With the increasing dependence of society on technology and the internet, cybersecurity has become a crucial aspect of our daily lives. As we continue to rely on technology, the threat of cybercrime has also increased.
One of the ways to combat cybercrime is through hacking. However, hacking, despite its usefulness, raises ethical questions about the practice and the future of the cybersecurity industry.
In this blog post, we will discuss the ethics of hacking and the future of the cybersecurity industry.
What is Hacking?
Hacking is the process of finding and exploiting vulnerabilities in computer systems, networks, and software to gain unauthorized access. The term "hacker" has different meanings, depending on the context. In general, a hacker is someone who seeks to understand and modify the inner workings of computer systems, networks, and software.
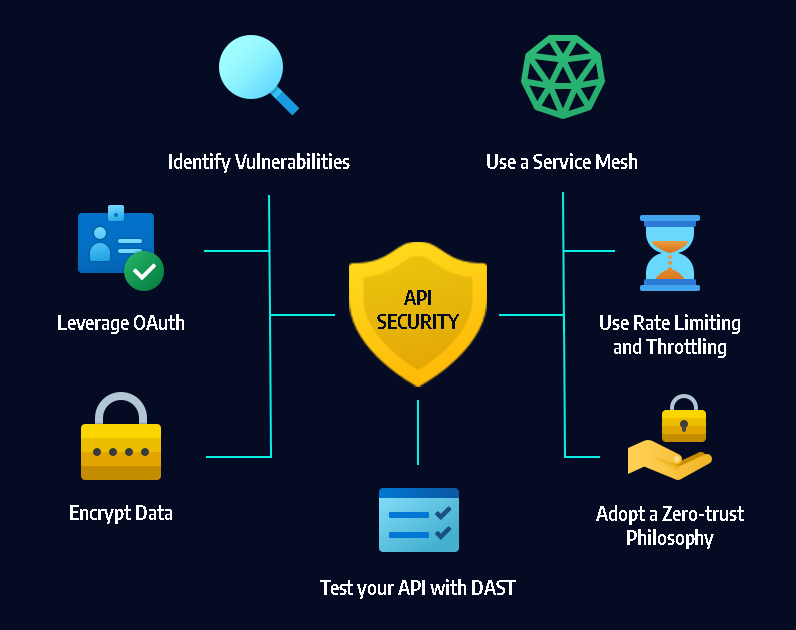
Hackers use their knowledge and skills to identify vulnerabilities and weaknesses in computer systems and networks, with the aim of improving security.
Ethics of Hacking
Hacking can be used for good or bad purposes. For instance, ethical hacking, also known as "white hat" hacking, is done with the permission of the owner of the system or network, with the aim of identifying and fixing vulnerabilities.
Ethical hacking is a legitimate and useful practice, and many organizations employ ethical hackers to test the security of their systems and networks.
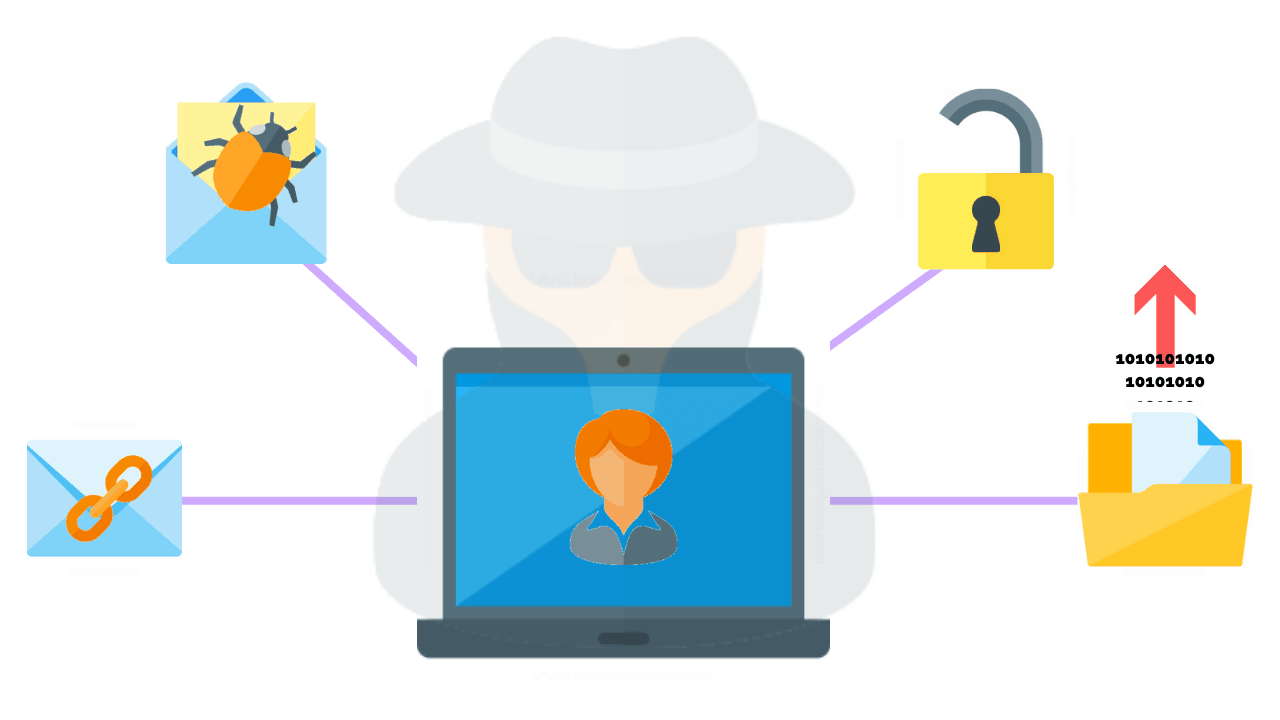
However, there are also "black hat" hackers, who use their skills and knowledge to gain unauthorized access to computer systems and networks for malicious purposes. Black hat hacking is illegal, and those who engage in it can face severe consequences.
