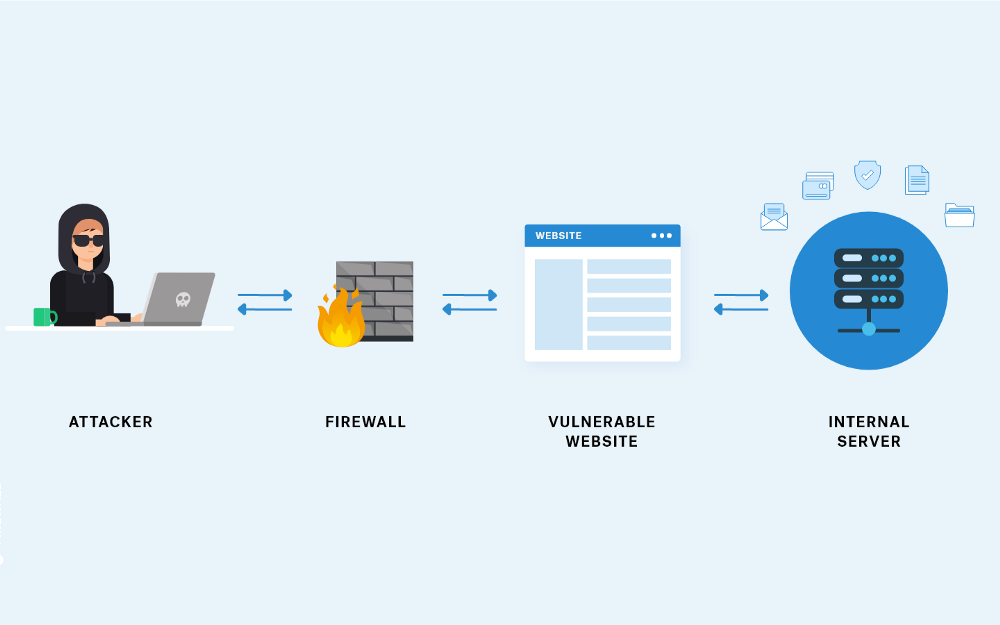
Server-side request forgery (SSRF) is a type of attack that allows an attacker to trick a vulnerable server into making requests to arbitrary external services. This can be used to access sensitive information, execute arbitrary commands, or even take control of the server.
Cloud metadata services are a common target for SSRF attacks. These services provide access to sensitive information about the cloud environment, such as the instance ID, the account ID, and the region. If an attacker can exploit a SSRF vulnerability in a cloud metadata service, they can gain access to this sensitive information and use it to launch further attacks.
How SSRF Exploitation in Cloud Metadata Services Works
SSRF attacks in cloud metadata services typically work by exploiting a vulnerability in the way that the service handles user input. For example, the service might allow users to specify the URL of the external service that they want to make a request to. If the service does not properly validate this input, an attacker could specify a URL that points to a malicious service.
Once the attacker has specified a malicious URL, the cloud metadata service will make a request to that URL. The malicious service can then use this request to access sensitive information or execute arbitrary commands.
Case Study: The Capital One Data Breach
One of the most well-known examples of SSRF exploitation in cloud metadata services was the Capital One data breach in 2019. In this attack, the attackers exploited a SSRF vulnerability in a web application that was used to manage Capital One's cloud infrastructure. The vulnerability allowed the attackers to make requests to the AWS metadata service, which they used to obtain access keys for various AWS resources.
With these access keys, the attackers were able to access sensitive data from Capital One's AWS accounts, including customer credit card numbers and Social Security numbers. The breach ultimately affected over 100 million people.
How to Protect Against SSRF Exploitation in Cloud Metadata Services
There are a number of steps that can be taken to protect against SSRF exploitation in cloud metadata services. These include:
Validating user input carefully: Cloud metadata services should carefully validate all user input before making requests to external services. This includes checking for malicious characters and ensuring that the URL is properly formatted.
Using a web application firewall (WAF): A WAF can help to detect and block SSRF attacks.
Educating developers about SSRF vulnerabilities: Developers should be aware of the risks of SSRF vulnerabilities and how to prevent them.
By following these steps, organizations can help to protect themselves from SSRF exploitation in cloud metadata services.
Conclusion
SSRF exploitation in cloud metadata services is a serious security risk. By understanding how these attacks work and taking steps to protect against them, organizations can help to keep their data safe.
Additional Information
In addition to the steps outlined above, there are a number of other things that organizations can do to protect themselves from SSRF attacks. These include:
Using a secure coding methodology: This will help to ensure that code is written in a way that is resistant to SSRF attacks.
Keeping cloud metadata services up to date: Cloud providers often release security patches for cloud metadata services. Organizations should keep their cloud metadata services up to date to ensure that they are protected from the latest vulnerabilities.
Monitoring for SSRF attacks: Organizations should monitor their cloud environment for signs of SSRF attacks. This can be done by using a WAF or by other means.
By taking these steps, organizations can help to protect themselves from SSRF attacks and keep their data safe.




