Ransomware attacks have emerged as one of the most significant cyber threats in recent years. Cybercriminals have perfected their techniques, targeting both individuals and organizations with sophisticated malware that encrypts valuable data, holding it hostage until a ransom is paid.
This article aims to shed light on the latest ransomware attacks and provide comprehensive guidance on how to avoid them. By understanding the evolving tactics employed by cybercriminals and implementing proactive security measures, you can fortify your defenses and safeguard your digital world.
Understanding Ransomware
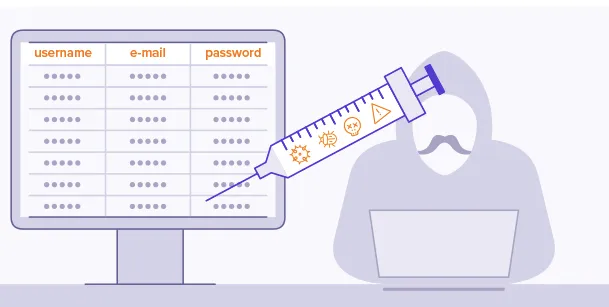
Ransomware is a type of malware that encrypts a victim's files or locks them out of their system until a ransom is paid. Attackers typically demand payment in cryptocurrencies, such as Bitcoin, to make it difficult to trace the transactions. The rise of anonymous networks and the increasing value of cryptocurrencies have made ransomware attacks highly profitable for cybercriminals.
Recent Ransomware Attacks
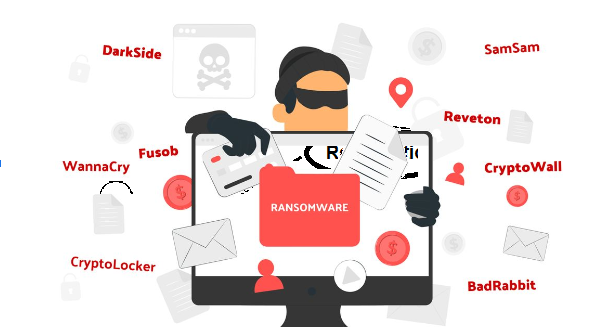
In this section, we'll explore some of the most notorious ransomware attacks that have taken place recently, highlighting their impact on individuals and organizations alike. We'll discuss attacks such as WannaCry, NotPetya, and Ryuk, providing insights into their techniques, targets, and consequences. By understanding these real-world examples, readers can grasp the severity of the threat and the potential devastation that can result from falling victim to a ransomware attack.
Common Attack Vectors
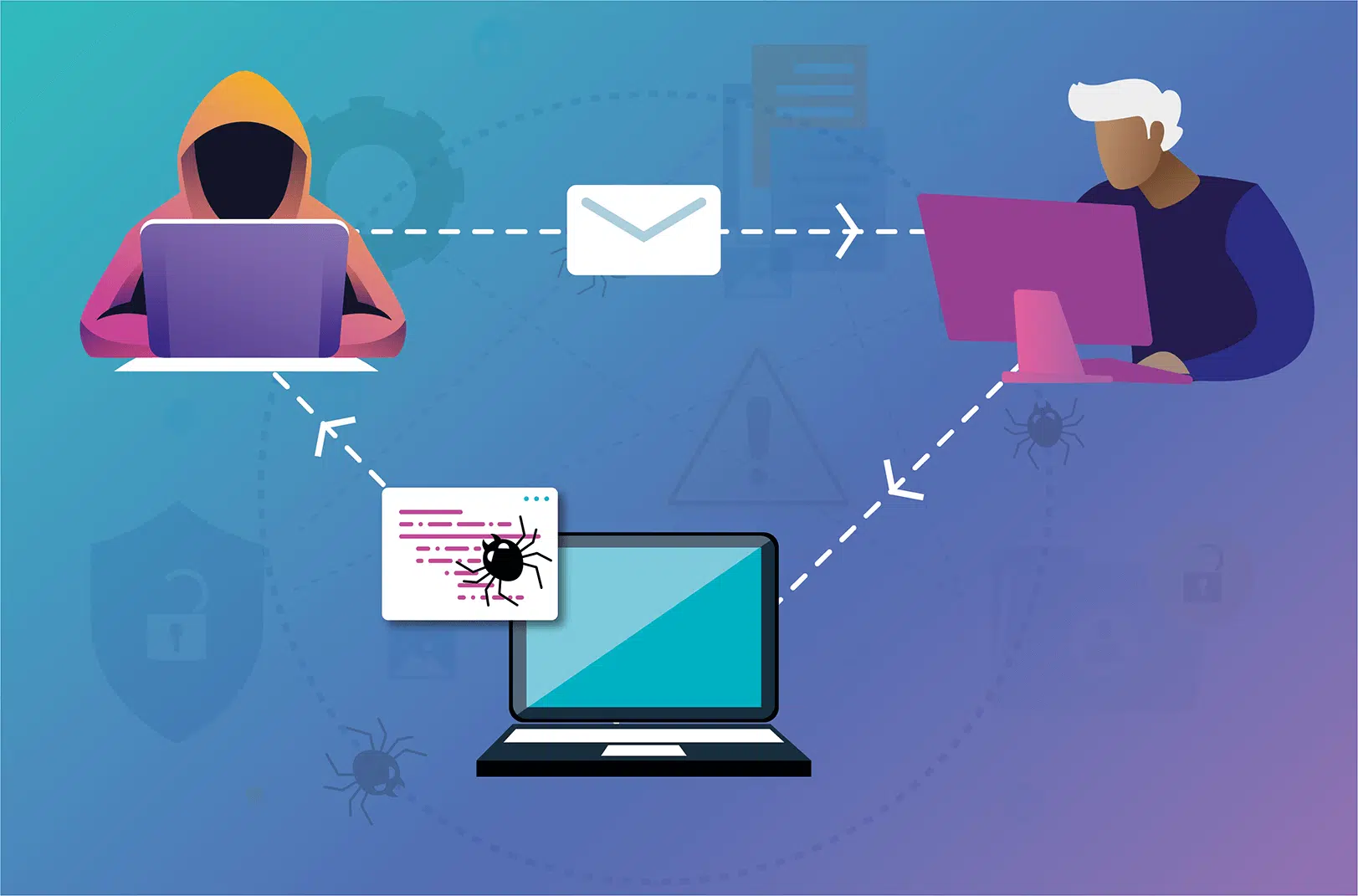
