Web Penetration Testing - Exploitation
Exploiting Insecure Deserialization in Web Applications
July 20, 2023
Server-Side Request Manipulation: Exploitation Techniques
July 16, 2023

Business Logic Flaws in Web Applications: Detection and Exploitation
July 24, 2023

Zero-Day Vulnerabilities: Web Application Exploitation
June 21, 2023
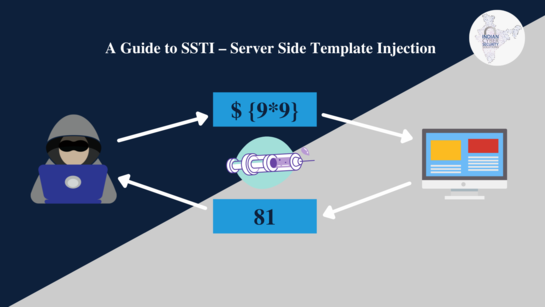
Server-Side Template Injection (SSTI): Exploitation Techniques
July 15, 2023

Mobile Application Penetration Testing: Web API Exploitation
July 14, 2023

Anatomy of a Web Penetration Test: Step-by-Step Process
July 14, 2023
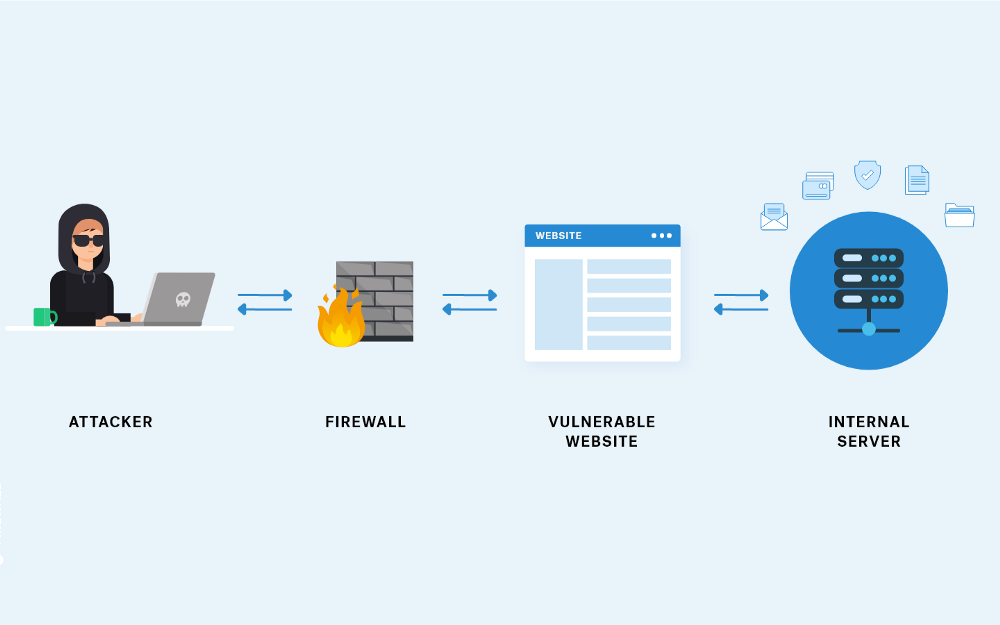
Server-Side Request Forgery (SSRF) Exploitation in Cloud Metadata Services
July 8, 2023

Dark Webathon-2023: Rally For Actionable Intelligence
June 20, 2023

Threat Modelling For Web Penetration Testing: Assessing Risks And Impact
June 1, 2023