Web Penetration Testing - Security

Building a Resilient Infrastructure with NIST SP 800-171 Guidelines
August 3, 2023
Ensuring Sustainable ISO 27001 Compliance: Challenges and Solutions
August 3, 2023

HIPAA and Cloud Computing: Security Considerations for CISOs
August 2, 2023

Best Practices for Secure File Uploads in Web Applications
August 1, 2023

Security Challenges in Serverless Architectures: Web Applications
August 1, 2023

Security Considerations for RESTful Web Services
July 31, 2023
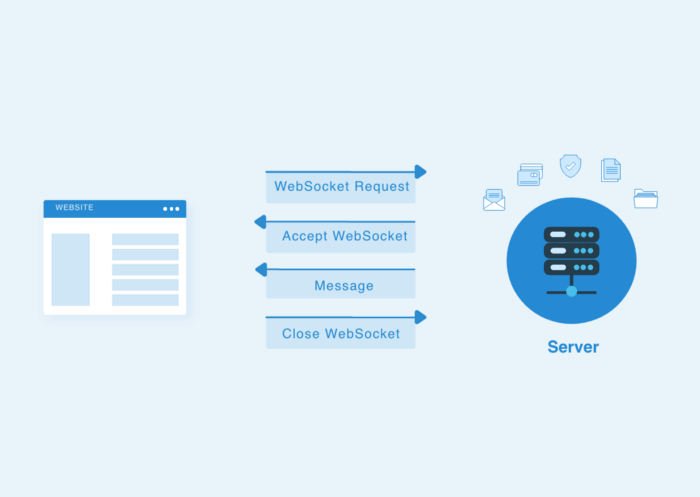
WebSocket Hijacking: Techniques and Countermeasures
July 31, 2023

Assessing Third-Party Web Application Security Risks
July 28, 2023
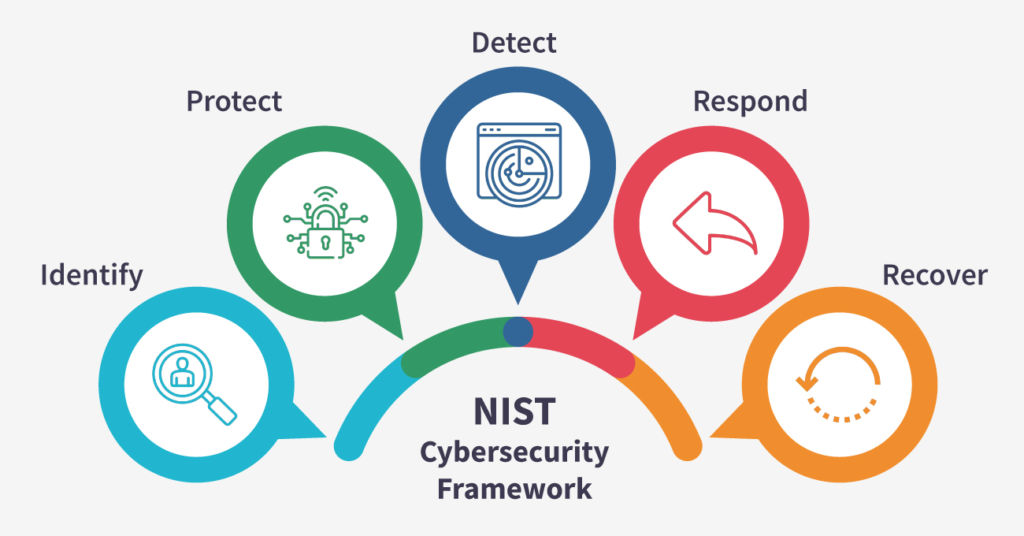
A Primer on NIST Cybersecurity Framework: Enhancing Organizational Security
July 28, 2023

