Web Penetration Testing - Web Application Firewall (waf)

DOM-Based XSS Attacks: Detection and Prevention
July 27, 2023
Server-Side Request Manipulation: Exploitation Techniques
July 16, 2023

Business Logic Flaws in Web Applications: Detection and Exploitation
July 24, 2023

Web Application Security Scanning Tools: A Comparative Analysis
July 12, 2023
Remote File Inclusion (RFI) and Local File Inclusion (LFI) Attacks
July 11, 2023

XML External Entity (XXE) Attacks
July 11, 2023

Exploiting File Upload Vulnerabilities in Web Applications
July 10, 2023
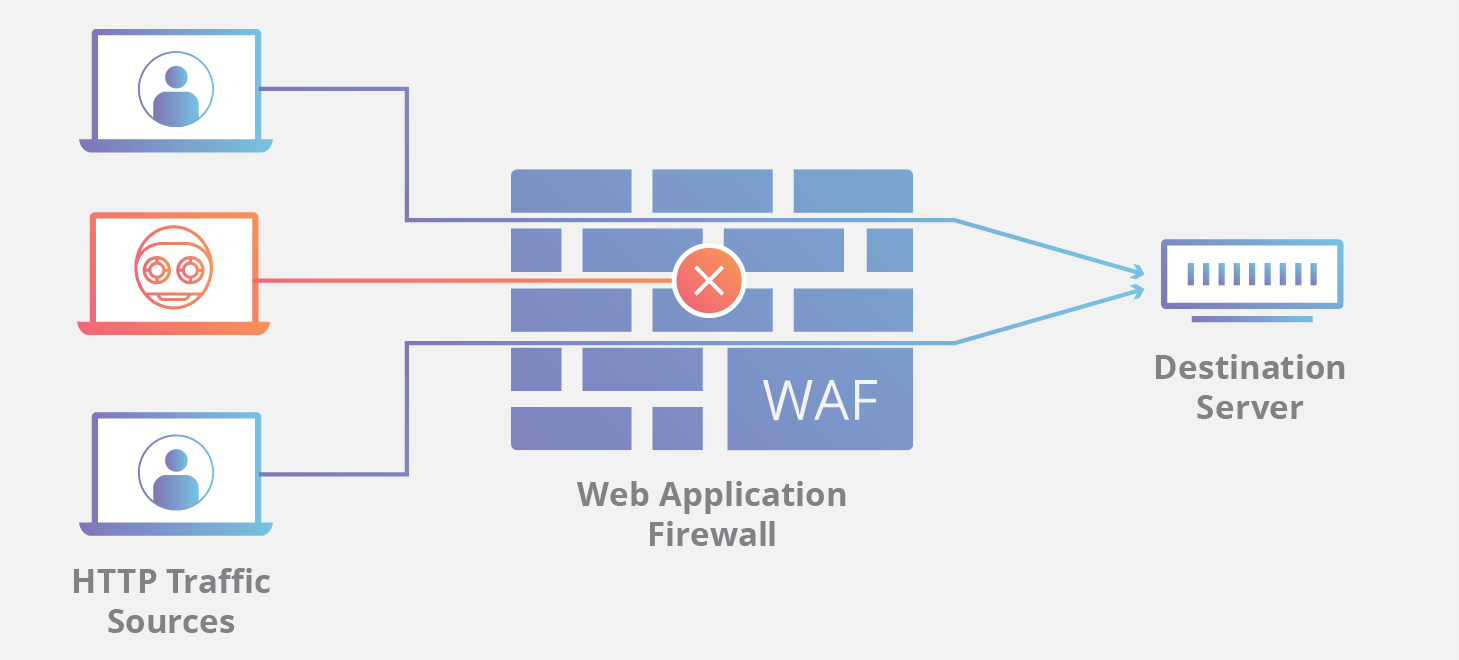
Web Application Firewalls (WAFs): How They Work and Their Limitations
July 8, 2023
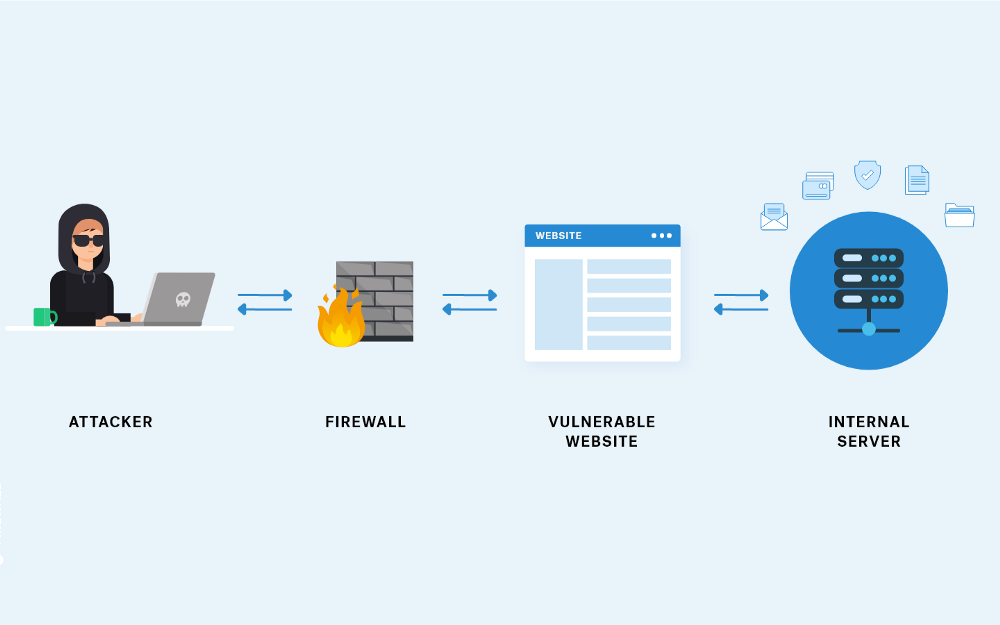
Server-Side Request Forgery (SSRF) Exploitation in Cloud Metadata Services
July 8, 2023

Directory Traversal Attack Case Study
July 7, 2023
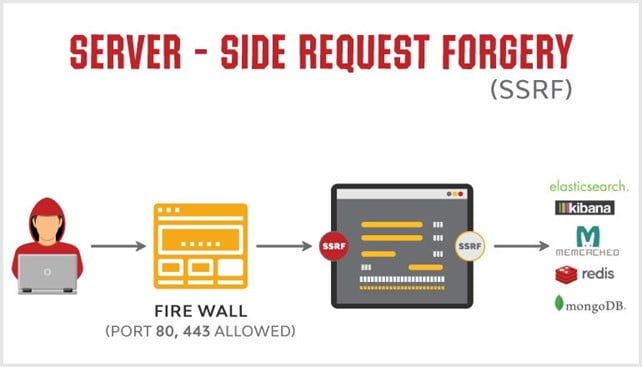
What is a Server-Side Request Forgery (SSRF) and how can they be prevented?
July 6, 2023

CVE-2022-34265 Exploit Step-by-Step
June 9, 2023