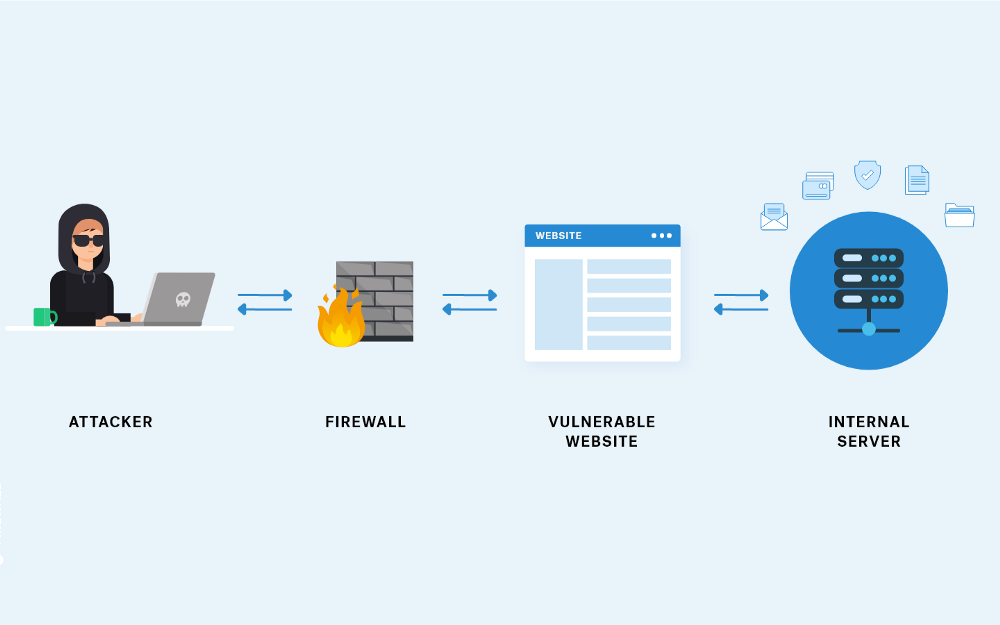
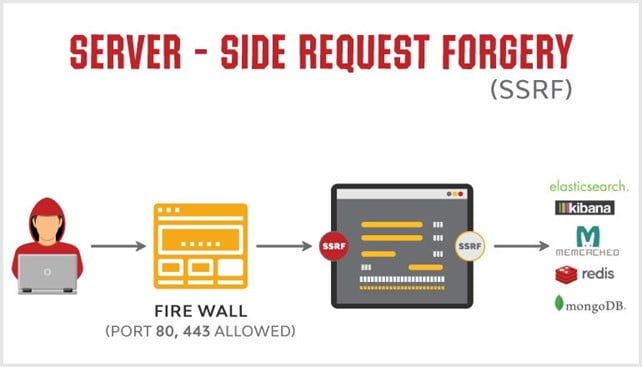
In today's interconnected digital world, where software forms the backbone of numerous applications and systems, ensuring their security is paramount. One crucial aspect of this process involves identifying and addressing vulnerabilities present in the packages and libraries used by developers. These third-party components play a pivotal role in software development, but they can also introduce security risks if not properly scrutinized.
This article delves into the critical task of prioritizing security and explores the comprehensive process of identifying vulnerabilities in packages and libraries. By understanding the significance of this endeavor, we can appreciate the complexities involved and the strategies employed to effectively manage and mitigate risks.
Understanding the Importance of Identifying Vulnerabilities
The increasing reliance on third-party software packages and libraries brings numerous benefits to developers, such as accelerated development timelines, code reusability, and access to specialized functionalities. However, these components often contain hidden vulnerabilities that can be exploited by malicious actors to compromise software systems.
By actively seeking out and addressing vulnerabilities in packages and libraries, developers can proactively enhance the security posture of their software. Such efforts help protect user data, maintain system integrity, prevent unauthorized access, and minimize the risk of potential breaches or attacks.
Prioritizing Vulnerabilities: The Challenge
With the extensive number of packages and libraries available, it becomes crucial to prioritize the identification and mitigation of vulnerabilities effectively. Security teams and developers face the challenge of allocating limited resources and time to tackle a vast array of potential threats.
One approach to prioritizing vulnerabilities involves considering the severity of the potential impact. The Common Vulnerability Scoring System (CVSS) provides a standardized framework for assessing the severity of vulnerabilities based on criteria such as exploitability, impact, and complexity. This system enables security teams to assign priority levels, focusing their efforts on the most critical and impactful vulnerabilities first.
Additionally, factors such as the package's popularity and usage frequency play a role in prioritization. Highly popular packages are more likely to be targeted by attackers, making their vulnerabilities of greater concern. The impact of a vulnerability on the overall software ecosystem, including downstream dependencies, is another important consideration.
Automation and tooling also aid in prioritizing vulnerabilities. By employing automated vulnerability scanners, security teams can efficiently identify potential weaknesses in packages and libraries. These tools often integrate with vulnerability databases, which provide up-to-date information on known vulnerabilities and their severity. This integration allows for a streamlined prioritization process based on the latest threat intelligence.
The Vulnerability Mitigation Process
Once vulnerabilities have been identified and prioritized, a comprehensive mitigation process is necessary to address the risks effectively. The following steps outline a typical vulnerability mitigation workflow:
Patching and Updating: Package maintainers and developers release updates and patches to address known vulnerabilities. Keeping software dependencies up-to-date is essential to ensure the latest security fixes are applied.
Dependency Management: It is crucial to track and manage software dependencies, including libraries and packages. Using dependency management tools enables developers to identify outdated or vulnerable components and replace them with secure alternatives.
Code Review and Auditing: Conducting regular code reviews and audits helps identify vulnerabilities that may have slipped through the initial scanning process. Manual review and testing are particularly valuable for uncovering logic flaws or architectural weaknesses.
Secure Development Practices: Implementing secure coding practices, such as input validation, output encoding, and access control, reduces the likelihood of introducing vulnerabilities during the development process. Training developers in secure coding principles is vital to foster a security-aware culture.
Threat Modeling: Performing threat modeling exercises allows security teams to identify potential attack vectors and prioritize security measures accordingly. By understanding the system's architecture and potential risks, mitigation efforts can be targeted effectively.
Incident Response Planning: Preparing an incident response plan helps organizations respond swiftly and effectively in the event of a security incident. Establishing clear roles, communication channels, and predefined steps ensures a coordinated and efficient response.
Conclusion
Prioritizing the identification and mitigation of vulnerabilities in software packages and libraries is crucial to safeguarding systems against potential attacks. By understanding the importance of this task and employing strategies like vulnerability prioritization, automation, and comprehensive mitigation processes, developers and security teams can enhance the security posture of their software.
Addressing vulnerabilities is an ongoing process that requires collaboration between developers, security experts, and the wider software community. Through continuous improvement, adoption of best practices, and an unwavering commitment to security, we can build robust and resilient software systems in an increasingly interconnected world.