DOM-Based XSS Attacks: Detection and Prevention
July 27, 2023

GraphQL Security: Common Vulnerabilities and Best Practices
July 25, 2023
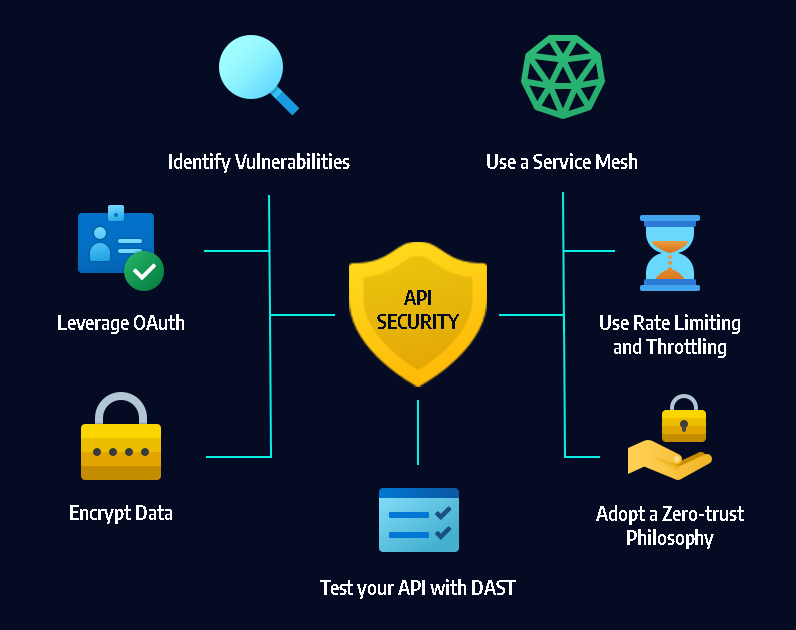
API Token Security: Risks and Recommendations
July 25, 2023

Business Logic Flaws in Web Applications: Detection and Exploitation
July 24, 2023

Server-Side JavaScript Injection: Exploitation and Defense
July 24, 2023
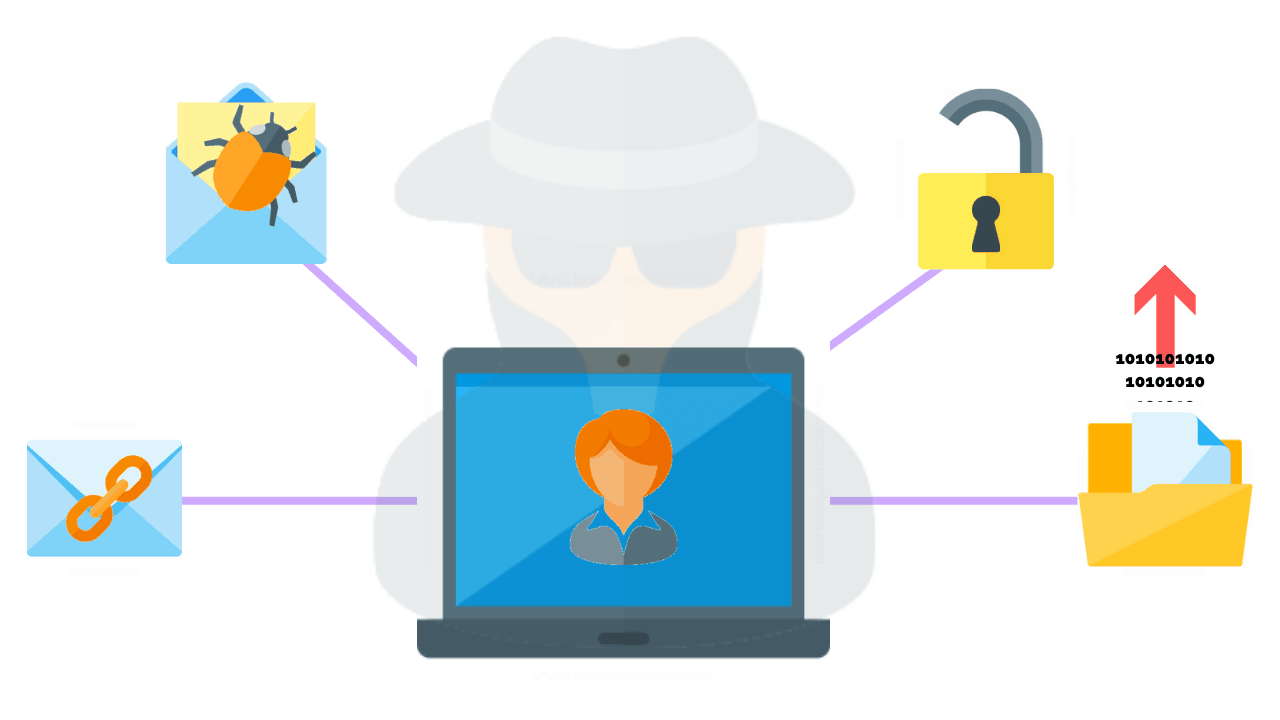
Social Engineering Techniques in Web Penetration Testing
July 22, 2023
Importance of Secure Session Management in Web Applications
July 22, 2023

