Web Penetration Testing - Vulnerabilities

Best Practices for Secure File Uploads in Web Applications
August 1, 2023
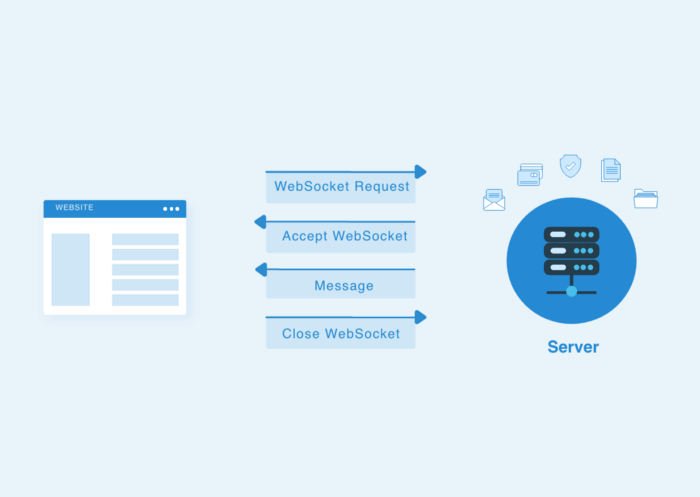
WebSocket Hijacking: Techniques and Countermeasures
July 31, 2023

Assessing Third-Party Web Application Security Risks
July 28, 2023
Server-Side Request Manipulation: Exploitation Techniques
July 16, 2023

GraphQL Security: Common Vulnerabilities and Best Practices
July 25, 2023

Business Logic Flaws in Web Applications: Detection and Exploitation
July 24, 2023

Biometric Authentication: Security Challenges in Web Applications
July 21, 2023

Zero-Day Vulnerabilities: Web Application Exploitation
June 21, 2023
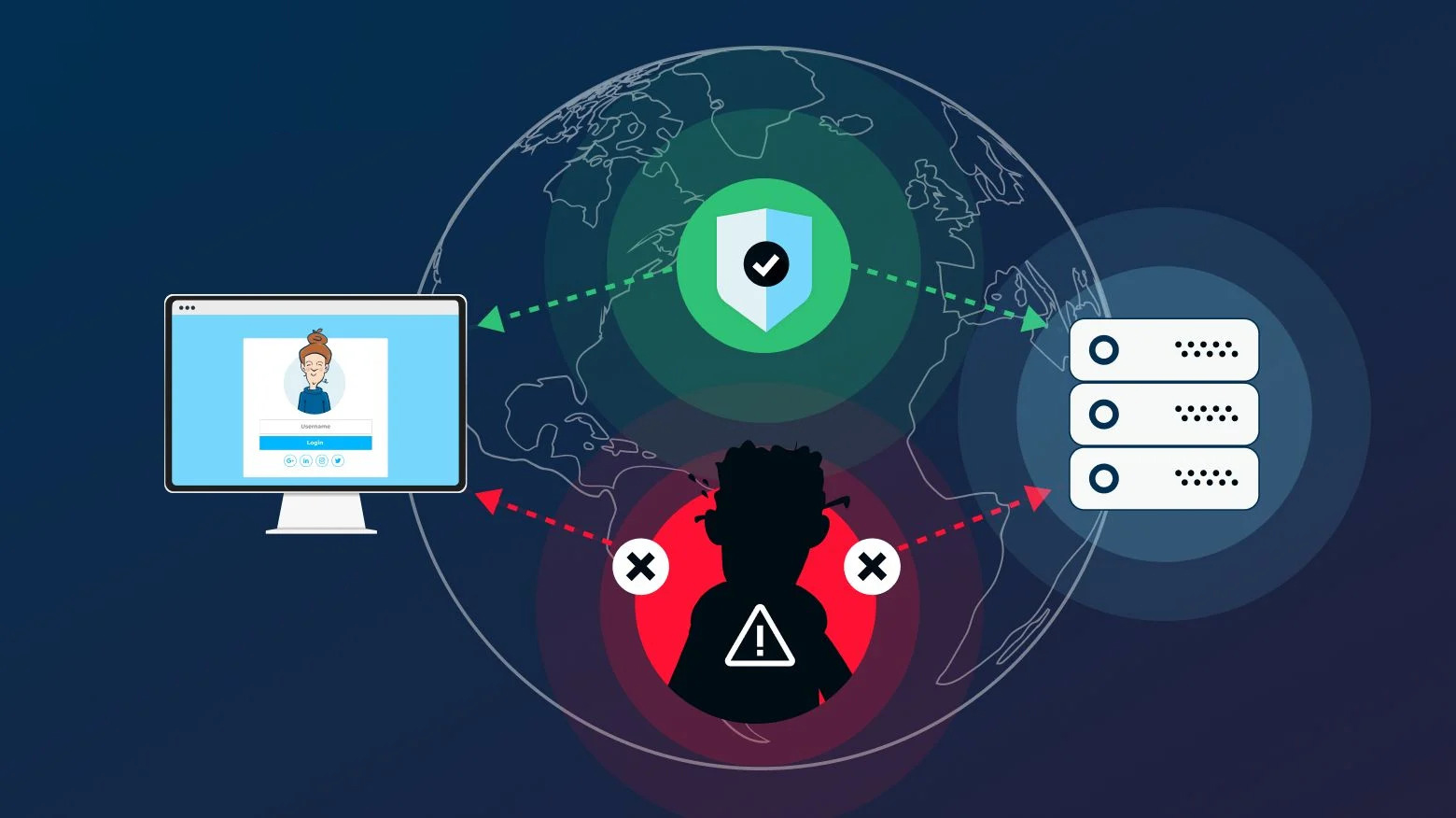
Man-in-the-Middle (MitM) Attacks on Web Applications
July 18, 2023
Insecure Direct Object References (IDOR): Exploitation and Prevention
July 17, 2023
Exploiting Command Injection Vulnerabilities in Web Applications
July 15, 2023

Mobile Application Penetration Testing: Web API Exploitation
July 14, 2023
Vulnerability Assessment vs. Penetration Testing: What's the Difference?
July 13, 2023

Hacking WordPress: Vulnerabilities and Countermeasures
July 13, 2023

Web Application Security Scanning Tools: A Comparative Analysis
July 12, 2023
API Security Testing: Best Practices and Tools
July 12, 2023

XML External Entity (XXE) Attacks
July 11, 2023

Exploiting File Upload Vulnerabilities in Web Applications
July 10, 2023
What is a Server-Side Request Forgery (SSRF) and how can they be prevented?
July 6, 2023
Exploring SQL Injection Attacks in Web Applications
July 5, 2023
Penetration Testing and Reporting Results Effectively
May 12, 2023

Protecting Your Wireless Network Against Cyber Attacks
May 12, 2023
Assessing the Security of Cloud Environments
May 13, 2023

Social Engineering Tactics and Their Impact on Security Vulnerabilities
May 13, 2023

Common Web Application Vulnerabilities and Exploits
July 4, 2023

The Importance Of Cybersecurity In The Age Of Digital Transformation
May 9, 2023

How to Protect Your Data in the Cloud
June 26, 2023

What Technique is Used To Automate The Detection Of Web Application Vulnerabilities
May 30, 2023
Web Penetration Testing In Agile Development Environments
May 31, 2023

How Can We Automate Penetration Testing In Order To Improve Network Security
June 2, 2023

What Type Of Web Application Vulnerabilities Are Humans Typically Better At Discovering
June 9, 2023

Securing the Internet of Medical Things (IoMT)
June 17, 2023