Web Penetration Testing - Web Application

Best Practices for Secure File Uploads in Web Applications
August 1, 2023

Security Challenges in Serverless Architectures: Web Applications
August 1, 2023

Web Application Reconnaissance Techniques for Penetration Testing
July 29, 2023
Exploiting Insecure Deserialization in Web Applications
July 20, 2023

Assessing Third-Party Web Application Security Risks
July 28, 2023

DOM-Based XSS Attacks: Detection and Prevention
July 27, 2023
Server-Side Request Manipulation: Exploitation Techniques
July 16, 2023

Cryptographic Weaknesses in Web Applications: Attacks and Fixes
July 26, 2023

Business Logic Flaws in Web Applications: Detection and Exploitation
July 24, 2023

Server-Side JavaScript Injection: Exploitation and Defense
July 24, 2023
Importance of Secure Session Management in Web Applications
July 22, 2023

Biometric Authentication: Security Challenges in Web Applications
July 21, 2023

Zero-Day Vulnerabilities: Web Application Exploitation
June 21, 2023
Websockets Security: Threats and Countermeasures
July 20, 2023
Man-in-the-Middle (MitM) Attacks on Web Applications
July 18, 2023
Insecure Direct Object References (IDOR): Exploitation and Prevention
July 17, 2023

Security Headers for Web Applications: Best Practices
July 17, 2023
Server-Side Template Injection (SSTI): Exploitation Techniques
July 15, 2023
Exploiting Command Injection Vulnerabilities in Web Applications
July 15, 2023

Anatomy of a Web Penetration Test: Step-by-Step Process
July 14, 2023

Web Application Security Scanning Tools: A Comparative Analysis
July 12, 2023
Remote File Inclusion (RFI) and Local File Inclusion (LFI) Attacks
July 11, 2023

XML External Entity (XXE) Attacks
July 11, 2023

Exploiting File Upload Vulnerabilities in Web Applications
July 10, 2023
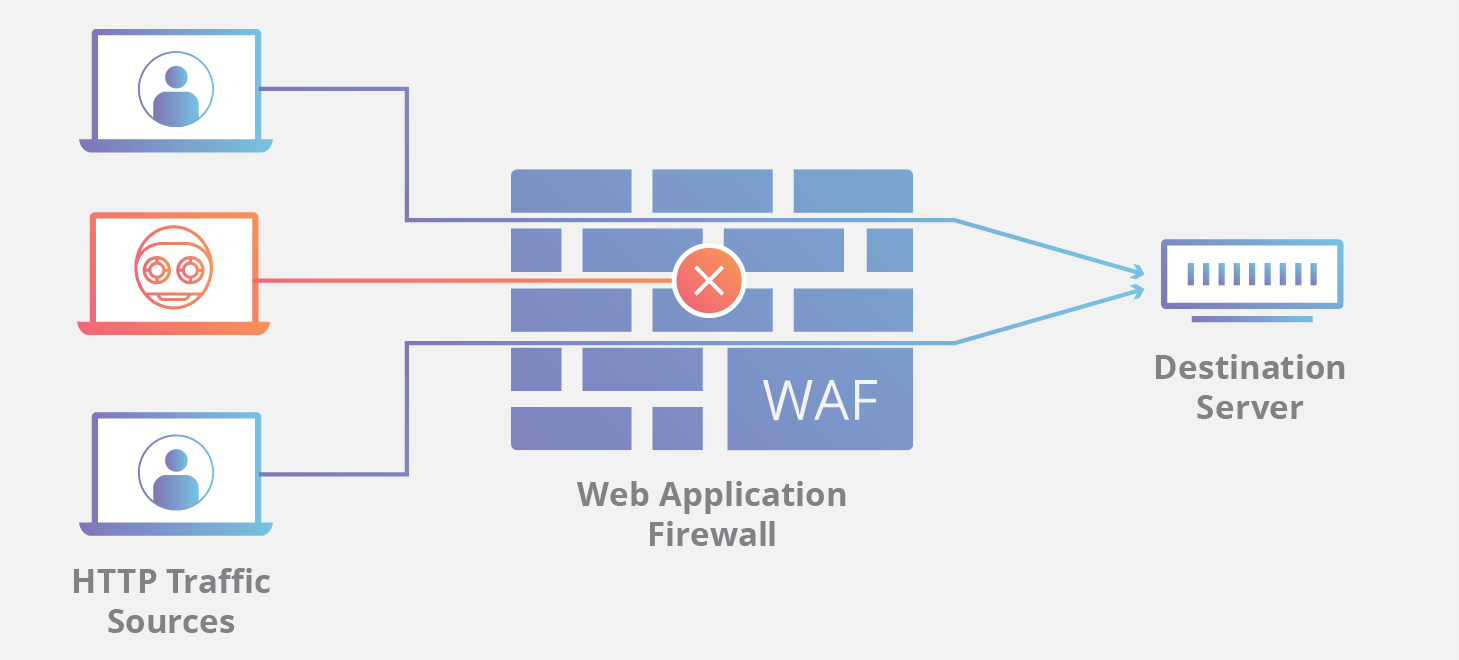
Web Application Firewalls (WAFs): How They Work and Their Limitations
July 8, 2023
Server-Side Request Forgery (SSRF) Exploitation in Cloud Metadata Services
July 8, 2023

Directory Traversal Attack Case Study
July 7, 2023
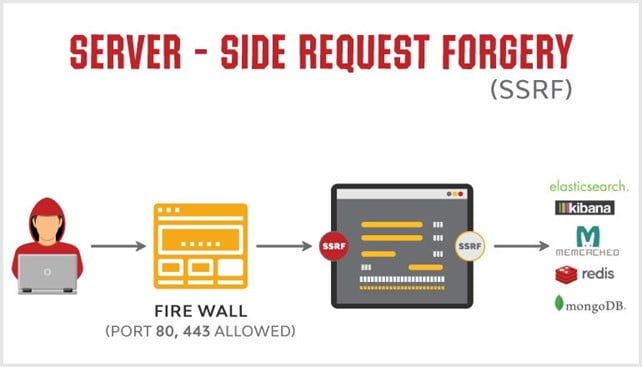
What is a Server-Side Request Forgery (SSRF) and how can they be prevented?
July 6, 2023
What is a cross-site scripting (XSS) attack? What is the purpose of attackers?
July 5, 2023
Exploring SQL Injection Attacks in Web Applications
July 5, 2023

Best ways to learn web penetration testing, ethical hacking, and IT security
July 4, 2023

Understanding Different Web Application Security Testing Techniques
June 5, 2023

Threat Modelling For Web Penetration Testing: Assessing Risks And Impact
June 1, 2023

CVE-2022-34265 Exploit Step-by-Step
June 9, 2023

What Type Of Web Application Vulnerabilities Are Humans Typically Better At Discovering
June 9, 2023