Web Penetration Testing - Attacks

Cryptographic Weaknesses in Web Applications: Attacks and Fixes
July 26, 2023

GraphQL Security: Common Vulnerabilities and Best Practices
July 25, 2023
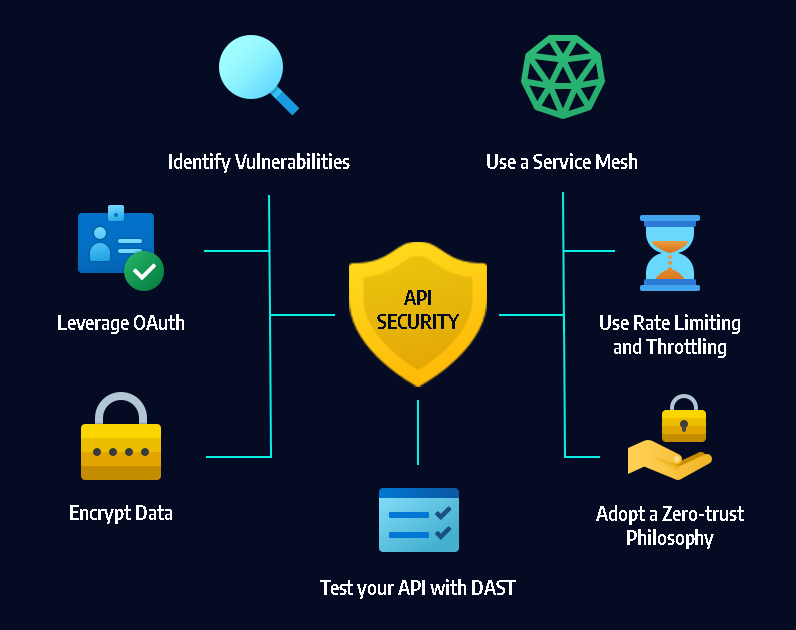
API Token Security: Risks and Recommendations
July 25, 2023
Importance of Secure Session Management in Web Applications
July 22, 2023

