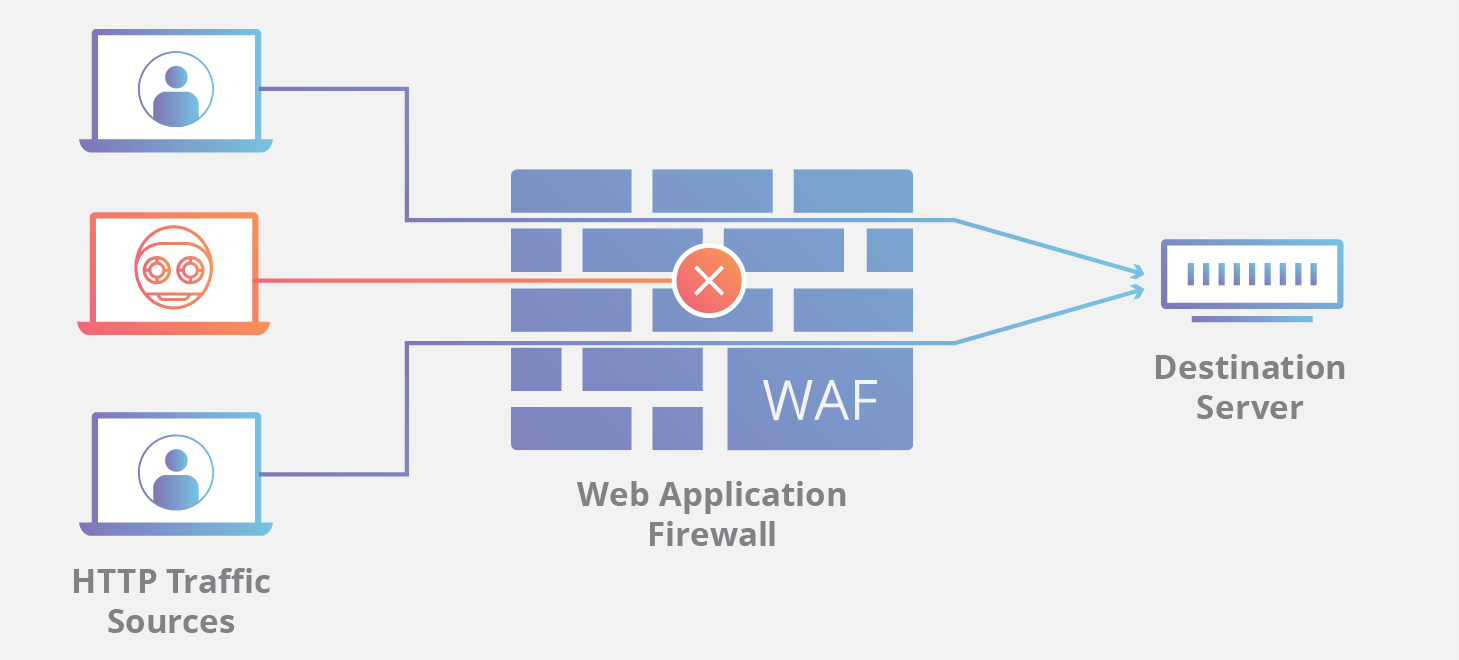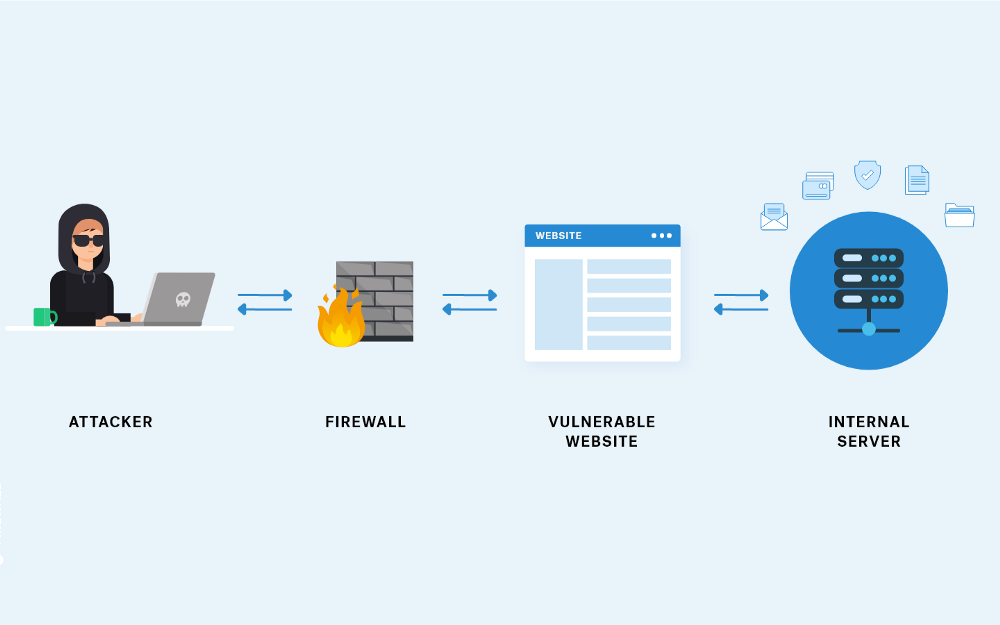
In today's rapidly evolving digital landscape, web applications play a crucial role in facilitating business operations and serving as a platform for engaging with customers. However, with the increasing complexity and sophistication of cyber threats, ensuring the security and resilience of web applications has become paramount.
This is particularly challenging in Agile development environments, where rapid iterations and frequent updates are the norm. Web penetration testing, also known as ethical hacking, is an indispensable practice that helps organizations identify vulnerabilities and weaknesses in their web applications to prevent potential security breaches.
Understanding Agile Development
To grasp the significance of web penetration testing in Agile development environments, it is essential to first understand the fundamental principles of Agile. Agile is an iterative and collaborative approach to software development, emphasizing flexibility, adaptability, and customer satisfaction. Agile methodologies, such as Scrum and Kanban, enable development teams to break down complex projects into smaller, manageable tasks or user stories. These stories are then developed, tested, and released in short iterations known as sprints, promoting continuous improvement and customer feedback.
The Role of Web Penetration Testing in Agile
In Agile development environments, web penetration testing is integrated throughout the software development life cycle (SDLC) to identify security vulnerabilities, assess risks, and ensure the overall robustness of web applications. Unlike traditional waterfall approaches, Agile embraces a proactive and iterative mindset, making security an integral part of every sprint. By including penetration testing in each iteration, organizations can detect and resolve security flaws early on, preventing potential exploitation.
Key Methodologies and Best Practices
To conduct effective web penetration testing in Agile development environments, several methodologies and best practices should be employed. This section highlights some of the key approaches and considerations:
