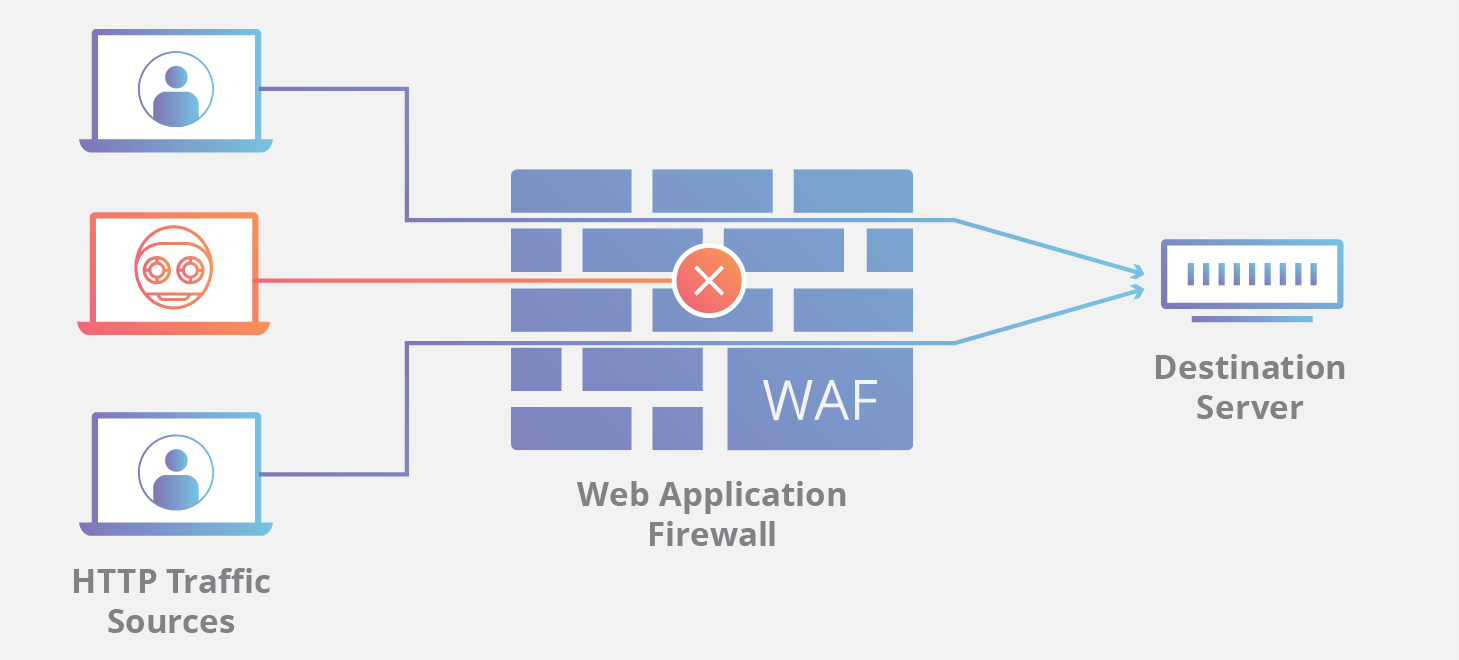
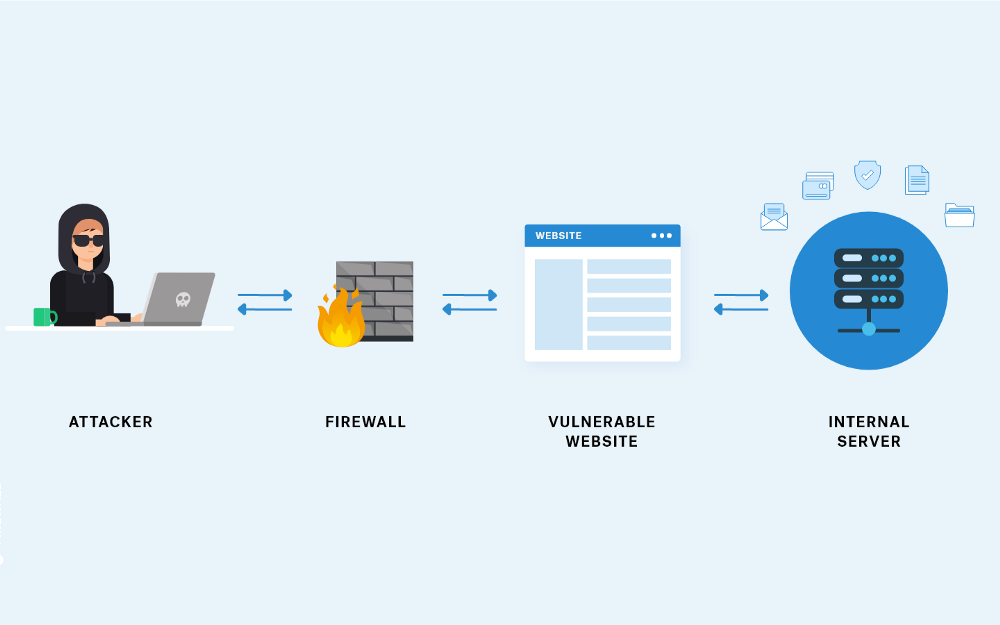
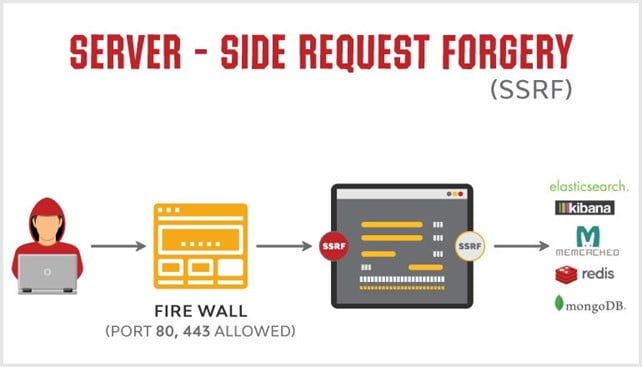
In today's digital landscape, web applications have become essential tools for businesses and individuals alike. However, this widespread use also attracts the attention of malicious actors seeking to exploit vulnerabilities for their own gain. To ensure the security of web applications, it is crucial to adopt a proactive approach that includes threat modelling and penetration testing.
This article serves as a comprehensive guide, explaining the importance of threat modelling in web application security, and providing insights into how to assess risks and their potential impact effectively. By implementing these strategies, you can protect your web applications and safeguard sensitive data.
Understanding Threat Modelling
Threat modelling is a proactive process that helps identify potential security risks and vulnerabilities within a system or application.
By systematically analyzing the components, functionalities, and potential threats, threat modelling enables organizations to better understand the potential risks and take appropriate measures to mitigate them. It involves identifying assets, identifying potential threats, and assessing the impact of these threats on the system.
Assessing Risks
To effectively assess risks, it is essential to categorize them into different levels of severity.
This can be done by considering various factors, such as the likelihood of the threat occurring and the potential impact it may have on the web application. By assigning risk levels, organizations can prioritize their security efforts and allocate resources accordingly. Risks can be classified as low, medium, or high, depending on the severity and likelihood of their occurrence.
This classification helps organizations focus on critical vulnerabilities first, ensuring that their resources are used effectively.
Impact of Risks
Understanding the potential impact of risks is crucial to prioritize remediation efforts.
Each identified risk should be evaluated based on its potential consequences, such as data breaches, unauthorized access, or financial loss. By assessing the impact of risks, organizations can determine the severity of a vulnerability and prioritize their response accordingly.
This ensures that resources are allocated effectively to address the most critical threats and minimize potential damage to the web application.
Penetration Testing