Biometric Authentication: Security Challenges in Web Applications
July 21, 2023

Zero-Day Vulnerabilities: Web Application Exploitation
June 21, 2023
Websockets Security: Threats and Countermeasures
July 20, 2023

OAuth Security: Risks and Recommendations for Web Developers
July 19, 2023

Clickjacking Attacks: Techniques and Mitigation
July 19, 2023

Web Caching Attacks: Techniques and Countermeasures
July 18, 2023
Insecure Direct Object References (IDOR): Exploitation and Prevention
July 17, 2023

Security Headers for Web Applications: Best Practices
July 17, 2023
Server-Side Template Injection (SSTI): Exploitation Techniques
July 15, 2023
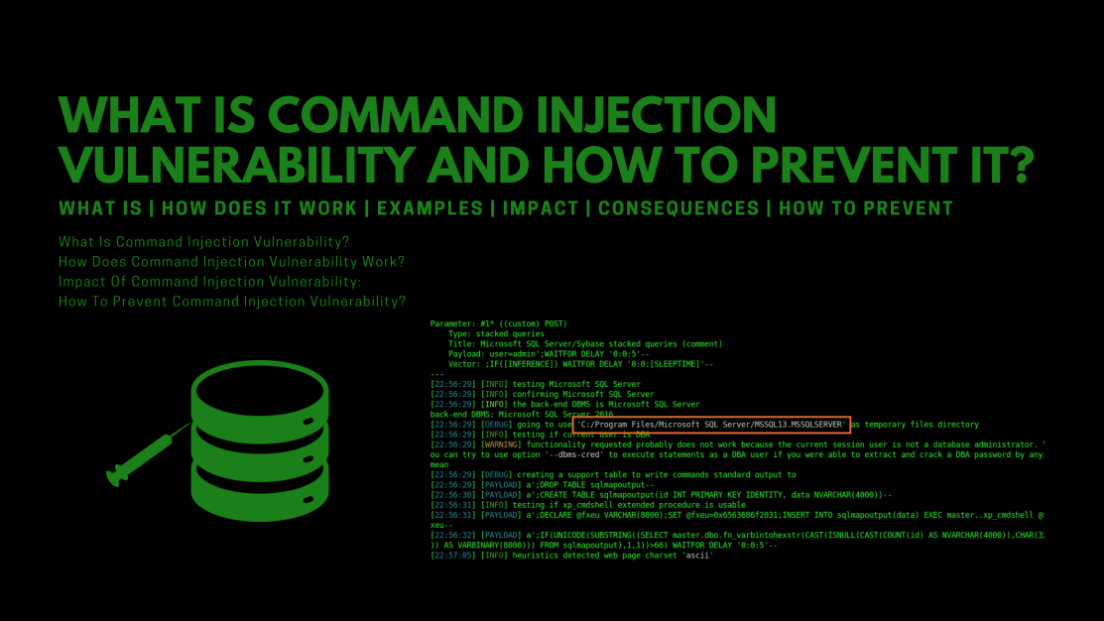
Exploiting Command Injection Vulnerabilities in Web Applications
July 15, 2023

Anatomy of a Web Penetration Test: Step-by-Step Process
July 14, 2023
Vulnerability Assessment vs. Penetration Testing: What's the Difference?
July 13, 2023

Hacking WordPress: Vulnerabilities and Countermeasures
July 13, 2023

Web Application Security Scanning Tools: A Comparative Analysis
July 12, 2023
API Security Testing: Best Practices and Tools
July 12, 2023
Remote File Inclusion (RFI) and Local File Inclusion (LFI) Attacks
July 11, 2023

