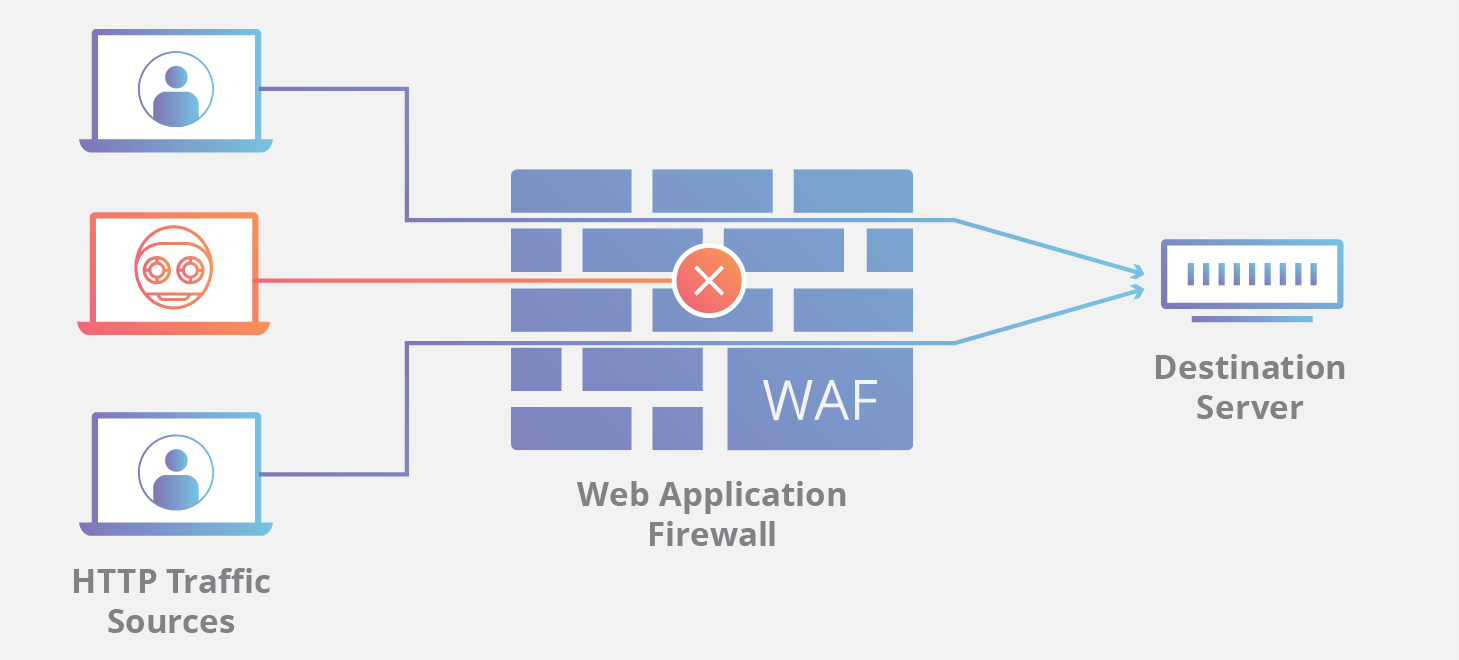
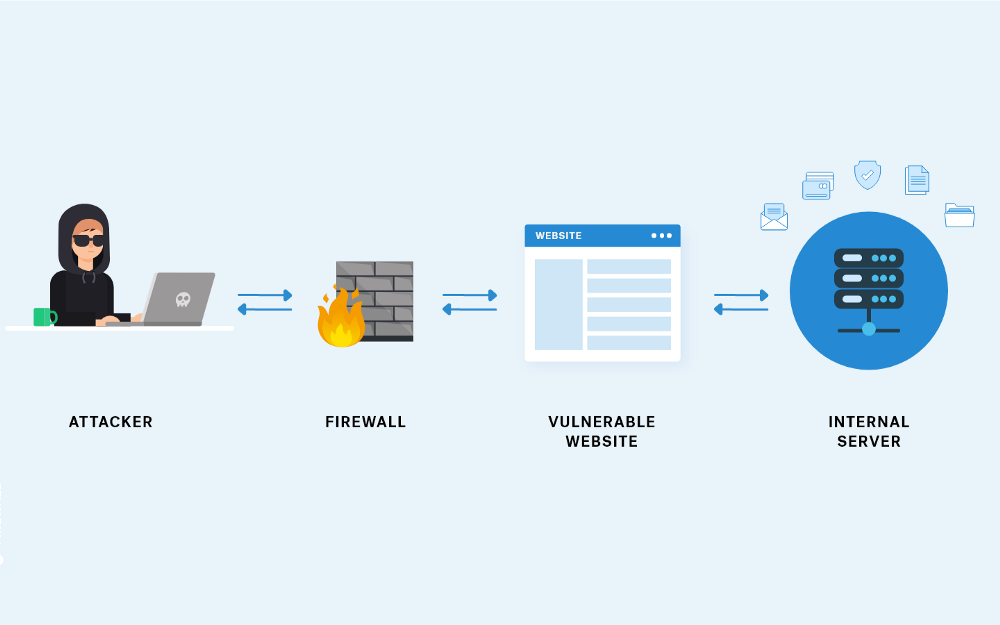
In an era dominated by technology and interconnectedness, web applications play a crucial role in various aspects of our lives. However, their increasing complexity and widespread usage make them attractive targets for malicious actors seeking to exploit vulnerabilities.
