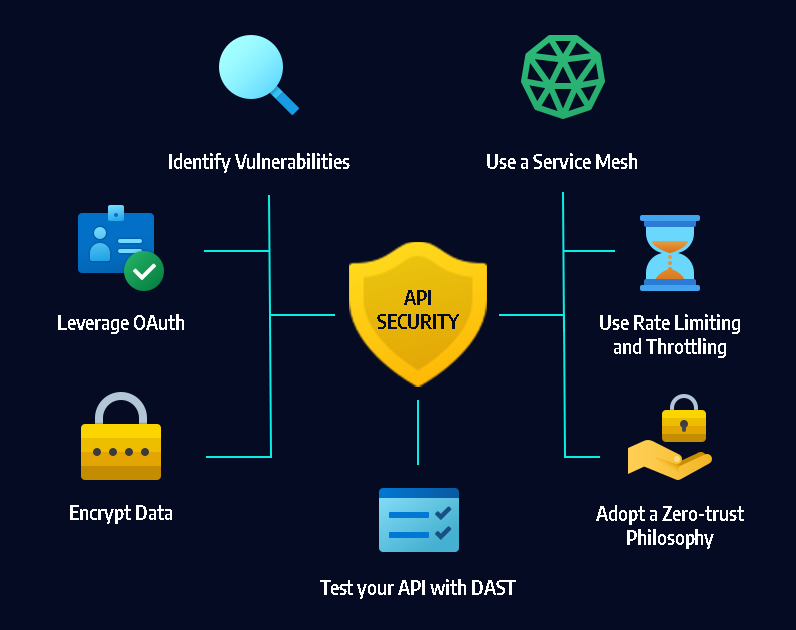
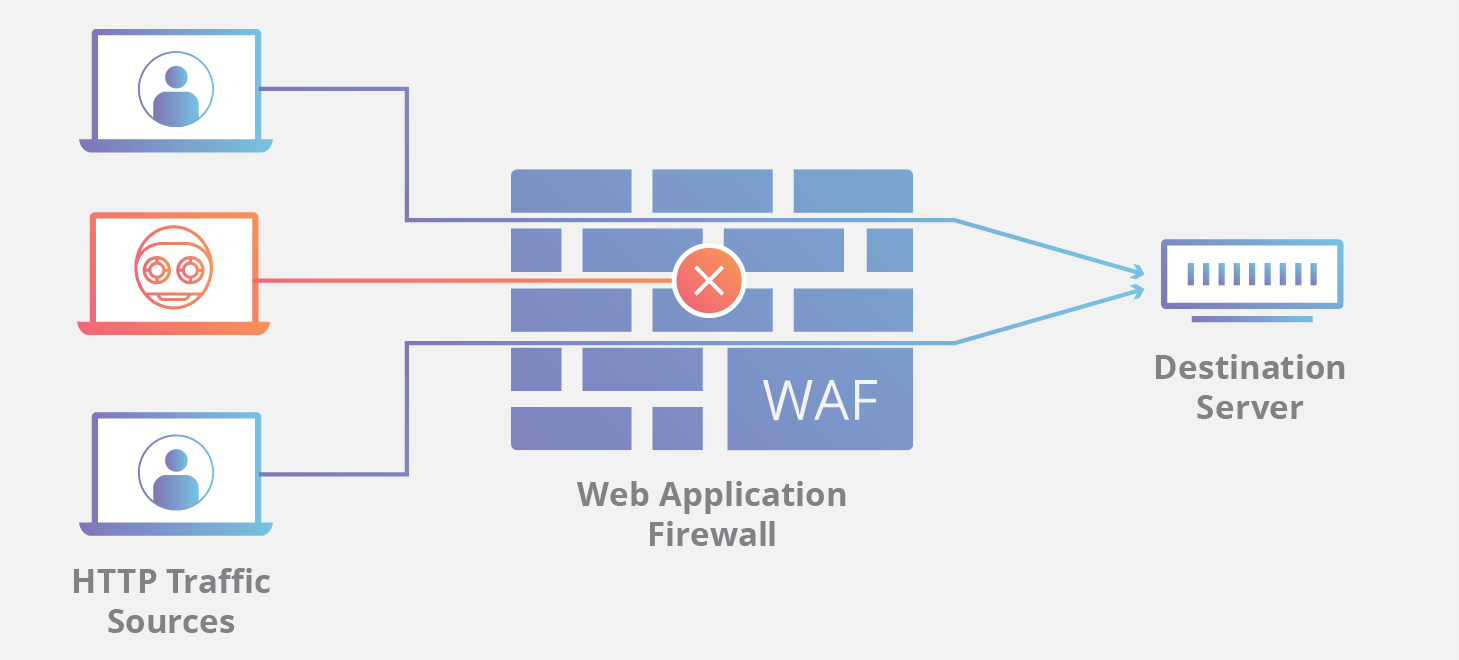
In today's digital landscape, web application security is of paramount importance. With an increasing number of cyber threats targeting web applications, it is essential to implement robust security measures to protect sensitive data and ensure the trust of users.
