Web Penetration Testing - Vulnerability

Achieving Cybersecurity Maturity with NIST Framework in Critical Infrastructure Organizations
August 2, 2023
Exploiting Insecure Deserialization in Web Applications
July 20, 2023

Zero-Day Vulnerabilities: Web Application Exploitation
June 21, 2023
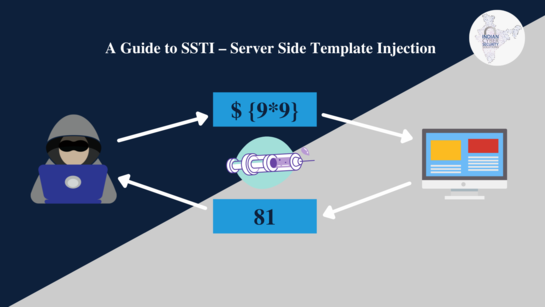
Server-Side Template Injection (SSTI): Exploitation Techniques
July 15, 2023

Anatomy of a Web Penetration Test: Step-by-Step Process
July 14, 2023
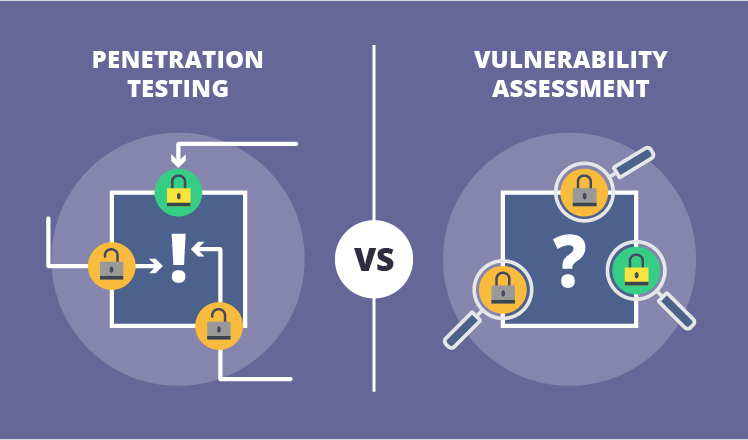
Vulnerability Assessment vs. Penetration Testing: What's the Difference?
July 13, 2023

Web Application Security Scanning Tools: A Comparative Analysis
July 12, 2023
Remote File Inclusion (RFI) and Local File Inclusion (LFI) Attacks
July 11, 2023

Exploiting File Upload Vulnerabilities in Web Applications
July 10, 2023

What is security misconfiguration in OWASP?
July 7, 2023

Directory Traversal Attack Case Study
July 7, 2023
What is a cross-site scripting (XSS) attack? What is the purpose of attackers?
July 5, 2023

Protecting Your Wireless Network Against Cyber Attacks
May 12, 2023
Assessing the Security of Cloud Environments
May 13, 2023

Twitter Data Breach
May 24, 2023

Suzuki Data Breach Forces Plant Shutdown
May 25, 2023

Shein Data Breach: What You Need to Know
May 31, 2023

Network Penetration Testing For Weaknesses
May 11, 2023

Automating Metasploit with Pymetasploit3 in Continuous Integration
May 8, 2023

Threat Modelling For Web Penetration Testing: Assessing Risks And Impact
June 1, 2023

How Can We Automate Penetration Testing In Order To Improve Network Security
June 2, 2023

What Priority Is Looking For Security Vulnerabilities In The Packages And Libraries?
June 3, 2023

CVE-2022-34265 Exploit Step-by-Step
June 9, 2023

North Korean Hackers Breach Hospital in Seoul, Threatening Data Security
June 13, 2023