Web Penetration Testing - Protect

Building a Resilient Infrastructure with NIST SP 800-171 Guidelines
August 3, 2023

HIPAA and Cloud Computing: Security Considerations for CISOs
August 2, 2023

Achieving Cybersecurity Maturity with NIST Framework in Critical Infrastructure Organizations
August 2, 2023
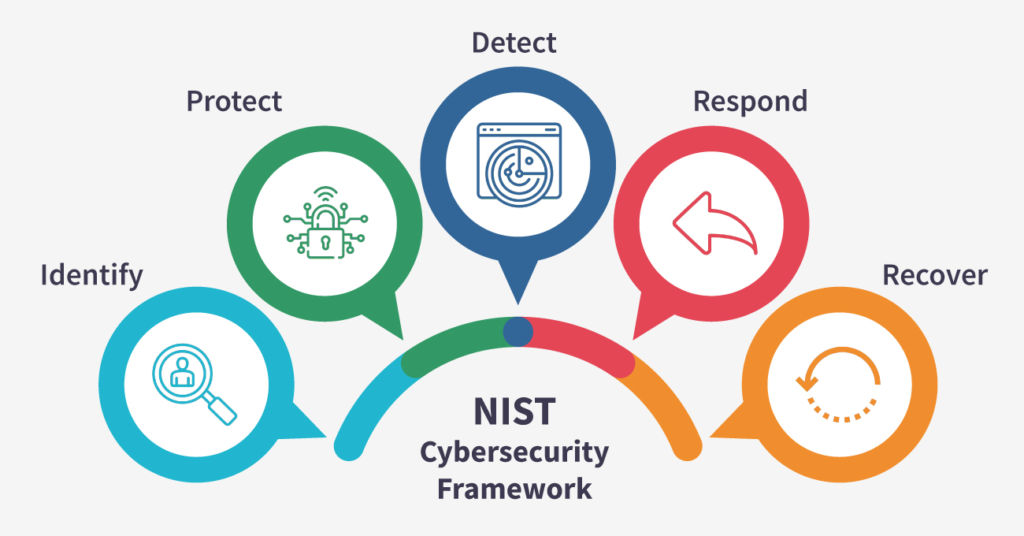
A Primer on NIST Cybersecurity Framework: Enhancing Organizational Security
July 28, 2023

Biometric Authentication: Security Challenges in Web Applications
July 21, 2023

OAuth Security: Risks and Recommendations for Web Developers
July 19, 2023

Security Headers for Web Applications: Best Practices
July 17, 2023

Hacking WordPress: Vulnerabilities and Countermeasures
July 13, 2023

Cyber Insurance: Lessons Learned and Best Practices for Coverage.
May 16, 2023
T-Mobile Data Breach Exposes Personal Information
May 22, 2023

Massive Tesla Leak Reveals Data Breaches, Thousands of Safety Complaints
May 29, 2023

The Impact of Social Engineering on Cybersecurity
July 3, 2023

Cryptocurrency Security: Best Practices for Safeguarding Your Digital Assets
July 3, 2023

Meta Platforms Inc. Announces Possible Data Breach
June 2, 2023

The Future of Ransomware
May 11, 2023

The Importance of Cyber Insurance in the Age of Ransomware
May 10, 2023

Ransomware and the Supply Chain
May 10, 2023

LastPass Hack: Understanding the Risks and Protecting Your Passwords
May 10, 2023

Understanding The Dark Web And Its Role In Cybercrime
May 9, 2023

Top Cybersecurity threats facing businesses in 2023
May 9, 2023

JBS Foods Ransomware Attack: Everything You Need To Know
May 8, 2023
Understanding the Psychology of Cybercriminals
May 5, 2023

Understanding the Importance of Cyber Insurance in Today's Business
May 6, 2023
The NotPetya Ransomware Attack: A Case Study in Destructive Malware
May 8, 2023

Major Data Breach in India Exposes COVID-19 Vaccination Data
June 14, 2023

The Importance of Data Privacy Regulations: GDPR, CCPA, and Their Impact
June 20, 2023

Dark Webathon-2023: Rally For Actionable Intelligence
June 20, 2023

How to Keep Your Kids Safe Online
June 24, 2023
Cyberbullying: A Growing Problem
June 28, 2023

The Most Common Cybersecurity Mistakes
June 27, 2023

How to Protect Your Data in the Cloud
June 26, 2023

What Technique is Used To Automate The Detection Of Web Application Vulnerabilities
May 30, 2023

Securing Cloud-Native Applications: Considerations and Best Practices
June 13, 2023