XML External Entity (XXE) Attacks
July 11, 2023

Exploiting File Upload Vulnerabilities in Web Applications
July 10, 2023
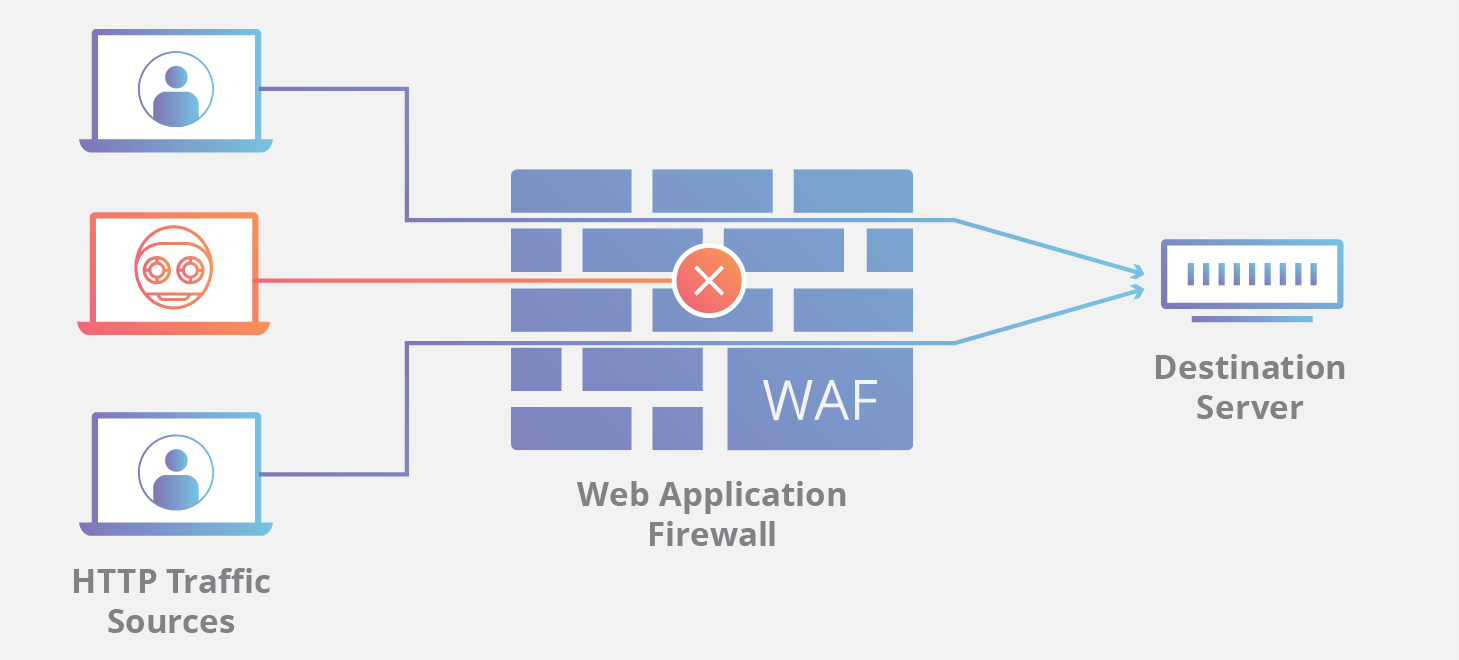
Web Application Firewalls (WAFs): How They Work and Their Limitations
July 8, 2023

What is security misconfiguration in OWASP?
July 7, 2023

Directory Traversal Attack Case Study
July 7, 2023
What is a cross-site scripting (XSS) attack? What is the purpose of attackers?
July 5, 2023
Penetration Testing and Reporting Results Effectively
May 12, 2023
Assessing the Security of Cloud Environments
May 13, 2023

Collecting Volatile Data and Identifying Attack Patterns through Forensic Analysis
May 15, 2023

Comparative Analysis: TikTok in China vs. TikTok in the USA
May 16, 2023

US Government Data Breach Exposes Personal Information of Employees
May 17, 2023

PharMerica Data Breach Impacts 5.8 Million Patients
May 18, 2023

Everything to Know About the ChatGPT Data Leak
May 19, 2023

Atlassian Data Breach: What You Need to Know
May 20, 2023

Activision Data Breach
May 20, 2023
T-Mobile Data Breach Exposes Personal Information
May 22, 2023

PayPal Data Breach: What You Need to Know
May 22, 2023

Apria Healthcare Data Breach
May 25, 2023

Shein Data Breach: What You Need to Know
May 31, 2023

Common Web Application Vulnerabilities and Exploits
July 4, 2023

Best ways to learn web penetration testing, ethical hacking, and IT security
July 4, 2023