Web application security testing plays a crucial role in identifying vulnerabilities and weaknesses that could be exploited by attackers.
This comprehensive guide aims to demystify web application security testing by providing an easy-to-understand explanation of different testing techniques. From manual assessments to automated scanning tools, each method offers unique benefits and plays a vital role in safeguarding web applications against potential threats.
By understanding these techniques, developers and security professionals can establish a robust security posture and enhance the overall resilience of their web applications.
1. Manual Testing Techniques
Manual testing techniques involve a systematic and hands-on approach to identifying security vulnerabilities. These methods require human expertise, enabling testers to evaluate web applications comprehensively. Here are some essential manual testing techniques:
a. Penetration Testing: Also known as "ethical hacking," penetration testing involves simulating real-world attacks to uncover vulnerabilities in a controlled environment. It identifies weaknesses that automated tools may miss, providing an in-depth analysis of the application's security posture.
b. Source Code Review: Source code review involves analyzing the application's programming code to identify security flaws. This technique helps identify vulnerabilities that might arise from poor coding practices, such as SQL injection, cross-site scripting (XSS), or insecure file handling.
c. Security Code Review: Security code review involves examining the application's security-specific code components, such as authentication mechanisms, access control, and encryption. By reviewing these components, testers can ensure that proper security controls are in place.
2. Automated Testing Techniques
Automated testing techniques leverage various tools and technologies to scan web applications for vulnerabilities. These techniques are faster and can cover a broader scope compared to manual testing. Here are some commonly used automated testing techniques:
a. Vulnerability Scanning: Vulnerability scanning tools identify common vulnerabilities, such as outdated software versions, misconfigurations, or weak passwords. They scan the web application and generate reports detailing the identified issues, helping testers prioritize and address vulnerabilities effectively.
b. Web Application Scanning: Web application scanning tools simulate attacks on web applications to identify vulnerabilities. They evaluate different attack vectors, such as injection attacks, broken authentication, or insecure direct object references, and provide detailed reports with remediation steps.
c. Fuzz Testing: Fuzz testing involves sending unexpected and invalid inputs to the application to uncover potential vulnerabilities. By injecting malformed or random data, fuzz testing helps identify flaws like buffer overflows, input validation issues, or unhandled exceptions.
3. Hybrid Testing Techniques
Hybrid testing techniques combine the benefits of both manual and automated testing. They involve using automated tools to enhance the efficiency and coverage of manual testing. Here are two hybrid testing techniques:
a. Threat Modeling: Threat modeling is a proactive approach that involves identifying potential threats, assessing their impact, and designing appropriate countermeasures. Automated tools can assist in identifying common threat patterns and vulnerabilities, aiding in the creation of a robust threat model.
b. Security Testing Frameworks: Security testing frameworks provide a structured approach to web application security testing. They combine manual and automated techniques, offering a comprehensive set of guidelines, methodologies, and tools to ensure a thorough assessment of security controls.
Conclusion
Web application security testing is a crucial aspect of maintaining the security and integrity of web applications. By employing a combination of manual, automated, and hybrid testing techniques, developers and security professionals can identify and address vulnerabilities, ensuring robust protection against cyber threats. Manual techniques offer a deep dive into application security, while automated techniques provide broader coverage and quicker results. Hybrid techniques combine the strengths of both approaches to create a comprehensive testing strategy.
In an ever-evolving threat landscape, it is crucial to stay up-to-date with the latest security testing techniques and best practices. Regular security testing, combined with proactive measures like secure coding practices and timely patching, will help maintain a robust security posture for web applications and protect sensitive user data. By understanding and implementing the various web application security testing techniques, businesses can mitigate risks, enhance their reputation, and establish trust with their users in the digital realm.