Introduction
The threat landscape is constantly evolving, and businesses are under increasing pressure to improve their cyber defenses. One way to do this is to adopt security orchestration, automation, and response (SOAR) solutions.
SOAR platforms help organizations to automate and orchestrate security processes, such as incident response, threat hunting, and compliance. This can free up security analysts to focus on more complex tasks, and it can help to improve the speed and accuracy of response to security incidents.
What is SOAR?
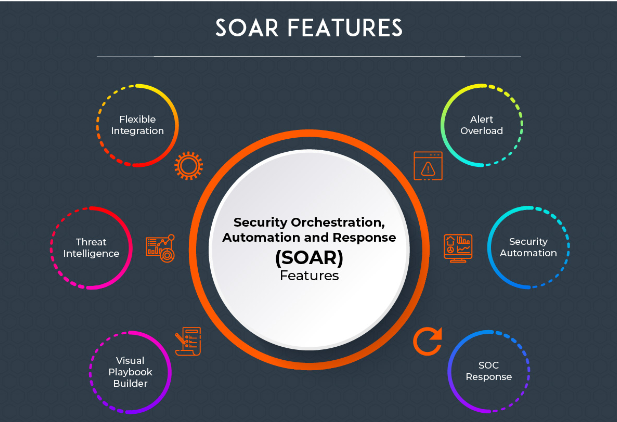
SOAR stands for security orchestration, automation, and response. It is a software platform that helps organizations to automate and orchestrate security processes. SOAR platforms typically include a number of features, such as:
Security orchestration: This allows organizations to automate the flow of information between different security tools and systems.
Security automation: This allows organizations to automate repetitive security tasks, such as incident response and threat hunting.
Security response: This provides organizations with a centralized repository for security information and enables them to quickly respond to security incidents.
Benefits of SOAR
There are a number of benefits to using SOAR solutions, including:
Improved efficiency: SOAR can help to improve the efficiency of security operations by automating repetitive tasks and by providing a centralized repository for security information.
Increased accuracy: SOAR can help to improve the accuracy of security operations by providing a more comprehensive view of the security environment and by automating the decision-making process.
Reduced risk: SOAR can help to reduce the risk of security incidents by automating the response process and by providing a more proactive approach to security.
How SOAR Works
SOAR platforms typically work by integrating with a variety of security tools and systems. This allows the platform to collect data from these tools and systems and to automate the flow of information between them. The platform can also be used to automate repetitive security tasks, such as incident response and threat hunting.
When a security incident occurs, the SOAR platform can be used to quickly identify the incident, to collect information about the incident, and to automate the response to the incident. This can help to reduce the impact of the incident and to minimize the damage caused.
Use Cases for SOAR
SOAR platforms can be used for a variety of use cases, including:
Incident response: SOAR platforms can be used to automate the incident response process. This can help to speed up the response to incidents and to improve the accuracy of the response.
Threat hunting: SOAR platforms can be used to automate the threat hunting process. This can help to identify potential threats that may not be detected by other security tools.
Compliance: SOAR platforms can be used to automate compliance tasks. This can help organizations to demonstrate compliance with various security regulations.
Conclusion
SOAR platforms are a valuable tool for organizations that are looking to improve their cyber defenses. SOAR platforms can help to automate and orchestrate security processes, which can free up security analysts to focus on more complex tasks. SOAR platforms can also help to improve the speed and accuracy of response to security incidents.
If you are looking for a way to improve your cyber defenses, then you should consider adopting a SOAR platform. SOAR platforms can help you to automate and orchestrate security processes, which can help you to improve the speed and accuracy of response to security incidents.