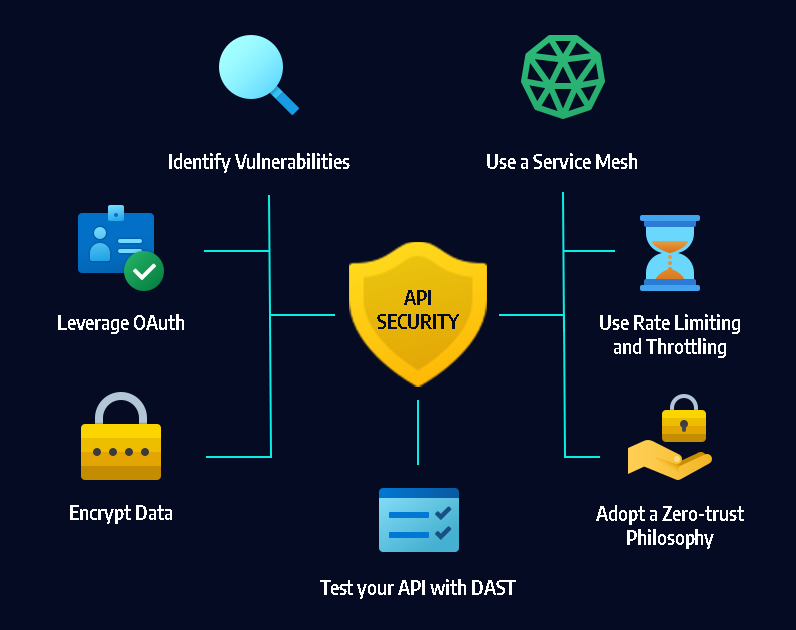
API Security Testing: Best Practices and Tools
July 12, 2023

XML External Entity (XXE) Attacks
July 11, 2023