Continuous Integration and Continuous Deployment (CI/CD): Integrating security testing into CI/CD pipelines enables automated security checks at each stage of the development process, ensuring vulnerabilities are addressed before deployment.
Threat Modeling: By systematically identifying potential threats, assessing risks, and prioritizing security measures, organizations can develop a comprehensive security strategy that aligns with Agile practices.
Security Champions: Appointing security champions within Agile teams fosters a security-conscious culture, promoting collaboration, knowledge sharing, and proactive security measures throughout the development process.
Security Testing Tools: Utilizing a wide range of security testing tools, such as dynamic application security testing (DAST), static application security testing (SAST), and interactive application security testing (IAST), enables thorough assessments and identifies vulnerabilities that may be missed through manual testing alone.
Overcoming Challenges and Ensuring Success
While integrating web penetration testing in Agile development environments offers significant benefits, there are challenges to overcome. This section discusses some common challenges, such as time constraints, resource limitations, and potential conflicts between development speed and security. It also provides recommendations for addressing these challenges effectively, such as leveraging automation, involving security experts early on, and prioritizing critical vulnerabilities.
Conclusion
In an era where cyber threats are ever-present, incorporating web penetration testing into Agile development environments is essential to build secure and robust web applications. By embracing a proactive and iterative approach to security, organizations can identify vulnerabilities early on, minimize risks, and maintain the trust of their users. Successful implementation of web penetration testing requires a combination of methodologies, tools, and best practices tailored to the Agile environment. By continuously improving security measures, organizations can safeguard their web applications and adapt to evolving threats, ensuring the long-term success of their business.