Web Penetration Testing - Cybersecurity

Building a Resilient Infrastructure with NIST SP 800-171 Guidelines
August 3, 2023
Ensuring Sustainable ISO 27001 Compliance: Challenges and Solutions
August 3, 2023

Achieving Cybersecurity Maturity with NIST Framework in Critical Infrastructure Organizations
August 2, 2023

Assessing Third-Party Web Application Security Risks
July 28, 2023
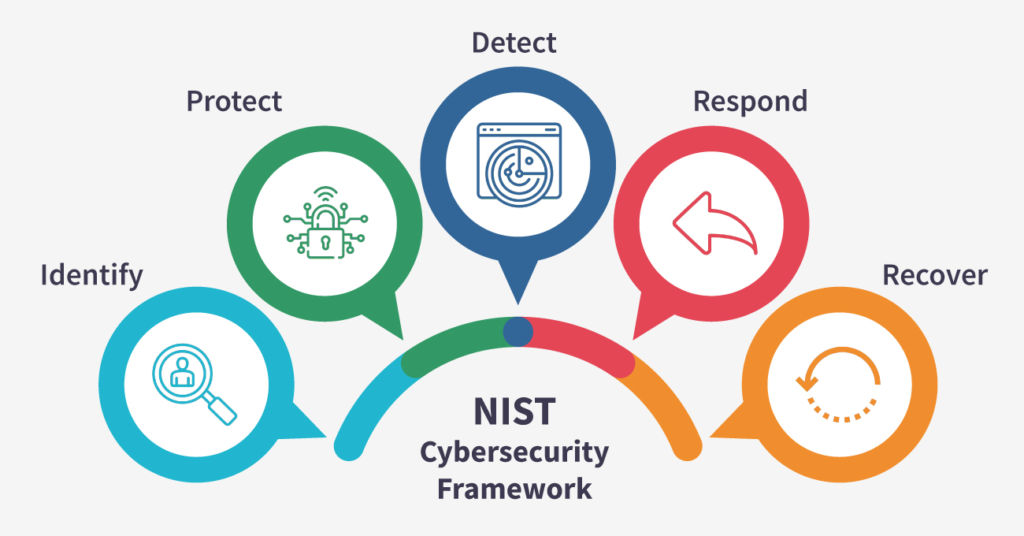
A Primer on NIST Cybersecurity Framework: Enhancing Organizational Security
July 28, 2023

Clickjacking Attacks: Techniques and Mitigation
July 19, 2023

Social Engineering Tactics and Their Impact on Security Vulnerabilities
May 13, 2023

Collecting Volatile Data and Identifying Attack Patterns through Forensic Analysis
May 15, 2023

AirAsia Data Breach: What You Need to Know
May 27, 2023

Best ways to learn web penetration testing, ethical hacking, and IT security
July 4, 2023

Network Penetration Testing For Weaknesses
May 11, 2023

The Future of Ransomware
May 11, 2023

Ransomware and the Supply Chain
May 10, 2023

The Importance Of Cybersecurity In The Age Of Digital Transformation
May 9, 2023

Top Cybersecurity threats facing businesses in 2023
May 9, 2023

JBS Foods Ransomware Attack: Everything You Need To Know
May 8, 2023
Understanding the Psychology of Cybercriminals
May 5, 2023
The NotPetya Ransomware Attack: A Case Study in Destructive Malware
May 8, 2023

Cybersecurity in the Post-COVID World: Lessons Learned and Future Predictions
May 6, 2023

How to Develop a Cybersecurity Incident Response Plan for Your Business
May 6, 2023

Role of AI in Cybersecurity: Opportunities & Challenges
May 5, 2023

The Ethics of Hacking and the Future of the Cybersecurity Industry
May 5, 2023

Emerging Technologies And Their Implications On Data Breach Prevention
June 8, 2023
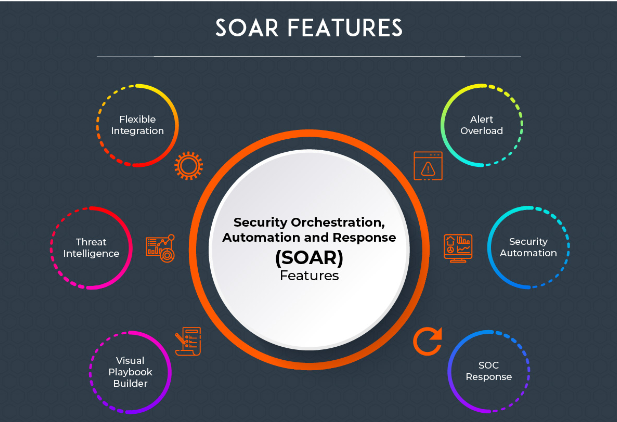
The Role of Security Orchestration, Automation, and Response in Cyber Defense
June 21, 2023

The Most Common Cybersecurity Mistakes
June 27, 2023

Cybersecurity Careers: Exploring the Path to a Lucrative and In-Demand Field
July 1, 2023

Cybersecurity Compliance 101: Understanding Regulations and Standards
July 1, 2023

Cybersecurity Culture: Engaging Employees as the First Line of Defense
June 22, 2023

Advantages And Disadvantages Of Penetration Testing
June 6, 2023

Nelnet Servicing Breach Exposes Data of 2.5 Million Student Loan Accounts
June 10, 2023

DarkBERT: Shining a Light on the Dark Side of the Internet
June 12, 2023

North Korean Hackers Breach Hospital in Seoul, Threatening Data Security
June 13, 2023

Securing the Internet of Medical Things (IoMT)
June 17, 2023

Exploring Cybersecurity Frameworks: NIST, ISO 27001, and Beyond
June 16, 2023