Web Penetration Testing - Authentication

Building a Resilient Infrastructure with NIST SP 800-171 Guidelines
August 3, 2023

Security Challenges in Serverless Architectures: Web Applications
August 1, 2023

Security Considerations for RESTful Web Services
July 31, 2023
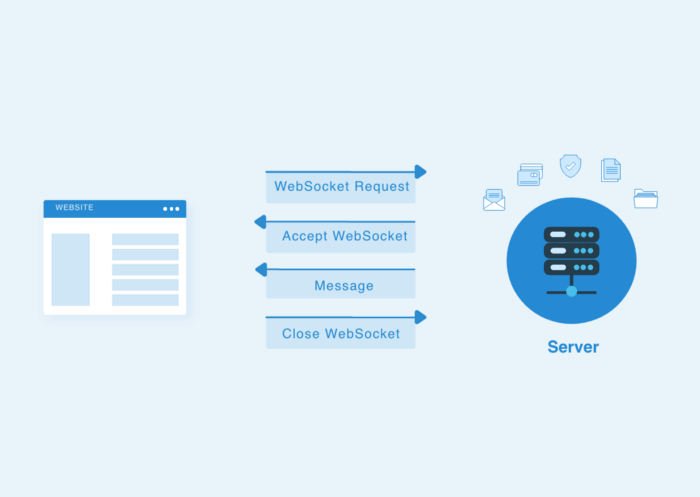
WebSocket Hijacking: Techniques and Countermeasures
July 31, 2023

Assessing Third-Party Web Application Security Risks
July 28, 2023
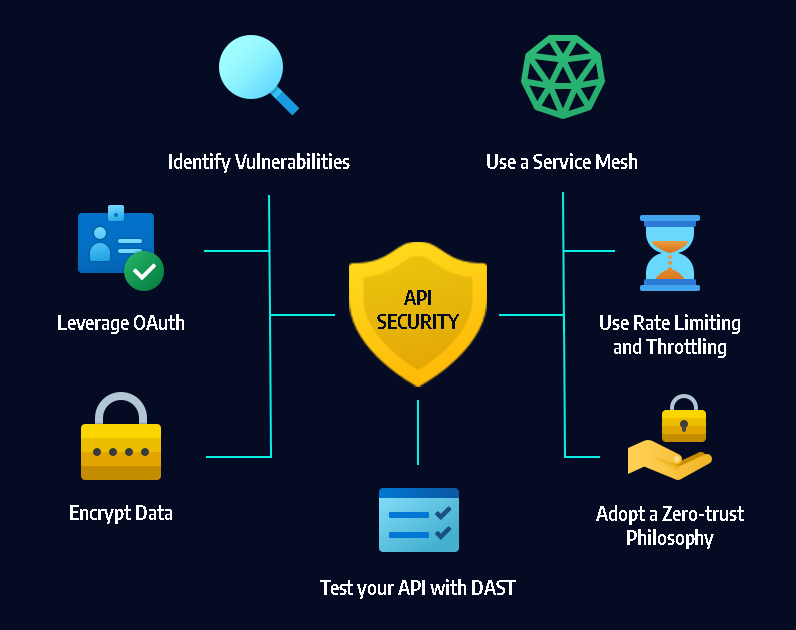
API Token Security: Risks and Recommendations
July 25, 2023

Biometric Authentication: Security Challenges in Web Applications
July 21, 2023

Secure Coding Practices for Web Developers
July 20, 2023
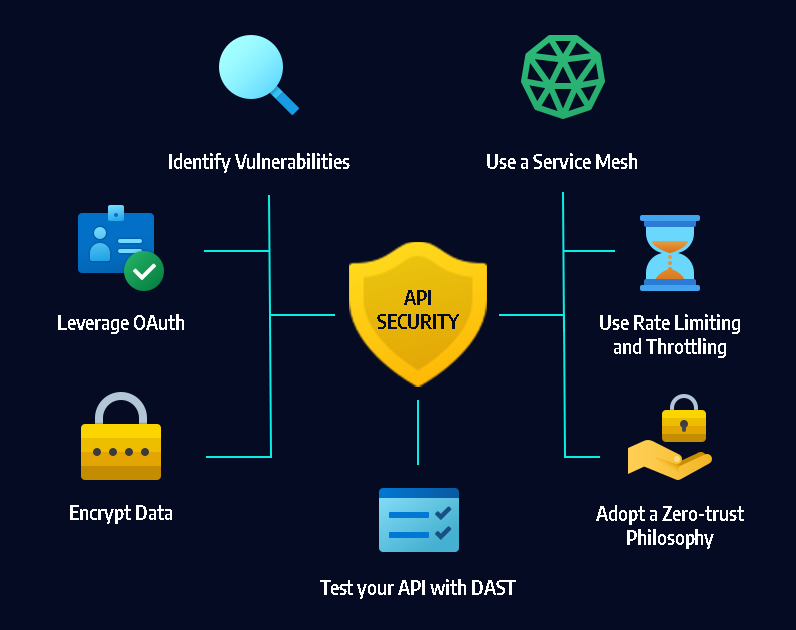
API Security Testing: Best Practices and Tools
July 12, 2023

Brute Force Attacks: Methods and Prevention in Web Applications
July 10, 2023

Social Engineering Tactics and Their Impact on Security Vulnerabilities
May 13, 2023

Power of Encryption in Safeguarding Your Digital World
May 17, 2023

Common Web Application Vulnerabilities and Exploits
July 4, 2023

The Impact of Social Engineering on Cybersecurity
July 3, 2023

Cryptocurrency Security: Best Practices for Safeguarding Your Digital Assets
July 3, 2023

Meta Platforms Inc. Announces Possible Data Breach
June 2, 2023

LastPass Hack: Understanding the Risks and Protecting Your Passwords
May 10, 2023

Best Practices For Securing Your Remote Workforce
May 9, 2023

The Importance Of Cybersecurity In The Age Of Digital Transformation
May 9, 2023

JBS Foods Ransomware Attack: Everything You Need To Know
May 8, 2023

Uber Data Breach Exposes Driver and Passenger Data
June 5, 2023

Emerging Technologies And Their Implications On Data Breach Prevention
June 8, 2023

The Most Common Cybersecurity Mistakes
June 27, 2023

How to Protect Your Data in the Cloud
June 26, 2023

The Best Password Managers for 2023
June 23, 2023

CVE-2022-34265 Exploit Step-by-Step
June 9, 2023
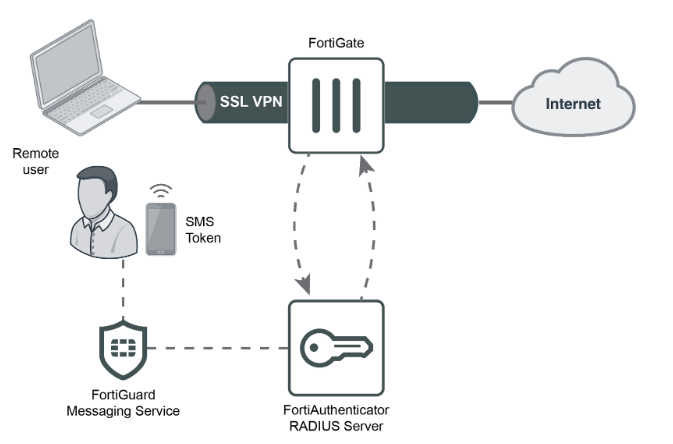
Fortinet FortiGate SSL VPN Alert
June 12, 2023

Securing the Internet of Medical Things (IoMT)
June 17, 2023