Biometric Authentication: Security Challenges in Web Applications
July 21, 2023
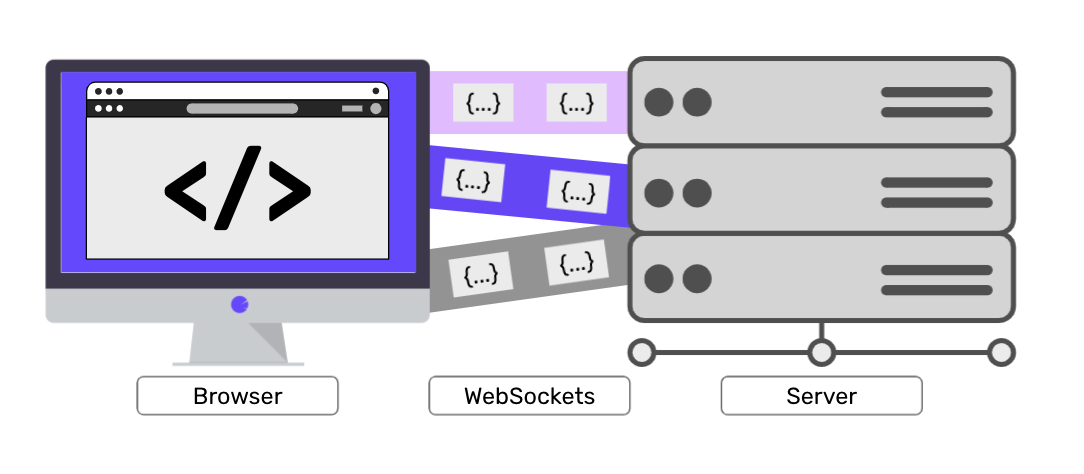
Websockets Security: Threats and Countermeasures
July 20, 2023
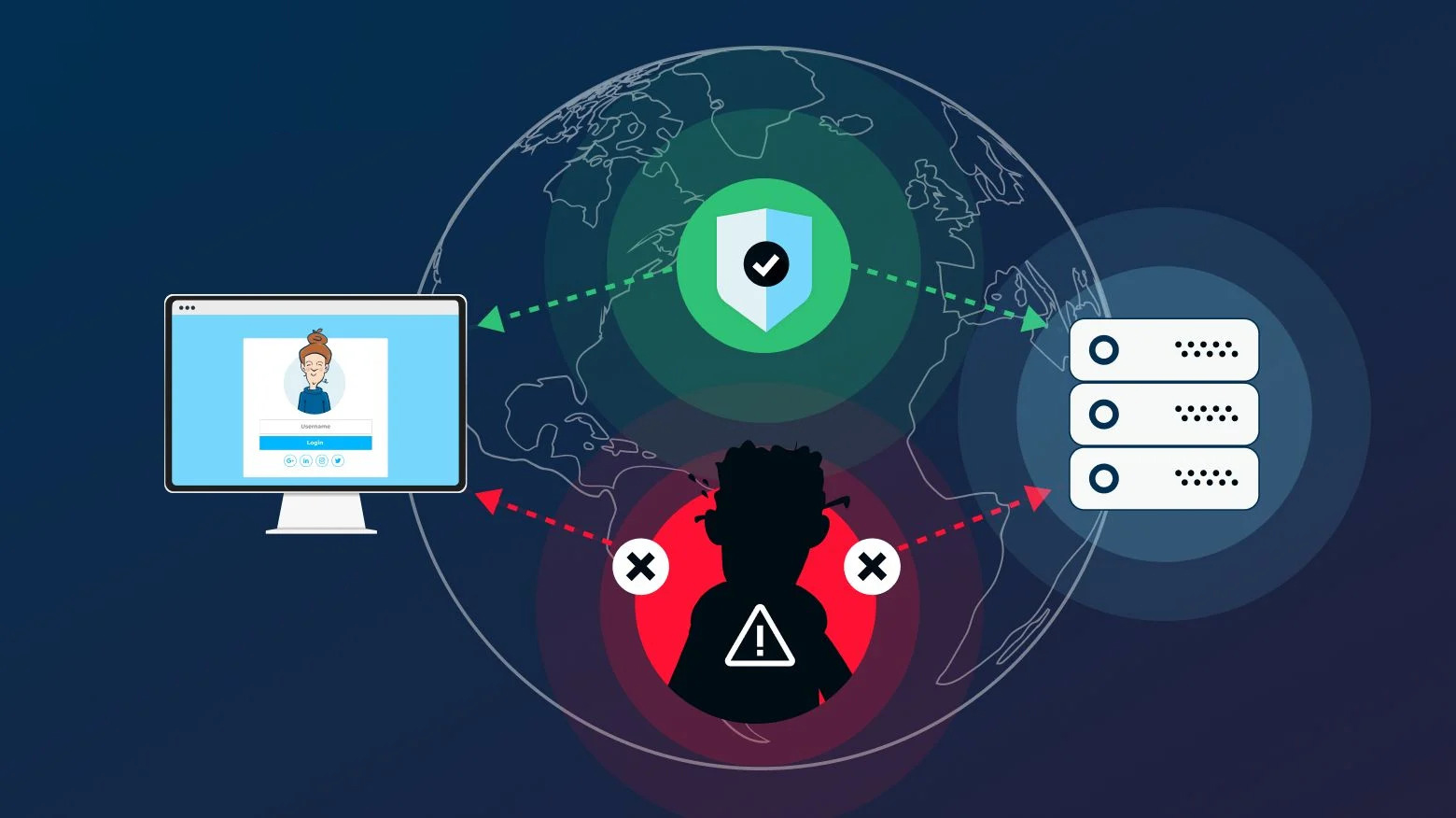
Man-in-the-Middle (MitM) Attacks on Web Applications
July 18, 2023
Exploiting Command Injection Vulnerabilities in Web Applications
July 15, 2023
Remote File Inclusion (RFI) and Local File Inclusion (LFI) Attacks
July 11, 2023

