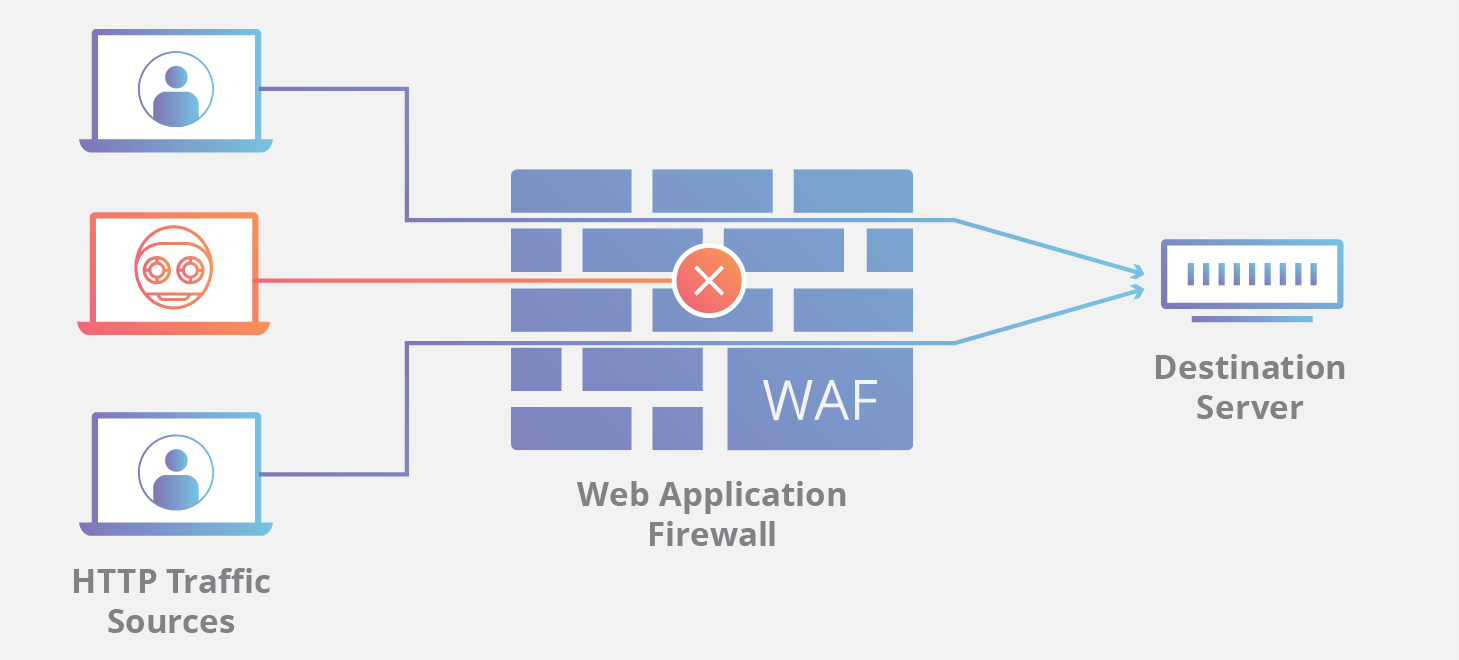
Web application firewalls (WAFs) are security appliances or software that monitor web traffic for malicious activity and block attacks. WAFs are designed to protect web applications from a variety of common attacks, including cross-site scripting (XSS), SQL injection, and denial-of-service (DoS) attacks.
How WAFs Work
WAFs work by inspecting HTTP traffic between a web application and the internet. They use a set of rules to identify malicious traffic and block it before it reaches the web application. These rules are typically based on known attack patterns, but they can also be customized to protect against specific threats.
The rules that a WAF uses to identify malicious traffic are typically based on one of two methods:
Signature-based detection: This method uses a database of known attack signatures to identify malicious traffic. When a WAF sees traffic that matches a signature, it blocks it.
Behavioral detection: This method uses statistical analysis to identify malicious traffic that does not match any known signatures. This type of detection is more difficult to bypass by attackers, but it can also generate more false positives.
Limitations of WAFs
WAFs are an important part of a layered security approach to web application protection, but they are not a silver bullet. WAFs can be bypassed by attackers who are using sophisticated techniques, and they can also generate false positives, which can block legitimate traffic.
Here are some of the limitations of WAFs:
They can be bypassed by attackers who are using sophisticated techniques: Attackers who are familiar with WAFs can often bypass them by using techniques such as obfuscating their attack traffic or using new attack vectors that the WAF is not aware of.
They can generate false positives: WAFs can sometimes block legitimate traffic if it matches a rule that is designed to block malicious traffic. This can lead to service disruptions for legitimate users.
They are not a replacement for other security measures: WAFs should be used as part of a layered security approach that includes other measures such as firewalls, intrusion detection systems, and application security testing.
Other Limitations of WAFs
In addition to the limitations mentioned above, WAFs also have some other limitations, including:
They can be expensive: WAFs can be a significant investment, both in terms of the hardware or software itself and the cost of maintenance and configuration.
They can be difficult to configure: WAFs can be complex to configure, and it is important to have a good understanding of web application security in order to do so effectively.
They can have a performance impact: WAFs can add overhead to the web application, which can impact its performance. This is especially true for high-traffic applications.
Conclusion
WAFs are an important part of a layered security approach to web application protection, but they are not a silver bullet. WAFs can help to prevent a wide range of attacks, but they are not perfect. It is important to understand their limitations and to use them in conjunction with other security measures.
Here are some tips for choosing and using a WAF:
Choose a WAF that is appropriate for your needs: There are a variety of WAFs available, so it is important to choose one that is right for your application and your budget.
Configure the WAF carefully: It is important to configure the WAF carefully in order to maximize its effectiveness.
Monitor the WAF for performance and accuracy: It is important to monitor the WAF for performance and accuracy to ensure that it is working properly.
Use the WAF in conjunction with other security measures: The WAF should be used in conjunction with other security measures, such as firewalls, intrusion detection systems, and application security testing.
By following these tips, you can help to ensure that your web application is protected from attack.