Penetration testing is an integral part of threat modelling, serving as a hands-on evaluation of a web application's security. It involves simulated attacks on the application to identify vulnerabilities and determine their exploitable potential.
By conducting penetration tests, organizations can evaluate the effectiveness of their security controls and discover any weaknesses that may exist within their web applications. This helps in identifying and mitigating potential threats before they are exploited by malicious actors.
The process of penetration testing typically involves several steps, including reconnaissance, vulnerability scanning, exploitation, and reporting. During reconnaissance, the tester gathers information about the web application, such as its architecture, technologies used, and potential entry points.
Vulnerability scanning involves using automated tools to scan the application for known vulnerabilities. Exploitation entails attempting to exploit identified vulnerabilities to gain unauthorized access or execute unauthorized actions.
Finally, a detailed report is generated, documenting the findings, potential risks, and recommended remediation measures.
Best Practices for Threat Modelling and Penetration Testing
To ensure the effectiveness of threat modelling and penetration testing, organizations should follow best practices. These include:
Regular assessments: Perform threat modelling and penetration testing on a regular basis to stay proactive against emerging threats and vulnerabilities.
Collaborative approach: Involve different stakeholders, such as developers, security professionals, and business owners, to gain diverse perspectives and comprehensive insights.
Prioritize critical risks: Focus on addressing high-risk vulnerabilities first to minimize potential damage and prioritize resource allocation effectively.
Continuous improvement: Learn from previous assessments and adapt strategies accordingly to enhance the overall security posture.
Conclusion
Threat modelling and penetration testing are essential components of a comprehensive web application security strategy. By adopting a proactive approach and regularly assessing risks, organizations can identify potential vulnerabilities and take the necessary measures to mitigate them effectively.
Through the implementation of best practices and continuous improvement, web applications can be safeguarded against potential threats, ensuring the protection of sensitive data and the overall integrity of the system.
Stay one step ahead of malicious actors by investing in thorough threat modelling and penetration testing for your web applications.