XML External Entity (XXE) Attacks
July 11, 2023
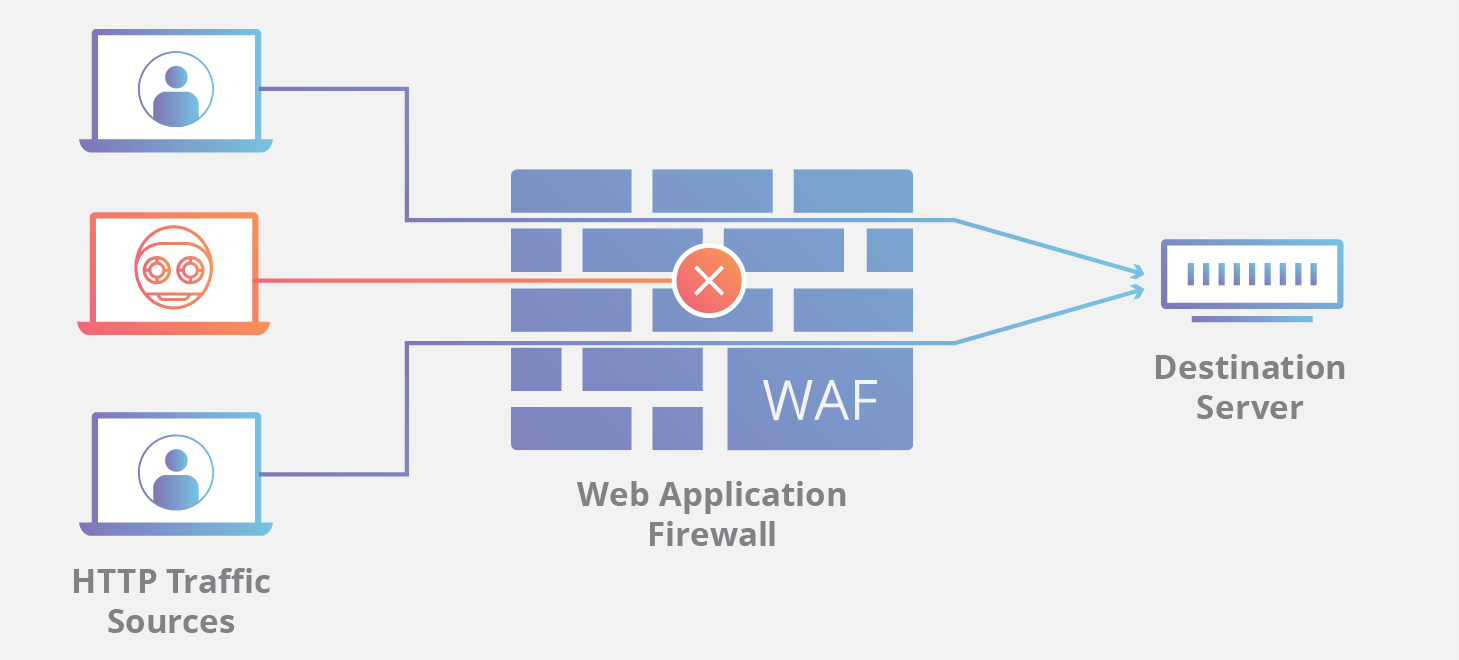
Web Application Firewalls (WAFs): How They Work and Their Limitations
July 8, 2023

Ransomware Mitigation Strategies
May 12, 2023

Protecting Your Wireless Network Against Cyber Attacks
May 12, 2023
Assessing the Security of Cloud Environments
May 13, 2023

Collecting Volatile Data and Identifying Attack Patterns through Forensic Analysis
May 15, 2023

Twitter Data Breach
May 24, 2023

Rising Threat of Ransomware and its Prevention By AI and Machine Learning
May 11, 2023

Ransomware and the Supply Chain
May 10, 2023

JBS Foods Ransomware Attack: Everything You Need To Know
May 8, 2023
Understanding the Psychology of Cybercriminals
May 5, 2023

Understanding the Importance of Cyber Insurance in Today's Business
May 6, 2023
The NotPetya Ransomware Attack: A Case Study in Destructive Malware
May 8, 2023

Role of AI in Cybersecurity: Opportunities & Challenges
May 5, 2023

What Technique is Used To Automate The Detection Of Web Application Vulnerabilities
May 30, 2023

Threat Modelling For Web Penetration Testing: Assessing Risks And Impact
June 1, 2023

What Type Of Web Application Vulnerabilities Are Humans Typically Better At Discovering
June 9, 2023
The Latest Ransomware Attacks and How to Avoid Them
June 10, 2023