Grey hat hacking is a form of hacking that falls between the two categories. Grey hat hackers may hack into computer systems and networks without permission, but their intentions are not necessarily malicious. Instead, they may seek to expose vulnerabilities and flaws in the system and inform the owner so that the issues can be fixed. However, grey hat hacking can still be illegal and is not always ethically justifiable.
What is Ethical Hacking
While ethical hacking is a legitimate practice, it is not always free from ethical concerns. For example, ethical hackers may uncover sensitive information during their testing, such as personal or financial data.
Ethical hackers have a responsibility to protect this information and use it only for the purpose of improving the security of the system or network. Failure to do so can result in legal and ethical repercussions.
Another ethical concern is the potential for ethical hacking to be used as a cover for illegal hacking. In some cases, black hat hackers may claim to be ethical hackers to gain access to a system or network for malicious purposes.
This highlights the importance of thorough background checks and verification of credentials for ethical hackers.
Future of the Cybersecurity Industry
The increasing threat of cybercrime has led to a growing demand for cybersecurity professionals. According to a report by Cybersecurity Ventures, there will be 3.5 million unfilled cybersecurity jobs globally by 2021.
This shortage of cybersecurity professionals highlights the importance of investing in education and training programs to produce more cybersecurity experts.
In addition to the shortage of cybersecurity professionals, the cybersecurity industry is also facing challenges from rapidly advancing technologies. Artificial intelligence, machine learning, and the Internet of Things (IoT) are all rapidly evolving and introducing new security challenges. As a result, cybersecurity professionals will need to stay up-to-date with the latest technologies and trends to remain effective.
One potential solution to the shortage of cybersecurity professionals is to develop and implement more automated cybersecurity solutions. Automated cybersecurity solutions, such as artificial intelligence and machine learning algorithms, can help to identify and respond to potential security threats more quickly and effectively than humans.
However, the effectiveness of automated cybersecurity solutions will depend on the quality of their programming and the ability to keep up with rapidly evolving security threats.
Another potential solution is to improve cybersecurity education and awareness. Cybersecurity education should be a key component of computer science and technology programs.
It should also be included in the curriculum of other fields, such as business, healthcare, and law. This will help to create a more cybersecurity-aware workforce and promote a culture of cybersecurity.
Furthermore, organizations should invest in ongoing cybersecurity training and education for their employees. This will help to ensure that employees are aware of the latest security threats and how to respond to them. It will also help to create a security-minded culture within the organization, which can help to prevent security incidents.
Lastly, there is a need for more international cooperation and coordination in cybersecurity. Cybersecurity threats are global, and they require a coordinated international response. This will involve sharing threat intelligence and best practices, developing common standards and regulations, and working together to combat cybercrime.
Conclusion
In conclusion, hacking can be a useful tool in improving cybersecurity, but it raises ethical concerns about its use. Ethical hacking is a legitimate practice that can help to improve the security of computer systems and networks.
However, it is not always free from ethical concerns, and ethical hackers have a responsibility to protect sensitive information and use it only for the purpose of improving security.
The future of the cybersecurity industry is facing significant challenges, including a shortage of cybersecurity professionals and rapidly advancing technologies. Solutions such as improving cybersecurity education and awareness, developing more automated cybersecurity solutions, and promoting international cooperation and coordination are needed to address these challenges.
As we continue to rely on technology in our daily lives, the need for strong cybersecurity measures will only increase. It is essential that we prioritize cybersecurity and work together to create a safer online environment.