Cryptocurrency Security: Best Practices for Safeguarding Your Digital Assets
July 3, 2023

Meta Platforms Inc. Announces Possible Data Breach
June 2, 2023

Network Penetration Testing For Weaknesses
May 11, 2023

The Future of Ransomware
May 11, 2023

LastPass Hack: Understanding the Risks and Protecting Your Passwords
May 10, 2023

Understanding The Dark Web And Its Role In Cybercrime
May 9, 2023

Best Practices For Securing Your Remote Workforce
May 9, 2023

Top Cybersecurity threats facing businesses in 2023
May 9, 2023

The Equifax Data Breach: Implications for Consumer Privacy and Security
May 6, 2023

Cybersecurity in the Post-COVID World: Lessons Learned and Future Predictions
May 6, 2023

Role of AI in Cybersecurity: Opportunities & Challenges
May 5, 2023

Major Data Breach in India Exposes COVID-19 Vaccination Data
June 14, 2023

North Face Data Breach: What You Need to Know
June 3, 2023

Uber Data Breach Exposes Driver and Passenger Data
June 5, 2023

CyberSecurity Breach Exposes Contact and Bank Details of BA, BBC, and Boots Customers
June 7, 2023

The Importance of Data Privacy Regulations: GDPR, CCPA, and Their Impact
June 20, 2023
The Role of Security Orchestration, Automation, and Response in Cyber Defense
June 21, 2023

The Most Common Cybersecurity Mistakes
June 27, 2023

Cybersecurity Careers: Exploring the Path to a Lucrative and In-Demand Field
July 1, 2023

Cybersecurity Compliance 101: Understanding Regulations and Standards
July 1, 2023

How to Protect Your Data in the Cloud
June 26, 2023

The Best Password Managers for 2023
June 23, 2023

Understanding Different Web Application Security Testing Techniques
June 5, 2023

Advantages And Disadvantages Of Penetration Testing
June 6, 2023

What Technique is Used To Automate The Detection Of Web Application Vulnerabilities
May 30, 2023
Web Penetration Testing In Agile Development Environments
May 31, 2023

Threat Modelling For Web Penetration Testing: Assessing Risks And Impact
June 1, 2023

Does Penetration Testing Have A Future, Looking It As A Career In 2023
June 7, 2023

How Can We Automate Penetration Testing In Order To Improve Network Security
June 2, 2023

What Priority Is Looking For Security Vulnerabilities In The Packages And Libraries?
June 3, 2023

What Type Of Web Application Vulnerabilities Are Humans Typically Better At Discovering
June 9, 2023

Nelnet Servicing Breach Exposes Data of 2.5 Million Student Loan Accounts
June 10, 2023
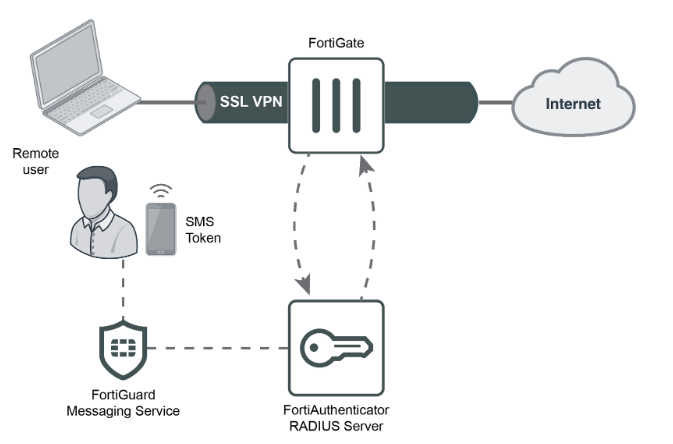
Fortinet FortiGate SSL VPN Alert
June 12, 2023

North Korean Hackers Breach Hospital in Seoul, Threatening Data Security
June 13, 2023

Securing Cloud-Native Applications: Considerations and Best Practices
June 13, 2023
Exploring Quantum Cryptography: The Future of Unbreakable Encryption
June 14, 2023

Securing the Internet of Medical Things (IoMT)
June 17, 2023

Exploring Cybersecurity Frameworks: NIST, ISO 27001, and Beyond
June 16, 2023