Web Penetration Testing - Detect

Achieving Cybersecurity Maturity with NIST Framework in Critical Infrastructure Organizations
August 2, 2023
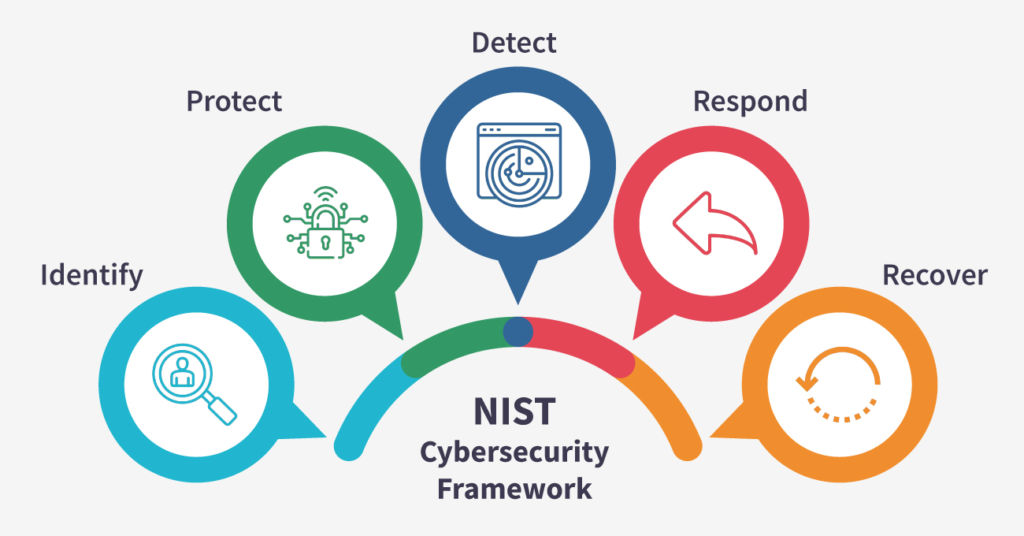
A Primer on NIST Cybersecurity Framework: Enhancing Organizational Security
July 28, 2023

Business Logic Flaws in Web Applications: Detection and Exploitation
July 24, 2023

Biometric Authentication: Security Challenges in Web Applications
July 21, 2023
Remote File Inclusion (RFI) and Local File Inclusion (LFI) Attacks
July 11, 2023

XML External Entity (XXE) Attacks
July 11, 2023
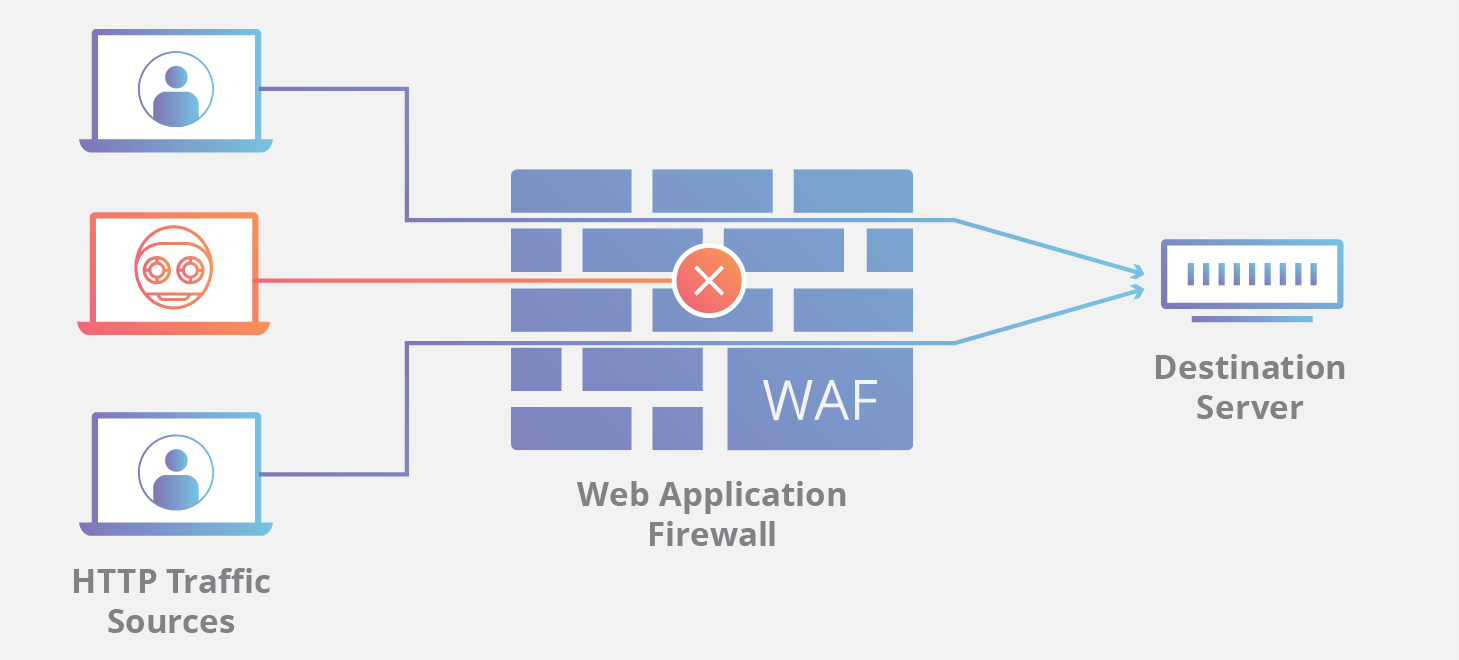
Web Application Firewalls (WAFs): How They Work and Their Limitations
July 8, 2023

Ransomware Detection Techniques Using Machine Learning
May 12, 2023

Protecting Your Wireless Network Against Cyber Attacks
May 12, 2023

Understanding Malware Behaviour through Reverse Engineering
May 15, 2023

Collecting Volatile Data and Identifying Attack Patterns through Forensic Analysis
May 15, 2023

Rising Threat of Ransomware and its Prevention By AI and Machine Learning
May 11, 2023

The Future of Ransomware
May 11, 2023

Cybersecurity in the Post-COVID World: Lessons Learned and Future Predictions
May 6, 2023

Role of AI in Cybersecurity: Opportunities & Challenges
May 5, 2023

Emerging Technologies And Their Implications On Data Breach Prevention
June 8, 2023

Dark Webathon-2023: Rally For Actionable Intelligence
June 20, 2023

STYX: The Newest Dark Web Market
June 8, 2023

Nelnet Servicing Breach Exposes Data of 2.5 Million Student Loan Accounts
June 10, 2023

North Korean Hackers Breach Hospital in Seoul, Threatening Data Security
June 13, 2023