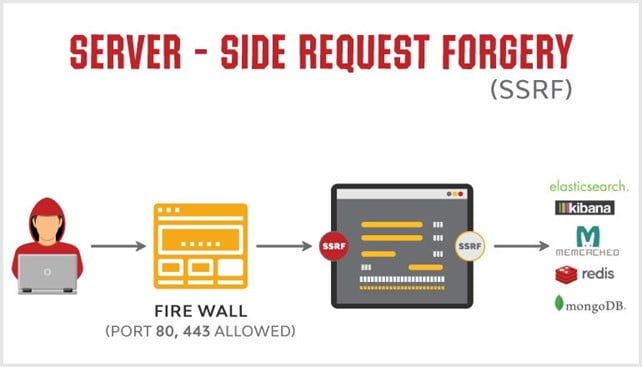
Server-side request forgery (SSRF) is a type of attack in which an attacker tricks a web application into making an unintended request to an external server. This can be used to steal sensitive information, such as database credentials, or to launch denial-of-service (DoS) attacks.
SSRF attacks are often difficult to prevent because they exploit vulnerabilities in the way that web applications handle user input. However, there are a number of steps that can be taken to reduce the risk of SSRF attacks.
How does SSRF work?
SSRF attacks exploit a vulnerability in a web application that allows user-supplied input to be used to construct HTTP requests. The attacker can then provide a malicious URL that the web application will attempt to access.
For example, an attacker could create a malicious URL that points to the internal network of the web application's host. If the web application is vulnerable to SSRF, it will attempt to access this URL, which could allow the attacker to steal sensitive information or launch a DoS attack.
How can SSRF be prevented?
There are a number of steps that can be taken to prevent SSRF attacks. These include:
Validating user input: All user-supplied input should be validated before it is used to construct HTTP requests. This validation should ensure that the input does not contain any malicious URLs. There are a number of ways to validate user input. One common way is to use regular expressions to match and remove malicious code. Another way is to use a library that has been specifically designed to validate user input.
Filtering outbound requests: Web applications should filter all outbound requests to ensure that they do not contain any malicious URLs. This can be done by using a web application firewall (WAF) or by implementing custom filtering logic. A WAF is a device or software application that is used to filter network traffic. WAFs can be configured to block malicious traffic that is associated with SSRF attacks.
Using a secure coding methodology: Web developers should use a secure coding methodology to develop web applications. This methodology should include practices that help to prevent SSRF attacks, such as input validation and outbound request filtering. There are a number of secure coding methodologies available. One popular methodology is the OWASP Secure Coding Practices.
Additional tips for preventing SSRF attacks:
Use a whitelist of allowed domains: This will prevent the web application from making requests to any domains that are not explicitly allowed.
Use a proxy server: A proxy server can be used to filter requests before they are sent to the external server.
Use a secure token: A secure token can be used to authenticate requests to the external server.
Implement rate limiting: Rate limiting can help to prevent attackers from flooding the external server with requests.
Use a sandbox: A sandbox is a restricted environment in which web applications can run. This can help to prevent SSRF attacks by limiting the amount of damage that an attacker can cause.
Use a honeypot: A honeypot is a decoy system that is designed to attract attackers. This can help to identify and mitigate SSRF attacks by providing attackers with a fake target.
Use a security information and event management (SIEM) system: A SIEM system can be used to monitor web applications for suspicious activity. This can help to detect SSRF attacks early on, before they can cause any damage.
Conclusion
SSRF is a serious security threat that can be exploited to steal sensitive information or launch DoS attacks. By following the steps outlined above, web developers and website owners can help to prevent SSRF attacks.