To effectively protect against ransomware, it's crucial to understand how cybercriminals gain access to systems. In this section, we'll delve into the most common attack vectors exploited by ransomware attackers, including phishing emails, malicious attachments, drive-by downloads, and compromised websites. By recognizing these entry points, users can be better equipped to identify and avoid potential threats.
Preventive Measures and Best Practices
This section focuses on practical strategies to avoid falling victim to ransomware attacks. We'll cover essential preventive measures, such as regularly updating software, employing robust antivirus and anti-malware solutions, and implementing strong, unique passwords. Additionally, we'll discuss the importance of regular data backups, network segmentation, user awareness training, and the need for a comprehensive incident response plan.
Future Trends and Emerging Technologies
As ransomware attacks continue to evolve, it is essential to stay updated on the latest trends and emerging technologies that can help combat this threat. This section provides a glimpse into potential future developments, such as machine learning and artificial intelligence-based security solutions, blockchain technology for enhanced data integrity, and the importance of proactive threat hunting and behavior-based detection.
Conclusion
Ransomware attacks pose a significant risk to individuals and organizations alike. However, by staying informed about the latest attack methods and implementing robust security measures, you can greatly reduce the chances of falling victim to this malicious threat. Remember to regularly update your software, educate yourself and your team about phishing scams, and maintain secure backups of your data. By adopting a proactive approach to cybersecurity, you can protect your digital assets and ensure peace of mind in an increasingly connected world.