Web Penetration Testing - Cyber Threats

Achieving Cybersecurity Maturity with NIST Framework in Critical Infrastructure Organizations
August 2, 2023
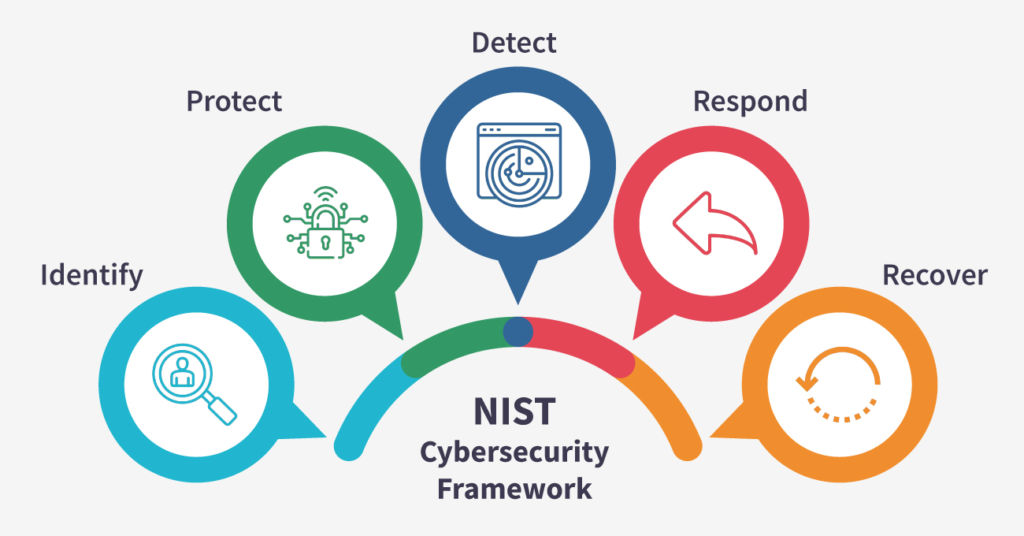
A Primer on NIST Cybersecurity Framework: Enhancing Organizational Security
July 28, 2023

Business Logic Flaws in Web Applications: Detection and Exploitation
July 24, 2023

Zero-Day Vulnerabilities: Web Application Exploitation
June 21, 2023

Secure Coding Practices for Web Developers
July 20, 2023

Understanding The Dark Web And Its Role In Cybercrime
May 9, 2023

Cybersecurity in the Post-COVID World: Lessons Learned and Future Predictions
May 6, 2023

How to Develop a Cybersecurity Incident Response Plan for Your Business
May 6, 2023

The Most Common Cybersecurity Mistakes
June 27, 2023

How Can We Automate Penetration Testing In Order To Improve Network Security
June 2, 2023