To combat this, the detection of web application vulnerabilities has become a top priority for organizations and security professionals. Thanks to advancements in automation, detecting vulnerabilities has become more efficient and effective.
In this article, we delve into the techniques used to automate the detection of web application vulnerabilities, providing a comprehensive understanding of the subject.
Static Application Security Testing (SAST)
Static Application Security Testing (SAST) is a widely used technique for automating the detection of web application vulnerabilities. It involves analyzing the source code or compiled version of an application without executing it. SAST tools examine the codebase for potential security flaws, such as SQL injection, cross-site scripting (XSS), and insecure data handling. By identifying vulnerabilities early in the development process, SAST helps developers remediate issues before they are deployed, reducing the overall risk.
Dynamic Application Security Testing (DAST)
Dynamic Application Security Testing (DAST) is another powerful technique for automating vulnerability detection. Unlike SAST, DAST analyzes the running web application by sending simulated attacks and analyzing the responses. By simulating real-world attack scenarios, DAST tools can uncover vulnerabilities that might not be apparent in the source code. This technique helps identify issues like input validation errors, weak authentication mechanisms, and session management vulnerabilities, providing a valuable perspective on an application's security posture.
Interactive Application Security Testing (IAST)
Interactive Application Security Testing (IAST) combines the benefits of SAST and DAST. It monitors the application during runtime, leveraging instrumentation techniques to capture relevant data. By analyzing code execution in real-time, IAST tools can pinpoint vulnerabilities with high accuracy, reducing false positives. This technique provides detailed insights into vulnerabilities, such as insecure library usage, information leakage, and server misconfigurations, enabling efficient remediation.
Runtime Application Self-Protection (RASP)
Runtime Application Self-Protection (RASP) is a cutting-edge technique that goes beyond detection and actively protects web applications. RASP integrates security controls directly into the application runtime environment, allowing it to detect and respond to attacks in real-time. By monitoring application behavior and implementing protective measures, RASP can mitigate vulnerabilities as they are being exploited. This technique offers proactive defense against common threats, including code injection, malicious file uploads, and session hijacking.
Machine Learning (ML) and Artificial Intelligence (AI)
Machine Learning (ML) and Artificial Intelligence (AI) are revolutionizing the field of vulnerability detection. ML algorithms can analyze vast amounts of data to identify patterns and anomalies, enabling the automated detection of complex vulnerabilities. AI-powered systems can learn from past attack data and adapt to new threats, improving accuracy and reducing false positives. These technologies can assist in identifying zero-day vulnerabilities, anomaly-based attacks, and advanced evasion techniques.
Conclusion
Automating the detection of web application vulnerabilities has become crucial in the face of ever-evolving threats.
Techniques such as Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), Interactive Application Security Testing (IAST), and Runtime Application Self-Protection (RASP) play a vital role in identifying vulnerabilities throughout the development lifecycle.
Additionally, the integration of Machine Learning (ML) and Artificial Intelligence (AI) brings further advancements, enabling the detection of complex and emerging vulnerabilities. By embracing these techniques and staying updated with the latest advancements, organizations can enhance the security of their web applications and protect sensitive data from potential breaches.